Qualys Vulnerability Management
Qualys Vulnerability Management (VM) is a vulnerability scanning tool that scans hosts and generates vulnerabilities against those hosts. You can bring these findings into Brinqa to construct a unified view of your attack surface and strengthen your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Qualys Vulnerability Management and how to obtain that information from Qualys. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Qualys Vulnerability Management from the Connector drop-down. If you cannot find the connector in the drop-down, make sure that you have installed it first. You must provide the following information to authenticate Qualys Vulnerability Management with Brinqa:
-
API Server URL: The Qualys API Server URL. For information on how to determine your Qualys API URL, see Qualys documentation.
-
Username and Password: The username and password associated with the Qualys user, which must have permissions to log in to the API server and return data.
Create a Qualys user
To ensure the user account that the Qualys VM connector uses to access the Qualys server has the appropriate permissions, follow these steps.
-
Log in to your organization's Qualys server.
-
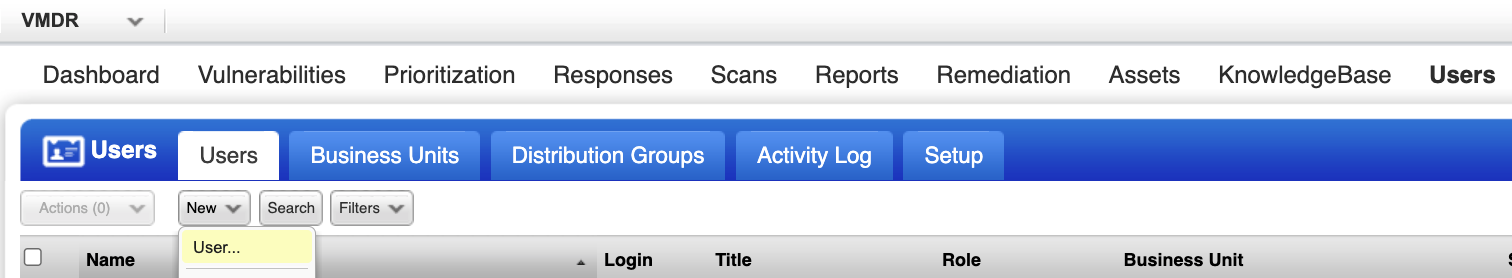
Navigate to Users, and then select the Users tab.
-
Click New and select User. The New User dialog displays.
-
Fill out the general information for the new user.
-
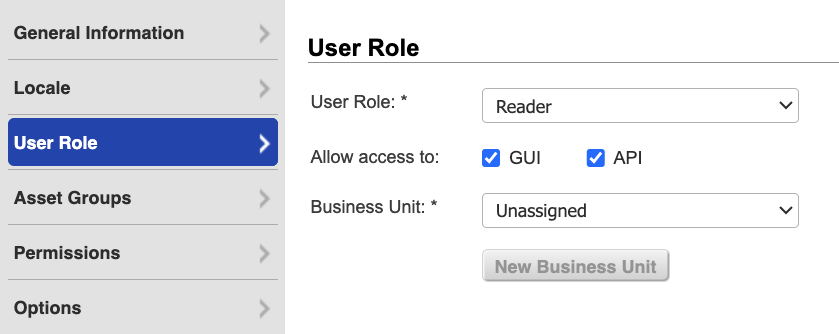
Click User Role on the left menu.
-
From the User Role drop-down, select Reader.
-
Select GUI and API to enable API access, and leave Business Unit Unassigned.
noteGUI access allows the user to log in to the Qualys GUI (graphical user interface). After you create the new Qualys user, log in to the Qualys GUI using the new credentials. The system prompts the user to reset their password. The Qualys connector will not function until you complete the password reset.
-
-
Click Asset Groups.
- From the Add asset groups drop-down, select All or only the asset groups the Qualys user needs access to.
-
Click Permissions and select all of the available permissions.
-
Click Options to modify the notification options as needed.
