Microsoft Azure Compute
Microsoft Azure Compute is a suite of cloud computing services that provide a wide range of infrastructure and tools for running various types of applications and services. You can bring virtual machine data from Azure Compute into Brinqa to gain a comprehensive view of your hosts, allowing you to identify and address potential vulnerabilities on those assets, thus strengthening your overall cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Azure Compute and how to obtain that information from Microsoft. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Microsoft Azure Compute from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Azure Compute with Brinqa:
-
Client ID and Client secret: The client ID and client secret associated with the service principal, which must have permissions to log in to the Microsoft Azure Active Directory (Active AD) and return data from the Azure Compute API.
-
Tenant ID: The unique identifier for the Active AD tenant associated with the service principal.
Register a Microsoft Azure Application
You must create a new application for the Microsoft Azure Compute connector to authenticate with Azure AD and access the Azure Compute API. To register an application in your Azure AD tenant, follow these steps:
-
Log in to your organization's Microsoft Azure Portal as an administrator.
-
Navigate to and click Microsoft Entra ID.
-
On the left-hand side of the page, click App registrations, and then click New registration.
-
Give your new application a name, select the supported account types, and provide an optional Redirect URI. If you do not have a redirect URI, you can leave the field as is.
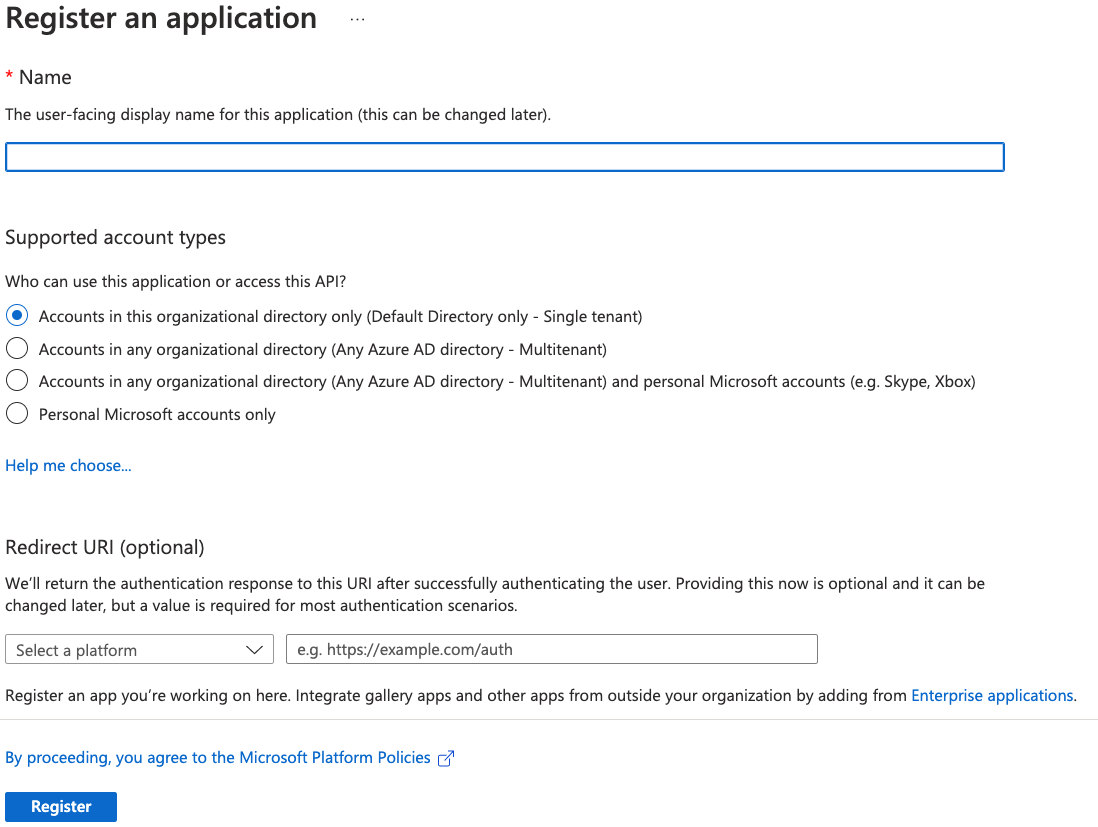
-
Click Register.
