Qualys Container Security
Qualys Container Security (CS) is a container security tool that scans your container assets and generates data related to compliance, policies, and vulnerabilities. You can bring compliance details, container, control, exception, host, image, registry, vulnerability container, and vulnerability image data from Qualys CS into Brinqa to gain a unified view of your attack surface, thus strengthening your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Qualys CS and how to obtain that information from Qualys. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Qualys Container Security from the Connector dropdown. You must provide the following information to authenticate Qualys with Brinqa:
-
API Server URL: The Qualys platform API Server URL. The default URL format is
https://gateway.<POD>.apps.qualys.com/. For information on how to determine your Qualys API URL, see Qualys documentation. -
Username and Password: The user name and password associated with the Qualys user, which must have permissions to log in to the API server and return data.
Create a Qualys user
To ensure the user account that the Qualys CS connector uses to access the Qualys server has the appropriate permissions, follow these steps.
-
Log in to your organization's Qualys server.
-
Click the dropdown at the top of the page and under Utilities, select Administration.
-
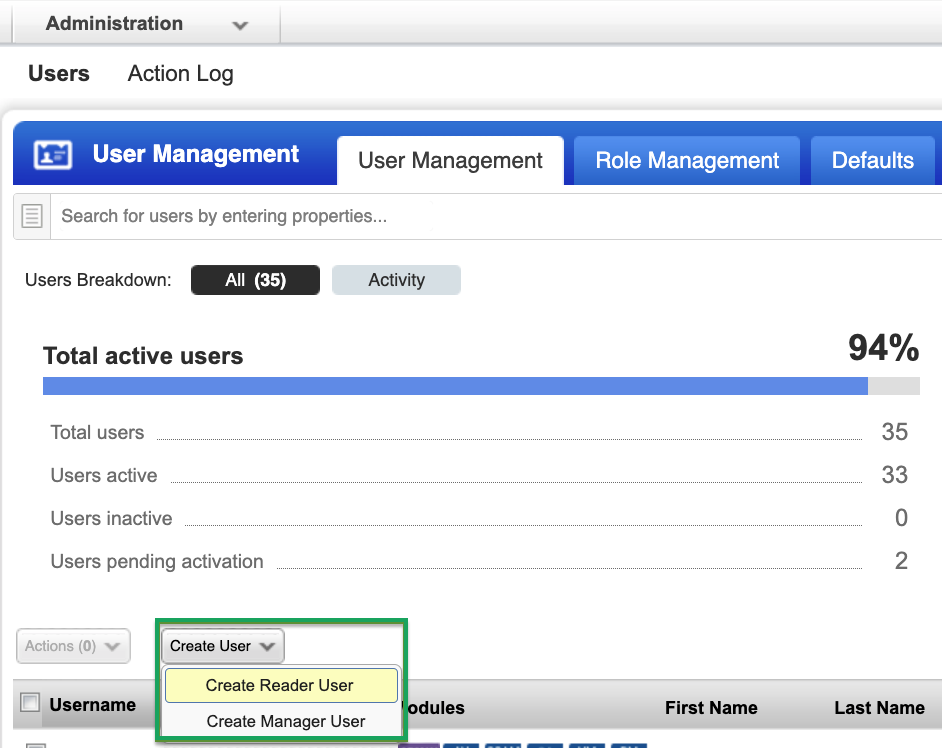
Navigate to Users, and then click the User Management tab.
-
Click the Create User dropdown and select Create Reader User.
-
Fill out the general information for the new user.
-
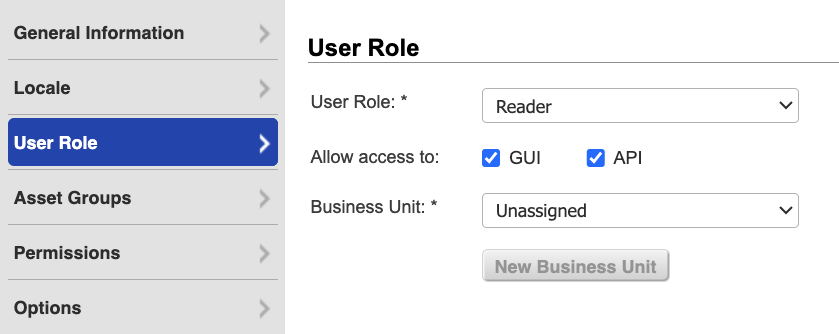
Click User Role on the left menu.
From the User Role dropdown, select Reader.
-
Select GUI and API to enable API access, and leave Business Unit Unassigned.
noteGUI access allows the user to log in to the Qualys GUI (graphical user interface). After you create the new Qualys user, log in to the Qualys GUI using the new credentials. The system prompts the user to reset their password. The Qualys connector will not function until you complete the password reset.