-
Click Save.
The new Qualys user with appropriate permissions to retrieve data displays on the Qualys Users page.
If you do not wish to create a new Qualys user, you can leverage an existing user with the appropriate permissions.
If you do not have permissions to create a new Qualys user, contact your Qualys administrator. For additional information, see Qualys documentation.
Enable CVSS scoring in Qualys
To ensure that the Qualys VM connector accurately retrieves CVSS scoring information, including Temporal Scores, from your Qualys environment, you must enable a specific setting in Qualys. This setting is not enabled by default. To enable this setting, follow these steps:
-
Log in to your organization's Qualys server.
-
Navigate to Vulnerability Management > Reports.
-
Click the Setup tab and then click CVSS.
The CVSS Setup window displays.
-
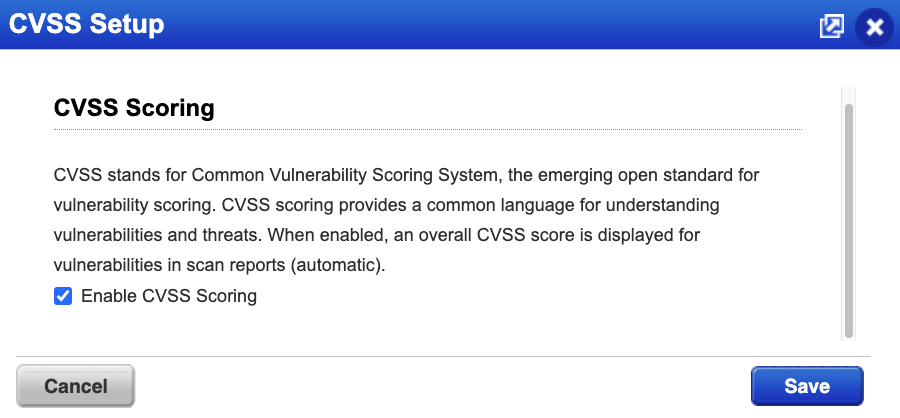
Click Enable CVSS Scoring and then click Save.
Additional settings
The Qualys Vulnerability Management connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 2.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the Qualys API before giving up and reporting a failure. The default setting is 5.
-
Request timeout (secs): The maximum time allotted, in seconds, before a request times out. The default setting is 120 seconds. Although it is not recommended, you can also enter zero (0) to disable timeouts.
Types of data to retrieve
The Qualys Vulnerability Management connector can retrieve the following types of data from the Qualys API:
Table 1: Data retrieved from Qualys
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Host | Yes | Host |
| Vulnerability | Yes | Vulnerability |
| Vulnerability Definition | Yes | Vulnerability Definition |
For detailed steps on how to view the data retrieved from Qualys VM in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Host
Table 2: Host attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| accountId | Local variable |
| availability zone | Local variable |
| categories/asset category | categories |
| first discovered | firstSeen |
| getName | name |
| host.getAGENTACTIVATIONKEY | Local variable |
| host.getAGENTACTIVATIONTITLE | Local variable |
| host.getAGENTSTATUS | Local variable |
| host.getARSFACTORS.getARSFORMULA | Local variable |
| host.getASSETCRITICALITYSCORE | Local variable |
| host.getASSETRISKSCORE | Local variable |
| host.getASSETID | Local variable |
| host.getCLOUDAGENTRUNNINGON | Local variable |
| host.getCLOUDPROVIDER | Local variable |
| host.getCLOUDPROVIDERTAGS | Local variable |
| host.getCLOUDRESOURCEID | instanceId |
| host.getCLOUDSERVICE | Local variable |
| host.getDNSDATA.getDOMAIN | Local variable |
| host.getDNSDATA.getFQDN | publicDnsNames, privateDnsNames |
| host.getHARDWAREUUID | Local variable |
| host.getID | uid |
| host.getIP | publicIpAddresses |
| host.getLASTVMAUTHSCANNEDDATE | Local variable |
| host.getLASTVULNSCANDATETIME | lastScanned, lastSeen |
| host.getNETBIOS | hostnames |
| host.getOS | description |
| host.getOWNER | Local variable |
| host.getQGHOSTID | Local variable |
| host.getTRACKINGMETHOD | Local variable |
| host.getTRURISKSCORE | Local variable |
| host.getTRURISKSCOREFACTORS().getTRURISKSCOREFORMULA | Local variable |
| host.getASSETCRITICALITYSCORE | Local variable |
