Risk Scoring
This article details how risk scoring works in the Brinqa Platform, how Brinqa calculates risk scores out-of-the-box, and how changes can be made to customize these calculations.
What is risk scoring?
Risk scoring in the Brinqa Platform is designed to provide you and your organization with a clear and actionable understanding of your security risk landscape. Before diving into the details, let's define some key terms:
-
Base risk score: The initial score assigned to a vulnerability, typically derived from standardized scoring systems such as Common Vulnerability Scoring System (CVSS) v3 or CVSS v2. This score reflects the inherent risk of a vulnerability without considering any additional risk factors or context.
-
Risk score: A calculated score that takes the base risk score and adjusts it by considering additional risk factors specific to your organization or environment, such as asset criticality, business impact, and threat intelligence. This score provides a more accurate assessment of the actual risk posed by a vulnerability in your specific context.
-
Risk rating: A qualitative representation of the risk score, usually expressed as a category like Low, Medium, High, or Critical. Risk ratings provide a more accessible and easily understandable view of the risk associated with a vulnerability, making it easier to prioritize remediation efforts.
The risk score model is a configuration that determines the calculation of base risk scores, risk scores, and risk ratings for vulnerabilities that fulfill the specified conditions of the risk scoring model. By using multiple scoring models and offering customization options, Brinqa enables you to prioritize vulnerabilities and assets based on your organization's unique risk profiles. The risk scoring model configuration encompasses the attribute that will be used as the basis for the risk score, whether the base risk score will be adjusted by risk factors, and the name of each numerical range.
Risk scoring model for vulnerabilities
It's important to note that in the Brinqa Platform, vulnerabilities refer to specific instances of security weaknesses in your assets, whereas vulnerability definitions describe the general characteristics of a vulnerability, including details like CVSS v3 or CVSS v2 scores.
Brinqa calculates risk scores for vulnerability definitions by first identifying the most appropriate risk scoring model for each item, based on the available data. Brinqa prioritizes these models in the following order: CVSS v3, CVSS v2, Severity number, and then Default value. Brinqa then aggregates and normalizes the risk scores across all findings by applying a consistent numbering format, from 0-10, providing a comprehensive view of your organization's risk landscape. This process enables you and your security teams to prioritize remediation efforts and make informed decisions about risk mitigation strategies.
Brinqa also calculates risk scores for vulnerabilities by first determining if there is a vulnerability definition associated with them. If an associated vulnerability definition is available, Brinqa uses that risk score; if not, it uses the default value instead. In both cases, Brinqa then takes into account any related risk factors, which may increase or decrease the base risk score. This approach ensures that risk scores for vulnerabilities are accurately assessed, depending on the presence of vulnerability definitions and applicable risk factors.
Vulnerability definition risk scoring models
By default, there are five risk scoring models that Brinqa applies to calculate risk scores for vulnerability definitions:
-
CVSS v3
CVSS v3 is an industry-standard method for assessing the severity of vulnerabilities. It takes into account various factors such as exploitability, impact, and scope. Brinqa uses CVSSv3 scores provided by vulnerability databases or security scanners, which typically range from 0-10, with 10 indicating the highest risk, to assess the risk of specific findings.
-
CVSS v2
CVSS v2 is the previous version of the CVSS framework. While it has been largely superseded by CVSS v3, Brinqa continues to support it for backward compatibility. Like CVSS v3, CVSS v2 scores from 0-10 and are used to assess the risk of specific findings. If CVSS v3 scores are not available for a vulnerability, Brinqa can use CVSS v2 scores as a fallback.
-
Severity score
The severity score is a simplified risk scoring model that categorizes vulnerabilities into different levels based on their severity. Brinqa calculates the severity score by normalizing a tool's severities or ratings to a scale of 0 to 10, particularly when a tool doesn't support CVSS v3 or CVSS v2 scores but provides its own severity ratings. By mapping the tools' severity levels to the 0-10 rating scale, Brinqa allows for a consistent assessment of risk across different tools and vulnerability findings.
-
Riskiest
The riskiest model calculates the risk score for vulnerabilities by using the associated CVE risk score, excluding additional risk factors. This model provides a straightforward evaluation by focusing solely on the raw CVE risk score, making it suitable for vulnerabilities that are linked to CVEs.
-
Default value
The default value is a fallback risk scoring model that Brinqa uses when no other scoring information is available for a finding. This model assigns a predefined default risk score to ensure that all findings have a risk score, even if they lack CVSS or severity data. You can customize default values to fit your organization's risk management requirements.