For additional details about registering an application in Azure AD and creating a service principal, see Microsoft documentation.
Obtain Microsoft Azure credentials
After you have created your new Microsoft Azure application, your client and tenant ID display. Copy the Application (client) ID and Directory (tenant) ID as shown below:
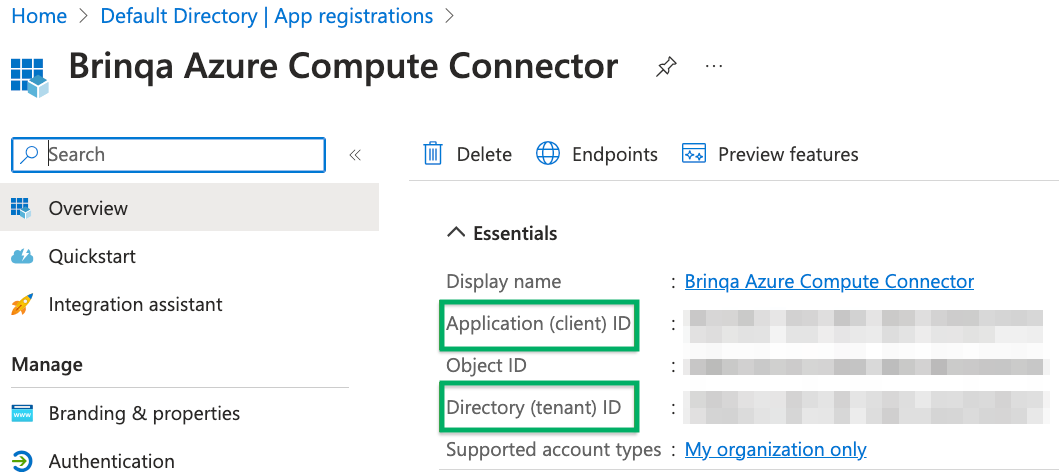
To obtain your client secret, follow these steps:
-
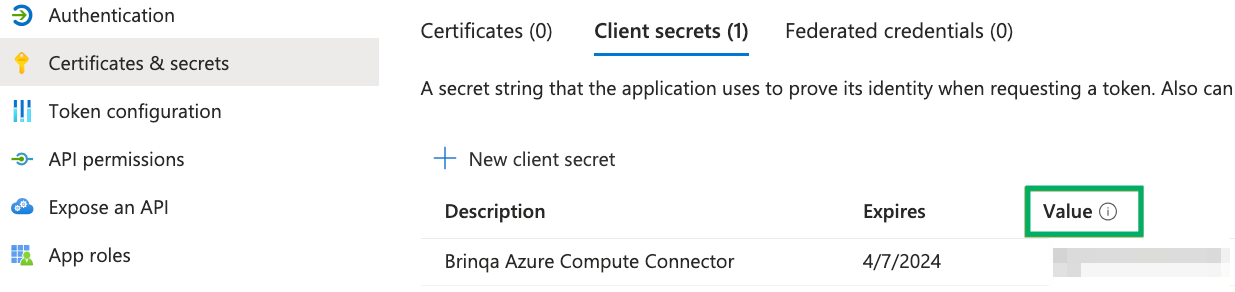
Click Certificates & secrets and then click New client secret.
-
Provide a description, set an expiry date, and then click Add.
The new client secret displays. You cannot view the client secret again. There is both a Value and Secret ID. The Value field is needed for authentication. Copy the Value field and save it to a secure location.
For additional details about obtaining your Microsoft Azure credentials, see Microsoft documentation.