| host.getARSFACTORS.getARSFORMULA | Local variable |
| hostnames | hostnames |
| host.getCLOUDPROVIDERTAGS | Local variable |
| host.getOS | description |
| host.getNETBIOS | hostname |
| host.getDNSDATA.getDOMAIN | domain |
| host.getLASTVMAUTHSCANNEDDATE | lastAuthScanned |
| host.getARSFACTORS.getARSFORMULA | arsFormula |
| host.getDNSDATA.getDOMAIN | domain |
| host.getOS | operatingSystem |
| host.getDNSDATA.getDOMAIN | domain |
| instance id | instanceId |
| instance state | status |
| instance type | Local variable |
| ipv6 | Local variable |
| location | Local variable |
| local hostname | privateDnsNames |
| mac | Local variable |
| name | Local variable |
| network | Local variable |
| os type | Local variable |
| port | Local variable |
| private ip | Local variable |
| private ipv4 | Local variable |
| project id | Local variable |
| protocol | Local variable |
| public hostname | publicDnsNames |
| public ip | Local variable |
| public ipv4 | publicIpAddresses |
| region | Local variable |
| resource group name | Local variable |
| scan type | Local variable |
| security group | Local variable |
| state | status |
| subnet | Local variable |
| subscription id | Local variable |
| target | Local variable |
| type | Local variable |
| uuid | uid |
| vm id | instanceId |
| zone | Local variable |
Vulnerability
Table 3: Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| detection.getAFFECTEXPLOITABLECONFIG | Local variable |
| detection.getAFFECTRUNNINGKERNEL | Local variable |
| detection.getAFFECTRUNNINGSERVICE | Local variable |
| detection.getFIRSTFOUNDDATETIME | firstFound |
| detection.getFIRSTREOPENEDDATETIME | Local variable |
| detection.getLASTFIXEDDATETIME | lastFixed |
| detection.getLASTFOUNDDATETIME | lastFound |
| detection.getLASTREOPENEDDATETIME | Local variable |
| detection.getLASTTESTDATETIME | lastScanned |
| detection.getLASTUPDATEDATETIME | sourceLastModified |
| detection.getLATESTVULNERABILITYDETECTIONSOURCE | Local variable |
| detection.getRESULTS | results |
| detection.getSTATUS | status |
| detection.getTIMESFOUND | timesFound |
| detection.getTIMESREOPENED | Local variable |
| detection.getTYPE | Local variable |
| detection.getVULNERABILITYDETECTIONSOURCES | Local variable |
| host.getDNS | publicDnsNames |
| host.getID | targets |
| host.getIP | ipAddresses |
| host.getNETBIOS | hostnames |
| host.getQGHOSTID | Local variable |
| is disabled | Local variable |
| is ignored | Local variable |
| mac address | macAddresses |
| port | port |
| protocol | protocol |
| severity | severity |
| service | service |
| ssl | Local variable |
| status category | statusCategory |
| type | type |
| uid | uid |
Vulnerability Definition
Table 4: Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| cvssv2.getAttackComplexity | cvssV2AccessComplexity |
| cvssv2.getAvailability | cvssV2AvailabilityImpact |
| cvssv2.getAuthentication | cvssV2Authentication |
| cvssv2.getAttackVector | cvssV2AttackVector |
| cvssv2.getConfidentiality | cvssV2ConfidentialityImpact |
| cvssv2.getExploitability | cvssV2Exploitability |
| cvssv2.getIntegrity | cvssV2IntegrityImpact |
| cvssv2.getReportConfidence | cvssV2ReportConfidence |
| cvssv2.getRemediationLevel | cvssV2RemediationLevel |
| cvssv2.getSeverity | cvssV2Severity |
| cvssv3.getAttackComplexity | cvssV3AccessComplexity |