Figure 1 illustrates this risk scoring process:
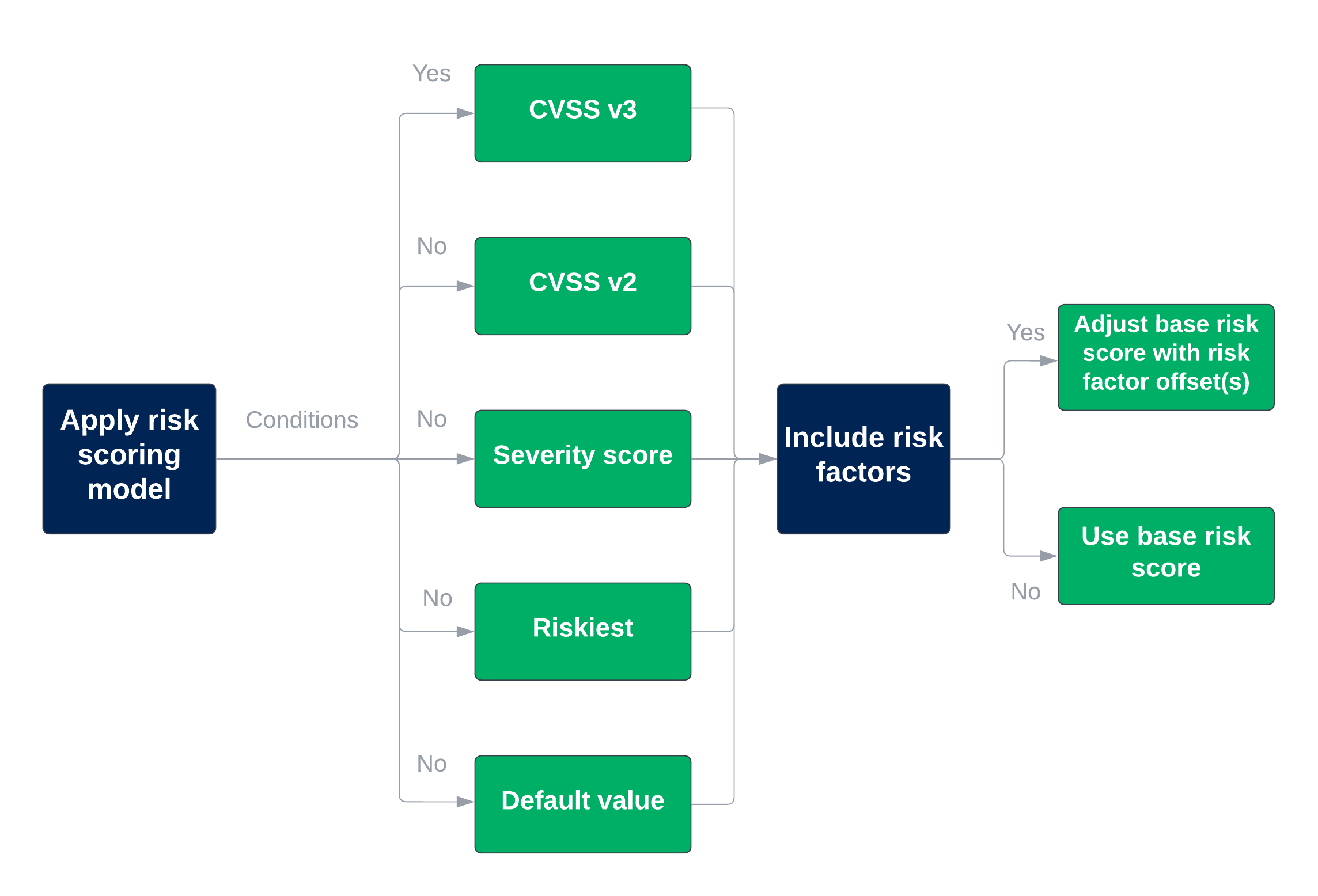
Figure 1. Vulnerability definition risk scoring process
Users with the Configurator or System Administrator role can access the pre-defined risk scoring model categories for vulnerability definitions by navigating to Administration > Data > Models > Vulnerability definition > Risk scoring. The default risk scoring models are detailed in the table below:
Table 1: Brinqa built-in vulnerability definition risk scoring models
| Order | Name | Description | Condition |
|---|---|---|---|
| 1 | Finding definition CVSSv4 (CVSS-B) without risk factors | The risk scoring model for Finding Definitions that have a CVSS v4 base score. The risk score is derived from the cvssV4BaseScore attribute. This model is deactivated by default. Support for CVSS v4 scores was added in platform version 11.33. Brinqa recommends activating this model only after thorough testing to verify its compatibility with your organization's risk scoring requirements. To help you assess the impact, two dashboards are available: "CVE Record CVSS Coverage" and "Finding Definition CVSS Coverage". These dashboards show the distribution of CVSS versions across your vulnerability data. When activated, CVSS v4 base scores take precedence over CVSS v3 base scores. | cvssV4BaseScore IS NOT NULL |
| 2 | Finding definition CVSSv3 without risk factors | The default risk scoring model for Finding Definitions that have a CVSS v3 base score. The risk score is derived from the cvssV3BaseScore attribute. | cvssV3BaseScore IS NOT NULL |
| 3 | Finding definition CVSSv2 without risk factors | The default risk scoring model for Finding Definitions that have a CVSS v2 base score. The risk score is derived from the cvssV2BaseScore attribute. | cvssV2BaseScore IS NOT NULL |
| 4 | Finding definition severity score without risk factors | The default risk scoring model for Finding Definitions that have a severity number. The risk score is derived from the severityScore attribute | severityScore IS NOT NULL |
| 5 | Finding definition riskiest associated CVE risk score without risk factors | The default risk scoring model for Finding Definitions that have associated CVEs. The risk score is derived from the riskScore attribute. | cveRecords.riskScore > 0 |