-
-
Click Asset Groups on the left menu.
- From the Add asset groups dropdown, select Add All or only the asset groups the Qualys user needs access to.
-
Click Permissions on the left menu and select all of the available permissions.
-
Click Options to modify the notification options as needed.
-
Click Save.
The new Qualys user with appropriate permissions to retrieve data displays on the Qualys Users page.
If you do not wish to create a new Qualys user, you can leverage an existing user with the appropriate permissions.
If you do not have permissions to create a new Qualys user, contact your Qualys administrator. For additional information, see Qualys documentation.
Additional settings
The Qualys CS connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 300. It is not recommended to go over 300.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 2.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the Qualys API before giving up and reporting a failure. The default setting is 5.
Types of data to retrieve
The Qualys CS connector can retrieve the following types of data from the Qualys API:
Table 1: Data retrieved from Qualys
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Compliance Details | Yes | Violation |
| Container | Yes | Container |
| Control | Yes | Violation Definition |
| Exception | No | Not mapped |
| Host | Yes | Host |
| Image | Yes | Container Image |
| Registry | No | Not mapped |
| Vulnerability Container | Yes | Vulnerability |
| Vulnerability Definition | ||
| Vulnerability Image | Yes | Vulnerability |
| Vulnerability Definition |
The Qualys CS connector does not currently support operation options for the types of data it retrieves.
For detailed steps on how to view the data retrieved from Qualys CS in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Compliance Details
Table 2: Compliance Details attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| controls.controlId | type |
| controls.criticality | Local variable |
| controls.datapoints_key | Local variable |
| controls.datapoints_value | Local variable |
| controls.lastEvaluated | lastAssessed |
| controls.policyUuid | Local variable |
| controls.posture | status |
| controls.statement | Local variable |
| controls.technologyId | Local variable |
| created | sourceCreatedDate |
| customerUuid | Local variable |
| lastComplianceScanned | lastScanned |
| sha | targets |
| updated | sourceLastModified |
| uuid | uid |
Container
Table 3: Container attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| compliance.errorCount | Local variable |
| compliance.failCount | Local variable |
| compliance.passCount | Local variable |
| containerId | Local variable |
| created | sourceCreatedDate |
| exceptions.assignmentType | Local variable |
| exceptions.uuid | target |
| host.hostname | hostnames |
| host.ipAddress | ipAddress (calculation) |
| host.lastUpdated | Local variable |
| host.sensorUuid | Local variable |
| host.uuid | targets |
| imageId | Local variable |
| imageUuid | image |
| isInstrumented | Local variable |
| isRoot | Local variable |
| lastComplianceScanDate | Local variable |
| lastVmScanDate | lastScanned |
| name | name |
| sha | Local variable |
| state | Local variable |
| stateChanged | Local variable |
| updated | sourceLastModified |
| uuid | uid |
| vulnerabilities.severity1Count | Local variable |
| vulnerabilities.severity2Count | Local variable |
| vulnerabilities.severity3Count | Local variable |
| vulnerabilities.severity4Count | Local variable |
| vulnerabilities.severity5Count | Local variable |
Control
Table 4: Control attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | categories |
| comments | description |
| criticality | Local variable |
| deprecated | Local variable |
| id | uid |
| isDeprecated | Local variable |
| statement | Local variable |
| subCategory | Local variable |
| technologies.id | Local variable |
| technologies.name | Local variable |
| technologies.rational | Local variable |
| technologies.remediation | solution |
Host
Table 5: Host attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| accountId | cloudAccountId |
| availability zone | Local variable |
| categories/asset category | categories |
| first discovered | firstSeen |
| getName | name,hostnames |
| host.getARSFACTORS.getARSFORMULA | Local variable |
| host.getASSETRISKSCORE | Local variable |
| host.getASSETCRITICALITYSCORE | Local variable |
| host.getASSETID | Local variable |
| host.getCLOUDPROVIDER | Local variable |
| host.getCLOUDPROVIDERTAGS | Local variable |
| host.getCLOUDRESOURCEID | instanceId, cloudResourceId |
| host.getCLOUDSERVICE | Local variable |