| cvssv3.getAvailability | cvssV3AvailabilityImpact |
| cvssv3.getAttackVector | cvssV3AttackVector |
| cvssv3.getConfidentiality | cvssV3ConfidentialityImpact |
| cvssv3.getExploitability | cvssV3ExploitCodeMaturity |
| cvssv3.getIntegrity | cvssV3IntegrityImpact |
| cvssv3.getPrivilegesRequired | cvssV3PrivilegesRequired |
| cvssv3.getReportConfidence | cvssV3ReportConfidence |
| cvssv3.getRemediationLevel | cvssV3RemediationLevel |
| cvssv3.getUserInteraction | cvssV3UserInteraction |
| discovery.getREMOTE | Local variable |
| getAffectedSoftware.vuln.getSOFTWARELIST | affected |
| getBugTracIds.vuln.getBUGTRAQLIST | Local variable |
| getComplianceTypes.vuln.getCOMPLIANCELIST | Local variable |
| getDiscoveryAuthTypes(discovery.getAUTHTYPELIST | Local variable |
| getExploits.vuln.getCORRELATION | exploits |
| getMalwares.vuln.getCORRELATION | malware |
| getPCIReasons.vuln.getPCIREASONS | Local variable |
| getThreatIndicators.vuln.getTHREATINTELLIGENCE | Local variable |
| getVendorReferences.vuln.getVENDORREFERENCELIST | references |
| uid | uid |
| vuln.getCATEGORY | categories |
| vuln.getCVSS.getBASE | cvssV2BaseScore, cvssV3BaseScore |
| vuln.getCVSS.getTEMPORAL | cvssV2TemporalScore, cvssV3TemporalScore |
| vuln.getCVSS.getVECTORSTRING | cvssV2Vector, cvssV3Vector |
| vuln.getCONSEQUENCE | summary |
| vuln.getDIAGNOSIS | description |
| vuln.getLASTSERVICEMODIFICATIONDATETIME | sourceLastModified |
| vuln.getPATCHABLE | patchAvailable |
| vuln.getPUBLISHEDDATETIME | publishedDate |
| vuln.getSEVERITYLEVEL | severity, severityScore, sourceSeverity |
| vuln.getSOLUTION | recommendation |
| vuln.getTITLE | name |
| vuln.getVULNTYPE | Local variable |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the Qualys VM connector:
Table 5: Qualys VM DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Host | LAST_SCANNED NOT IN LAST 30 Days | 30 days after inactivity | Uses the LAST_SCANNED attribute to identify hosts that are inactive within the last 30 days, and then purges the records after 30 days of inactivity. |
| Vulnerability | Inactivity is delegated to the Host object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated host, and then purges the records after 30 days of inactivity. |
Operation options
The Qualys VM connector supports the following operation options. See connector operation options for information about how to apply them.
Expand the sections below to view the supported operation options for each connector object:
Host
Table 6: Host operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Host | host_metadata | all, azure, ec2, google | Retrieve host metadata for all cloud providers (Azure, EC2, Google) or only the specified cloud providers. | Key: host_metadata Value: all. This key and value combination retrieves metadata for hosts from all your cloud providers. |
| ips | Any IP addresses or ranges | You can use this option to retrieve specific hosts from Qualys by the specified IP addresses. You can use either a comma-separated list or specify a range with a dash. | Key: ips Value: 10.10.10.1-10.10.10.100. This key and value combination only retrieves hosts associated with the specified range of IP addresses. |
For additional information on on the supported operation options and parameters, see Qualys documentation.