| 6 | Finding definition default base risk score to 0 without risk factors | The default risk scoring model for Finding Definitions that do not have a CVSS base score or severity number. | true |
Vulnerability risk scoring models
By default, there are two risk models that Brinqa applies to calculate risk scores for vulnerabilities:
-
Findings with associated definitions and risk factors
This risk scoring model calculates vulnerability risk scores based on the corresponding vulnerability definition's risk score, which includes CVSS v3 or v2 scores. It takes into account both the characteristics of the vulnerability and any related risk factors. If a vulnerability has an associated definition, this model assigns the risk score from the definition to the vulnerability, ensuring a comprehensive and accurate risk assessment for each individual vulnerability.
-
Default value with risk factors
This risk scoring model is designed for findings that have no CVSS or severity information. In the absence of an industry-standard scoring system like CVSS or a defined severity, this model incorporates any relevant risk factors to assess the risk of specific findings. This ensures that even findings without CVSS or severity scores are evaluated and prioritized appropriately, based on available risk factor data.
Figure 2 illustrates this risk scoring process:
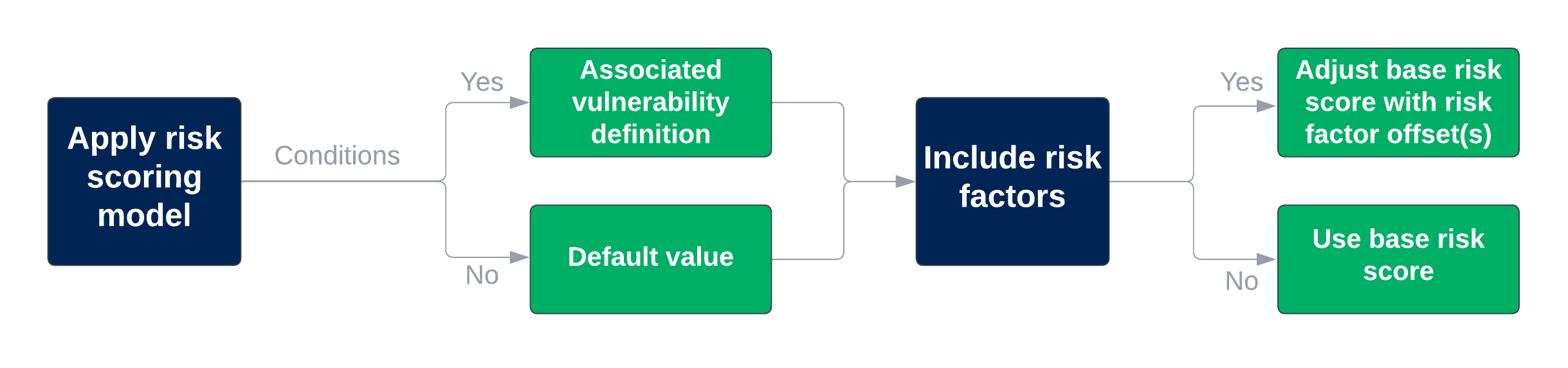
Figure 2. Vulnerability risk scoring process
Users with the Configurator or System Administrator role can access the pre-defined risk scoring model categories for vulnerabilities by navigating to Administration > Data > Models > Vulnerability > Risk scoring. The default risk scoring models are detailed in the table below:
Table 2: Brinqa built-in vulnerability risk scoring models
| Order | Name | Description | Condition |
|---|---|---|---|
| 1 | Finding highest associated active finding with risk factors | The default risk scoring model for findings based on the associated finding definition's risk score and related risk factors. | type IS NOT NULL |
| 2 | Finding default base risk score to 0 without risk factors | The default risk scoring model for findings that do not have a CVSS score or severity. | true |
Risk scoring model for assets
In the Brinqa Platform, assets are also assigned risk scores; however, the process differs from vulnerability risk scoring.