Assign permissions
After you have created your new Microsoft Azure application and obtained the authentication credentials, you must assign the required permissions for the application to access your data. To do so, follow these steps:
-
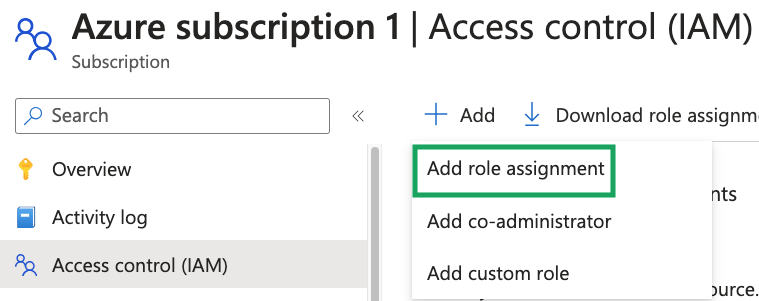
Navigate to the applicable Azure subscription.
-
Click Access control (IAM), click Add, and then click Add role assignment from the dropdown.
-
In the Job function roles tab, select the Virtual Machine Contributor role.
-
Click Next.
-
In the Members tab, click the User, group, or service principal option.
-
Click Select members, search for and click the application you registered earlier, and then click Select.
-
Navigate to the Review + assign tab and click Review + assign.
If you do not have permissions to assign roles, contact your Azure administrator. For additional information, see Microsoft documentation.
(Optional) Create a management group for multiple subscriptions
If you have multiple Azure subscriptions, you can organize them into a single management group to uniformly set access controls. To do so, follow these steps:
-
Log in to your Microsoft Azure Portal as an administrator.
-
Search for "Management groups" in the search box and click Management groups.
-
Click Create, provide a management group ID and display name, and then click Submit.
-
On the Management groups page, click the name of the new management group.
-
Click Add subscription, select the Azure subscriptions you want to add to the management group, and then click Save.
-
Click Access control (IAM), click Add, and then click Add role assignment from the dropdown.
-
Search for and select the role you want to assign to the management group.
-
Click Next.
-
In the Members tab, click the User, group, or service principal option.
-
Click Select members, search for and click the application you registered earlier, or any relevant members who require this role, and then click Select.
-
Navigate to the Review + assign tab and click Review + assign.
If you do not have permissions to create management groups, contact your Azure administrator. For additional information, see Microsoft documentation.
Additional settings
The Microsoft Azure Compute connector contains an additional option for specific configuration:
- Subscription ID: A comma-separated list of unique identifiers for your Microsoft Azure subscriptions, which represents a billing and resource usage entity within Azure. If no subscription ID is provided, the connector retrieves all subscriptions for the tenant.
To obtain your subscription ID, follow these steps:
-
Log in to your organization's Microsoft Azure Portal as an administrator.
-
Search for "Subscriptions" in the search box at the top of the page and click Subscriptions.
The subscription IDs for your corresponding applications display. If desired, copy these values into the Subscription ID field in the integration configuration.
Azure Subscription IDsOnly provide a Subscription ID if you want to retrieve resources from specific subscriptions. Leave this field blank to retrieve data from all subscriptions.
Types of data to retrieve
The Microsoft Azure Compute connector can retrieve the following types of data from the Azure Compute API:
Table 1: Data retrieved from Azure Compute API
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Virtual Machine | Yes | Host |
The Microsoft Azure compute connector does not currently support operation options for the types of data it retrieves.
For detailed steps on how to view the data retrieved from Azure Compute in the Brinqa Platform, see How to view your data.