| host.getDNSDATA.getDOMAIN | domain |
| host.getDNSDATA.getFQDN | publicDnsName,privateDnsName |
| host.getID | uid |
| host.getIP | publicIpAddress |
| host.getLASTVMAUTHSCANNEDDATE | Local variable |
| host.getLASTVULNSCANDATETIME | lastScanned,lastSeen |
| host.getNAME | name |
| host.getNETBIOS | local variable |
| host.getOS | os |
| host.getOWNER | Local variable |
| host.getQGHOSTID | Local variable |
| host.getTAGS.getTAG | tags |
| host.getTRACKINGMETHOD | Local variable |
| imageId | image |
| instanceId | instanceId, local variable |
| instanceState | status (normalize) |
| instanceType | Local variable |
| ipv6 | Local variable |
| localHostname | privateDnsName |
| location | Local variable |
| mac | Local variable |
| macAddress | macAddresses |
| machineType | Local variable |
| name | Local variable |
| network | Local variable |
| os type | Local variable |
| private ip | Local variable |
| private ipv4 | Local variable |
| project id | Local variable |
| public hostname | publicDnsName |
| public ipv4 | publicIpAddress |
| region | Local variable |
| resource group name | Local variable |
| security group | Local variable |
| state | status (normalize) |
| subnet | Local variable |
| subscription id | Local variable |
| vm id | instanceId |
| zone | Local variable |
Image
Table 6: Image attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| associatedContainersCount | Local variable |
| associatedHostsCount | Local variable |
| compliance.errorCount | Local variable |
| compliance.failCount | Local variable |
| compliance.passCount | Local variable |
| created | sourceCreatedDate |
| exceptions | Local variable |
| imageId | Local variable |
| instrumentationState | Local variable |
| instrumentedFrom | Local variable |
| isDockerHubOfficial | Local variable |
| isInstrumented | Local variable |
| lastComplianceScanDate | Local variable |
| lastFoundOnHost.hostname | Local variable |
| lastFoundOnHost.ipAddress | Local variable |
| lastFoundOnHost.lastUpdated | Local variable |
| lastFoundOnHost.sensorUuid | Local variable |
| lastFoundOnHost.uuid | Local variable |
| lastVmScanDate | lastScanned |
| registryUuid | Local variable |
| repo.registry | registry |
| repo.repository | repository |
| repo.tag | tags |
| repoDigests.digest | digest |
| repoDigests.registry | Local variable |
| repoDigests.repository | Local variable |
| scanErrorCode | Local variable |
| scanStatus | Local variable |
| scanType | Local variable |
| scanTypes | Local variable |
| sha | Local variable |
| size | Local variable |
| source | Local variable |
| updated | sourceLastModified |
| uuid | uid |
| vulnerabilities.severity1Count | Local variable |
| vulnerabilities.severity2Count | Local variable |
| vulnerabilities.severity3Count | Local variable |
| vulnerabilities.severity4Count | Local variable |
| vulnerabilities.severity5Count | Local variable |
Vulnerability Container
Table 7: Vulnerability Container attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| authType | Local variable |
| category | categories |
| ContainerSha | target |
| cveids | type/uid |
| cvss3Info.baseScore | cvssV3BaseScore |
| cvss3Info.temporalScore | cvssV3TemporalScore |
| cvssInfo.accessVector | cvssV2Vector |
| cvssInfo.baseScore | cvssV2BaseScore |
| cvssInfo.temporalScore | cvssV2TemporalScore |
| discoveryType | Local variable |
| firstFound | firstFound |
| lastFound | lastFound |
| patchAvailable | patchAvailable |
| port | port |
| product | affected |
| published | publishedDate |
| qid | uid |
| result | results |
| risk | Local variable |
| scanType | Local variable |
| severity | severity, sourceSeverity, severityScore |
| software.fixVersion | Local variable |
| software.name | Local variable |
| software.packagePath | Local variable |
| software.scanType | Local variable |
| software.version | Local variable |
| software.vulnerabilities | Local variable |
| status | status(normalized), sourceStatus, statusCategory |
| supportedBy | Local variable |
| threatIntel.activeAttacks | Local variable |
| threatIntel.denialOfService | Local variable |
| threatIntel.easyExploit | Local variable |
| threatIntel.exploitKit | Local variable |
| threatIntel.exploitKitNames | Local variable |
| threatIntel.highDataLoss | Local variable |
| threatIntel.highLateralMovement | Local variable |
| threatIntel.malware | malware |
| threatIntel.malwareNames | Local variable |
| threatIntel.noPatch | Local variable |
| threatIntel.publicExploit | Local variable |
| threatIntel.publicExploitNames | Local variable |
| threatIntel.zeroDay | zeroDay |
| title | jobTitle |
| typeDetected | Local variable |
| vendor | Local variable |