Vulnerability
Table 7: Vulnerability operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Vulnerability | arf_filter_keys | non-running-kernel, non-running-service, config-not-exploitable | You can use this option to filter vulnerabilities based on advanced runtime conditions. This option is only applied if arf_key is set to true. | Key: arf_filter_keys Value: non-running-kernel,non-running-service. This key and value combination retrieves vulnerabilities for the specified ARF conditions. |
| arf_kernel_filter | 0, 1, 2, 3, 4 | You can use this option to filter vulnerabilities on Linux kernels. For additional information, see Qualys documentation. | Key: arf_kernel_filter Value: 3. This key and value combination only retrieves exploitable kernel related vulnerabilities. | |
| arf_key | true, false | You can use this option to enable advanced ARF filtering. When set to true, you can apply the arf_filter_keys and show_arf_data filters. | Key: arf_key Value: true. This key and value combination enables advanced ARF filtering options. | |
| ids | Any valid host ID or range | You can use this option to filter vulnerabilities by specific host IDs or ranges. Multiple host IDs or ranges can be specified as a comma-separated list. Specify a host ID range using a hyphen (for example: 190-400). For additional information, see Qualys documentation. | Key: ids Value: 123,200-250. This key and value combination retrieves vulnerabilities for the specified host IDs or ranges. | |
| ips | Any valid IP address or range | You can use this option to filter vulnerabilities by specific IP addresses or ranges. Multiple IP addresses or ranges can be specified as a comma-separated list. Specify an IP range using a hyphen (for example: 10.10.10.1-10.10.10.100). For additional information, see Qualys documentation. | Key: ips Value: 10.10.10.1,10.10.10.5-10.10.10.10. This key and value combination retrieves vulnerabilities for the specified IP addresses or ranges. | |
| qds_max | Any Qualys Detection Score (QDS) value from 1–100 | You can use this option to filter vulnerabilities with a QDS value less than or equal to the specified value. For additional information on QDS scores, see Qualys documentation. | Key: qds_max Value: 10. This key and value combination only retrieves vulnerabilities with a QDS value less than or equal to 10. | |
| qds_min | Any QDS value from 1–100 | You can use this option to filter vulnerabilities with a QDS value greater than or equal to the specified value. For additional information on QDS scores, see Qualys documentation. | Key: qds_min Value: 90. This key and value combination only retrieves vulnerabilities with a QDS value greater than or equal to 90. | |
| severities | 1, 2, 3, 4, 5 | You can use this option to filter vulnerabilities by their severity level. You can use a comma-separated list to retrieve multiple severity levels or a dash to retrieve a range of severity levels. For additional information on severity levels, see Qualys documentation. | Key: severities Value: 4,5. This key and value combination only retrieves vulnerabilities with a severity level of 4 or 5. | |
| show_arf_data | 0, 1 | You can use this option to show or hide tags for vulnerabilities affected by ARF conditions. This option is only applied if arf_key is set to true. | Key: show_arf_data Value: 1. This key and value combination displays ARF tags in vulnerability records. | |
| show_qds | 0, 1 | You can use this option to determine whether the QDS is displayed in the output for each vulnerability record. Specify 1 to show the QDS value for each detection record. Specify 0 if you do not want to show the QDS value. | Key: show_qds Value: 1. This key and value combination displays the QDS value for each vulnerability record. | |
| status | Active, Fixed, New, Re-Opened | You can use this option to filter vulnerabilities by their status. You can use a comma-separated list of statuses. For additional information, see Qualys documentation. | Key: status Value: Active,Re-Opened. This key and value combination only retrieves active and re-opened vulnerabilities. | |
| vuln_detection_source | 0, 1 | You can use this option to include detection source metadata in the retrieved vulnerabilities. Set to 1 to display detection source and latest detection source metadata. Set to 0 to omit them. The default value is 0. | Key: vuln_detection_source Value: 1. This key and value combination includes detection source metadata in the retrieved vulnerabilities. |
For additional information on on the supported operation options and parameters, see Qualys documentation.