By default, the risk score assigned to assets is based on the risk score of their open vulnerabilities. If an asset has one or more open vulnerabilities, the highest risk score is assigned to the asset. This approach ensures that the asset's risk score accurately represents the most significant risk currently associated with it.
Assigning risk scores to assets based on their open vulnerabilities enables organizations to better understand the overall risk landscape of their infrastructure. This information helps security teams prioritize remediation efforts, allocate resources effectively, and implement risk mitigation strategies to reduce the potential impact of vulnerabilities on their assets.
Users with the Configurator or System Administrator role can access the pre-defined risk scoring model categories for assets by navigating to Administration > Data > Models > Host > Risk scoring. The default risk scoring model for assets is detailed in the table below:
Table 3: Brinqa built-in asset risk scoring model
| Name | Description | Condition |
|---|---|---|
| Asset highest associated active finding risk score without risk factors | The default asset risk scoring model is based on the highest risk score for associated active findings. | true |
The conditions for the asset risk scoring model apply to data models that extend the asset data model. The conditions for these data models are as follows:
-
Target data model: Host (or any data model that extends Asset)
-
Aggregation data model: Finding
-
Aggregation attribute: Risk score
-
Filter:
statusCategory = "open" -
Condition:
true(Note: This condition will always be true)
These conditions are used to compute the risk score for assets based on the open vulnerabilities associated with them. The risk scoring model first checks if the ID exists for each Host in the target data model, ensuring that the host exists. Then, for each existing host, it filters for findings with an "open" status category and identifies the highest risk score among them. This approach ensures that only relevant and active vulnerabilities are considered when calculating the asset's risk score.
Adjust risk score with risk factors
The risk scoring model defines which attributes act as the base risk score for the risk score computation. If the chosen risk scoring model has risk factors enabled, then the base risk score can be adjusted by the risk factors applied to that finding. Risk factors may either increase or decrease the base risk score.
Typically, if you rely solely on base scores, you may end up with many findings rated as high or critical. Risk factors are designed to lower the priority of findings in secure networks with little to no traffic, while elevating those that involve sensitive data or support critical business functions. CVSS scores provide information about the vulnerability itself, but they don't offer insights into the importance of the location where the vulnerability is found.
Users with the Configurator or System Administrator role can access the risk factor adjustments by navigating to Administration > Configuration > Risk factors. Brinqa provides default risk factor adjustments out-of-the-box, which can be enabled or disabled as needed. For additional information, see Built-in risk factors.
See risk factors for additional information about risk factors and how to create and apply risk factors to your security data.
The risk score of a finding equals the base risk score plus the sum of all risk factor scores on a scale of 0-10. For example, a risk factor score of -1 on the vulnerability data model decreases the risk score of the associated findings by 1.