Microsoft Azure Compute SDKs
The Microsoft Azure Compute connector uses the Microsoft Azure Compute SDK. Specifically, it uses the following classes:
Table 2: Microsoft Azure Compute SDK Classes
| Azure SDK Class | Description |
|---|---|
com.azure.core.http.rest.PagedIterable | Manages iterable responses for Azure service requests. |
com.azure.core.management.exception.ManagementException | Handles exceptions specific to Azure resource management operations. |
com.azure.resourcemanager.compute.models.InstanceViewStatus | Provides status details for compute instances. |
com.azure.resourcemanager.compute.models.VirtualMachineAgentInstanceView | Contains information about the Azure VM Agent instance view. |
com.azure.resourcemanager.compute.models.VirtualMachineInstanceView | Provides instance view details for Azure virtual machines. |
com.azure.resourcemanager.network.models.NetworkInterface | Manages Azure network interface components. |
Changelog
The Microsoft Azure Compute connector has undergone the following changes:
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
Table 3: Microsoft Azure Compute connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.4.29 | No change. | February 23rd, 2026 |
| 3.4.28 | No change. | February 4th, 2026 |
| 3.4.27 | No change. | January 26th, 2026 |
| 3.4.26 | No change. | November 17th, 2025 |
| 3.4.25 | No change. | November 17th, 2025 |
| 3.4.24 | No change. | November 10th, 2025 |
| 3.4.23 | No change. | October 23rd, 2025 |
| 3.4.22 | No change. | October 16th, 2025 |
| 3.4.21 | No change. | October 15th, 2025 |
| 3.4.20 | No change. | September 17th, 2025 |
| 3.4.19 | The Azure Compute connector has been renamed to "Microsoft Azure Compute". This change only affects the connector label and does not impact functionality. You can update without making any changes to your existing configurations. | August 5th, 2025 |
| 3.4.18 | No change. | August 4th, 2025 |
| 3.4.17 | No change. | August 1st, 2025 |
| 3.4.16 | No change. | June 11th, 2025 |
| 3.4.15 | No change. | May 27th, 2025 |
| 3.4.14 | No change. | May 21st, 2025 |
| 3.4.13 | No change. | May 20th, 2025 |
| 3.4.12 | No change. | April 22nd, 2025 |
| 3.4.11 | No change. | April 7th, 2025 |
| 3.4.10 | No change. | April 1st, 2025 |
| 3.4.9 | No change. | March 26th, 2025 |
| 3.4.8 | No change. | February 12th, 2025 |
| 3.4.7 | No change. | January 28th, 2025 |
| 3.4.5 | No change. | December 19th, 2024 |
| 3.4.4 | No change. | December 6th, 2024 |
| 3.4.3 | No change. | November 28th, 2024 |
| 3.4.2 | No change. | October 7th, 2024 |
| 3.4.1 | No change. | September 27th, 2024 |
| 3.4.0 | Made the Subscription ID optional in the integration configuration. Before updating to version 3.4.0, ensure that if you do not specify any subscription IDs, the connector retrieves data from all subscriptions. This may result in more data being brought in than expected. Specify subscription IDs if you want to limit data retrieval to only specific subscriptions. | September 17th, 2024 |
| 3.3.10 | No change. | September 4th, 2024 |
| 3.3.9 | No change. | August 27th, 2024 |
| 3.3.8 | No change. | July 24th, 2024 |
| 3.3.7 | No change. | July 24th, 2024 |
| 3.3.6 | No change. | July 8th, 2024 |
| 3.3.5 | No change. | May 20th, 2024 |
| 3.3.4 | No change. | May 20th, 2024 |
| 3.3.3 | No change. | May 20th, 2024 |
| 3.3.2 | No change. | May 9th, 2024 |
| 3.3.1 | No change. | May 3rd, 2024 |
| 3.3.0 | No change. | April 30th, 2024 |
| 3.2.2 | No change. | April 26th, 2024 |
| 3.2.1 | The "VM stopped" status now translates to "Active". | April 19th, 2024 |
| 3.2.0 | No change. | April 4th, 2024 |
| 3.1.18 | No change. | April 4th, 2024 |
| 3.1.17 | No change. | March 24th, 2024 |
| 3.1.16 | No change. | March 14th, 2024 |
| 3.1.15 | No change. | February 11th, 2024 |
| 3.1.14 | No change. | February 2nd, 2024 |
| 3.1.13 | No change. | January 26th, 2024 |
| 3.1.12 | No change. | January 24th, 2024 |
| 3.1.11 | No change. | October 11th, 2023 |
| 3.1.9 | No change. | July 20th, 2023 |
| 3.1.8 | No change. | July 19th, 2023 |
| 3.1.7 | No change. | May 18th, 2023 |
| 3.1.6 | Code cleanup and general maintenance. | May 9th, 2023 |
| 3.1.5 | Code cleanup and general maintenance. | May 8th, 2023 |
| 3.1.4 | Initial Integration+ release. | April 3rd, 2023 |