The option keys and values are case-sensitive as they are shown in this documentation
APIs
The Qualys VM connector uses the Qualys VM API v3 and v4. Specifically, it uses the following endpoints:
Table 8: Qualys VM API Endpoints
| Connector Object | API Endpoint |
|---|---|
| Host | GET /api/4.0/fo/asset/host/ |
| Vulnerability | GET /api/4.0/fo/asset/host/ |
GET /api/4.0/fo/asset/host/vm/detection | |
| Vulnerability Definition | POST /api/3.0/fo/knowledge_base/vuln/ |
Changelog
The Qualys VM connector has undergone the following changes:
Table 9: Qualys VM connector changelog
| Version | Description |
|---|---|
| 5.3.19 | No change. |
| 5.3.18 | - The /vm/detection Vulnerability API endpoint has been updated to v4.0. - Added the DETECTION_GET_VULNERABILITY_DETECTION_SOURCES and DETECTION_GET_LATEST_VULNERABILITY_DETECTION_SOURCES attributes to the Vulnerability object. - Added a new operation option on the Vulnerability object to include detection source metadata in the retrieved vulnerabilities: vuln_detection_source. |
| 5.3.17 | Added the AGENT_ACTIVATION_KEY and AGENT_ACTIVATION_TITLE attributes to the Host object to support status configurations and data lifecycle management (DLM) policies. |
| 5.3.16 | No change. |
| 5.3.15 | No change. |
| 5.3.14 |
|
| 5.3.13 | No change. |
| 5.3.12 | No change. |
| 5.3.11 | No change. |
| 5.3.10 | No change. |
| 5.3.9 | Fixed the following data type mismatches:
|
| 5.3.8 | No change. |
| 5.3.7 | No change. |
| 5.3.6 | Fixed an issue where the Vulnerability Definition object sync was failing due to a NullPointerException error. |
| 5.3.5 | Added a new additional setting to help prevent sync failures due to default timeout limits: Request timeout. |
| 5.3.4 | Changed the ASSET_ID attribute type on the Host object from integer to string. |
| 5.3.3 | No change. |
| 5.3.2 | - Added support for Data lifecycle management to the Host and Vulnerability objects. - Added the following attributes to the Host object:
|
| 5.2.4 | Added the following attributes on the Host object so it can utilize the TruRisk attribute from Qualys:
|
| 5.2.3 | Added the following attributes on the Vulnerability object to retrieve the Qualys Detection Score:
|
| 5.2.2 | Changed the SOURCE_SEVERITY attribute on the Vulnerability Definition object to SOURCE_SEVERITY_SCORE. |
| 5.2.1 | Changed the SOURCE_SEVERITY attribute on the Vulnerability object to SOURCE_SEVERITY_SCORE. |
| 5.1.11 | Added the NETWORK_ID attribute on the Host object. |
| 5.1.10 | Updated dependencies. |
| 5.1.8 | Added asset risk score (ARS) related operation options such as ars_max, ars_min, show_ars, and show_ars_factors for the Host connector object. |
| 5.1.5 | Added checks for null Common Vulnerability Scoring System (CVSS) vectors. |
| 5.1.3 | Updated to trim trailing spaces from the CVE IDs present in certain vulnerability definitions. |
| 5.0.18 | Added the SEVERITY_SCORE attribute in the Vulnerability Definition object. |
| 5.0.14 | Added UID as identifier for all connector objects. |
| 5.0.13 | Replaced the CATEGORY attribute with CATEGORIES on the Vulnerability Definition object. |
| 5.0.12 | Replaced the CATEGORY`attribute with CATEGORIES on the Host object. |
| 5.0.10 | Stopped using IP_ADDRESS as identifier for hosts or vulnerabilities. |
| 5.0.4 | Replaced the Finding Definition object with Vulnerability Definition. |
| 5.0.0 | Initial Integration+ release. |