To examine how risk factors impact the base risk score of a finding, navigate to Findings, click the Risk factors filter, and then select one or more risk factors from the dropdown. For example:
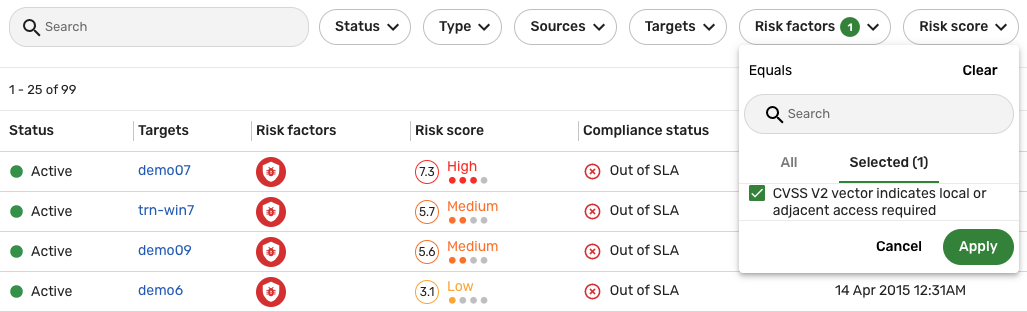
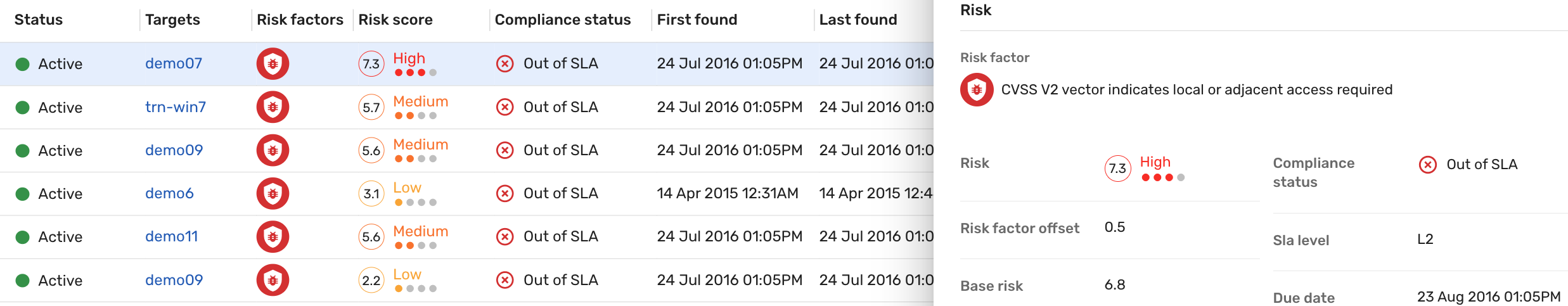
In the screenshot above, the CVSS v2 vector indicates local or adjacent access required risk factor has been applied and only the findings with that risk factor are displayed in the list view. Click one of the entries in the list view, and locate the Risk section in the slide-out view to see how the sum of the risk factors (Risk factor offset) affects the final risk score (Risk): it increases the base risk score (6.8) of the finding by 0.5, resulting in a final risk score of 7.3.
Create a new risk scoring model
To calculate risk, you must first determine the most suitable risk score model for the finding you are computing. If the default Brinqa risk scoring models do not quite fit your risk scoring and risk prioritization needs, users with the Configurator or System Administrator role can create a new risk scoring model. To do so, follow these steps:
-
Navigate to Administration > Configuration > Risk scoring models.
-
Click Create and fill in the fields as shown below:
-
Name: The name of the risk scoring model.
-
Active: Whether the risk scoring model is active or not.
-
Description: The description of the risk scoring model.
-
Preset: The different ways that the risk scoring model calculates the base risk score. Select one of the following:
-
Aggregate related attribute: Takes an aggregation (Maximum, Minimum, Mean, Median, Sum, or Standard deviation) of a dataset. You must select the Aggregation attribute when specifying the conditions. The attribute must be of either the Number or Calculated (Number) type.
-
Value from attribute: Uses the value of an attribute on any dataset or related data. You must select the Preset attribute when specifying the conditions. The attribute must be of either the Number or Calculated (Number) type.
-
Default value: Specify a number as the default.
-
-
Conditions: Specify the condition to score your data. The supported syntax is Brinqa Condition Language. For example:
cvssV2BaseScore IS NOT NULL, orpatchAvailable = "False". -
Test condition: Click Test condition to see the results retrieved by the condition.
Click + to add additional conditions to the risk scoring model.
-
-
Click Create.
-
Locate the new risk scoring model and click Edit.
-
In the Risk levels section, fill in the following information:
-
Name: The name of the risk level.
-
From and To: The range of preset attribute values for the risk level. For example, if you choose Risk rating as the preset attribute, you can set the Low risk level to span from 0 to 3. This range is inclusive, which means that risk ratings from 0 to 3, which include 0 and 3, belong in the Low risk level.
The following screenshot illustrates an example of risk levels with corresponding ranges defined for a new risk scoring model.