| vulnerability | Local variable |
Vulnerability Image
Table 8: Vulnerability Image attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| authType | Local variable |
| category | statusCategory |
| cveids | type, uid |
| cvss3Info.baseScore | cvssV3BaseScore |
| cvss3Info.temporalScore | cvssV3TemporalScore |
| cvssInfo.accessVector | cvssV2Vector |
| cvssInfo.baseScore | cvssV2BaseScore |
| cvssInfo.temporalScore | cvssV2TemporalScore |
| discoveryType | Local variable |
| firstFound | firstFound |
| ImageSha | target |
| lastFound | lastFound |
| patchAvailable | patchAvailable |
| port | port |
| product | affected |
| published | publishedDate |
| qid | uid |
| result | results |
| risk | Local variable |
| scanType | Local variable |
| severity | severity, sourceSeverity, severityScore |
| software.fixVersion | Local variable |
| software.name | Local variable |
| software.packagePath | Local variable |
| software.scanType | Local variable |
| software.version | Local variable |
| software.vulnerabilities | Local variable |
| status | status(normalized), sourceStatus, statusCategory |
| supportedBy | Local variable |
| threatIntel.activeAttacks | Local variable |
| threatIntel.denialOfService | Local variable |
| threatIntel.easyExploit | Local variable |
| threatIntel.exploitKit | Local variable |
| threatIntel.exploitKitNames | Local variable |
| threatIntel.highDataLoss | Local variable |
| threatIntel.highLateralMovement | Local variable |
| threatIntel.malware | malware |
| threatIntel.malwareNames | Local variable |
| threatIntel.noPatch | Local variable |
| threatIntel.publicExploit | Local variable |
| threatIntel.publicExploitNames | Local variable |
| threatIntel.zeroDay | zeroDay |
| title | jobTitle |
| typeDetected | Local variable |
| vendor | Local variable |
| vulnerability | Local variable |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
APIs
The Qualys CS connector uses the Qualys Container Security REST API v1.3. However, for Host data, the connector uses an endpoint from the Qualys Asset Management v2 API. Specifically, it uses the following endpoints:
Table 9: Qualys CS API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Compliance Details | GET /csapi/v1.3/images/{imageSha}/compliance |
| Container | GET /csapi/v1.3/containers |
| Control | GET /csapi/v1.3/controls |
| Exception | GET /csapi/v1.3/exception |
| Host | GET /rest/2.0/search/am/asset (from Qualys Asset Management v2 API) |
| Image | GET /csapi/v1.3/images |
| Registry | GET /csapi/v1.3/registry |
| Vulnerability Container | GET /csapi/v1.3/containers |
GET /csapi/v1.3/containers/{containerSha}/vuln | |
GET /csapi/v1.3/images | |
GET /csapi/v1.3/images/{imageSha}/vuln | |
| Vulnerability Image | GET /csapi/v1.3/containers |
GET /csapi/v1.3/containers/{containerSha}/vuln | |
GET /csapi/v1.3/images | |
GET /csapi/v1.3/images/{imageSha}/vuln |
Changelog
The Qualys CS connector has undergone the following changes:
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
Table 10: Qualys CS connector changelog
| Version | Description | Date Published |
|---|---|---|
| 5.3.30 | No change. | February 3rd, 2026 |
| 5.3.29 | No change. | January 26th, 2026 |
| 5.3.28 | No change. | December 26th, 2025 |
| 5.3.27 | No change. | November 25th, 2025 |
| 5.3.26 | No change. | November 19th, 2025 |
| 5.3.25 | No change. | October 30th, 2025 |
| 5.3.24 | No change. | September 9th, 2025 |
| 5.3.23 | No change. | August 15th, 2025 |
| 5.3.22 | No change. | August 5th, 2025 |
| 5.3.21 | No change. | August 5th, 2025 |
| 5.3.20 | No change. | July 11th, 2025 |
| 5.3.19 | No change. | July 2nd, 2025 |
| 5.3.18 | No change. | June 30th, 2025 |
| 5.3.17 | No change. | May 7th, 2025 |
| 5.3.16 | No change. | April 23rd, 2025 |
| 5.3.15 | No change. | April 8th, 2025 |
| 5.3.14 | No change. | March 26th, 2025 |
| 5.3.13 | No change. | March 12th, 2025 |
| 5.3.12 | No change. | March 3rd, 2025 |
| 5.3.11 | Fixed an issue where updating to v5.3.10 of the connector resulted in duplicating the HOSTNAMES attribute. | February 28th, 2025 |
| 5.3.10 | No change. | January 29th, 2025 |
| 5.3.9 | No change. | December 30th, 2024 |
| 5.3.8 | No change. | November 14th, 2024 |
| 5.3.7 | No change. | November 12th, 2024 |
| 5.3.6 | No change. | November 7th, 2024 |
| 5.3.5 | No change. | October 21st, 2024 |
| 5.3.4 | No change. | September 23rd, 2024 |
| 5.3.3 | - Changed the following attribute types on the Vulnerability Image object from string to integer:
| September 20th, 2024 |
| 5.3.2 | No change. | August 23rd, 2024 |
| 5.3.1 | No change. | August 15th, 2024 |
| 5.3.0 | Initial Integration+ release. | August 12th, 2024 |