User Access Management
In the Brinqa Platform, user access management involves the procedure of creating user accounts and granting them permissions to view assets, findings, or tickets. It ensures that users have the right level of access needed to perform their roles effectively while also maintaining security and compliance.
Brinqa offers two different approaches for provisioning user accounts: individual creation and just-in-time (JIT) creation. The following table summarizes the similarities and differences between the two options:
| Procedure | Option 1 Individual User Creation | Option 2 JIT User Creation |
|---|---|---|
| Pre-configuration | None | [Manual] Customer sets role and ownership attributes in their SAML provider. |
| User creation | [Manual] Customer creates users one by one from the Brinqa UI. | [Automatic] Upon first login, Brinqa retrieves permissions from the SAML claim and creates the user accounts. |
| Role assignment | [Manual] Customer assigns roles when creating the users. | [Automatic] Brinqa automatically assigns roles based on the SAML claim. |
| Access Control | [Manual] Customer places users into ownership clusters. | [Automatic] Based on the information provided in the SAML claim, Brinqa uses a condition to automatically assign the users to ownership clusters. |
Individual user provisioning
The process of individual user provisioning begins with deciding the level of access a user needs within the Brinqa Platform. If limited access is necessary, this user must be assigned the Risk analyst role and added to the appropriate ownership cluster as a member. For full access to the Brinqa Platform, you can assign the System administrator role to the user. The following diagram illustrates this process.
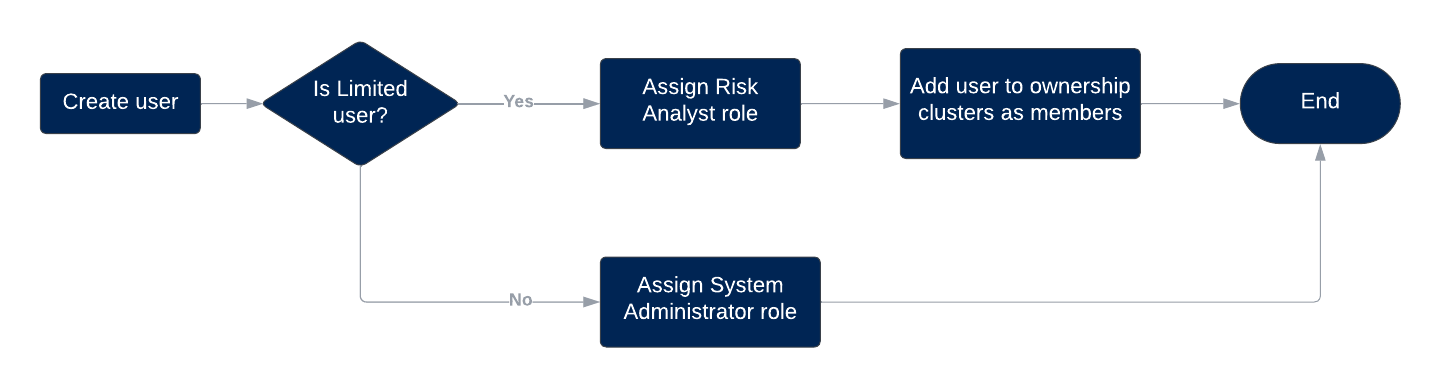
Figure 1. Individual user access provisioning process
For detailed step-by-step instructions on configuring this process in the Brinqa Platform, refer to the documentation on individual user provisioning.
JIT user provisioning
Customers who have established secure access to the Brinqa Platform through single sign-on (SSO) can leverage the user and user group information contained in the Security Assertion Markup Language (SAML) claims. In other words, during their first login, relevant roles are assigned to the users based on the SAML claim, and then the users are added to the relevant ownership clusters, also based on the SAML claim. The following diagram illustrates this process.
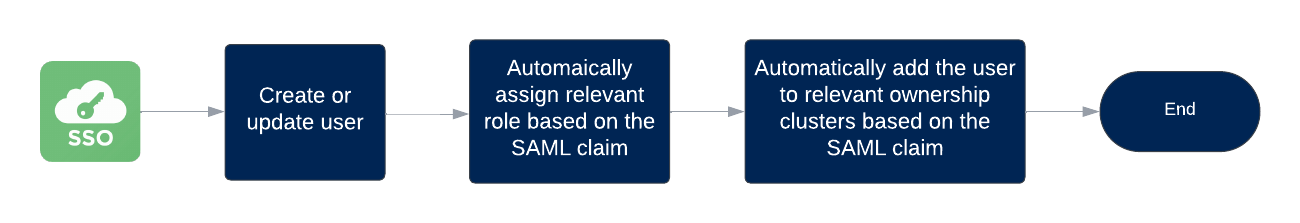
Figure 2. JIT user access provisioning process
Depending on the identifier provider (IdP) of your SSO solution, see instructions for configuring JIT provisioning through Microsoft Entra ID (formerly known as Azure Active Directory) or Okta.