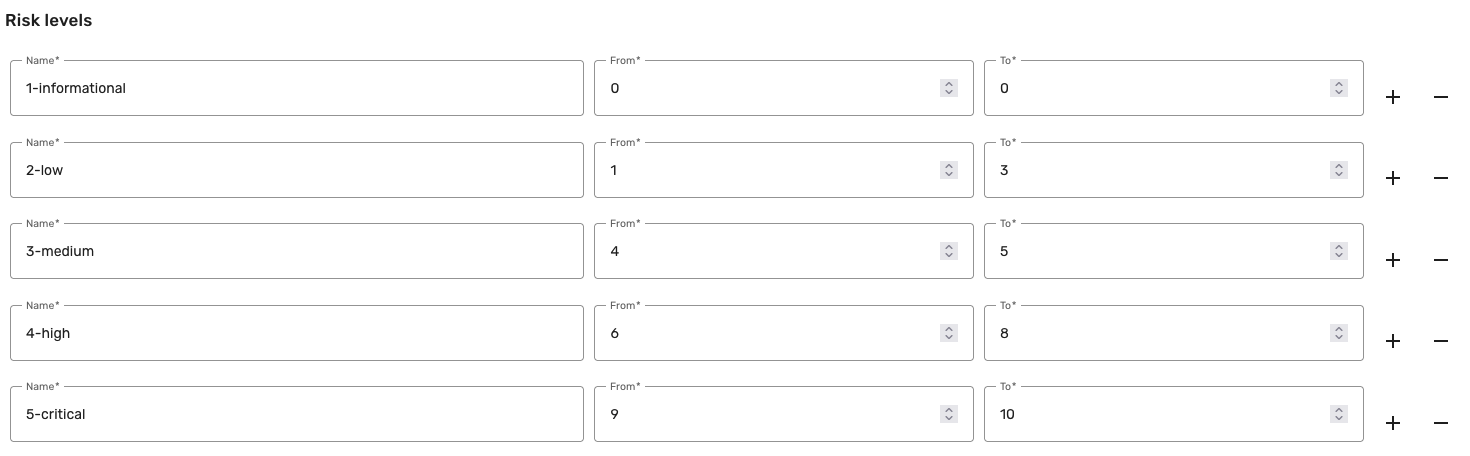
-
-
Click + to add another risk level or - to delete a risk level.
-
Select Active. Inactive risk scoring models are effectively archived.
-
Click Update.
Clone an existing risk scoring model
Rather than creating a new risk scoring model from scratch, you can clone a built-in one and modify it to better fit your needs. Cloning not only allows you to keep the built-in risk scoring model intact but also ensures that your modifications won't be overwritten during release updates. This way, you get a duplicated version to tailor as you like without unintentionally altering important default settings.
-
Navigate to Administration
> Configuration > Risk scoring models.
-
Hold the pointer over the risk scoring model that you want to modify and click Clone.
-
Make any necessary changes.
noteFor each target data model included in the cloned risk scoring model, you must modify the Order attribute. Failing to do so results in an error message when you attempt to create the clone.
The Order attribute signifies the sequence in which the Brinqa Platform evaluates the conditions specified for the target data model. Therefore, the same data model cannot share the same order in both the built-in and cloned risk scoring models.
-
Select Active to activate the cloned risk scoring model, and then click Create.
The page reloads, and the cloned risk scoring model displays in the list view.
noteIf the cloned risk scoring model's conditions include multiple target data models, your changes apply to all of them. For instance, if you clone a risk scoring model that applies to the Open source finding, Pentest finding, and Violation data models, the cloned risk scoring model displays on the respective data model pages.
-
Hold the pointer over the cloned risk scoring model and click Edit.
-
Revise the risk levels as needed and click Save.
Activate or deactivate a risk scoring model
If you want to activate a risk scoring model, whether built-in or cloned, do the following:
-
Hold the pointer over the risk scoring model in the list view.
-
Click Activate.
If you want to deactivate a risk scoring model, whether built-in or cloned, do the following:
-
Hold the pointer over the risk scoring model in the list view.
-
Click Deactivate.
This prevents any overlapping conditions from being applied twice.
Launch risk scoring models
Your new risk scoring model applies when the data orchestration runs. However, if you want the new risk scoring model to go into effect immediately, follow these steps:
-
Navigate to the data model to which the risk scoring model applies.
-
Click Flows.
-
Click the compute flow for your data model. For example, if you have added a new risk scoring model for the Vulnerability data model, click Vulnerability compute flow.
-
Click Launch.
Repeat these steps for each target data model you've selected during the risk scoring model creation process.