Qualys Policy Compliance
Qualys Policy Compliance (PC) is a compliance management tool that performs automated security configuration assessments on your IT systems. You can bring control, host, and violation data from Qualys into Brinqa to construct a unified view of your attack surface and strengthen your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Qualys PC and how to obtain that information from Qualys. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Qualys Policy Compliance from the Connector dropdown. You must provide the following information to authenticate Qualys with Brinqa:
-
API Server URL: The Qualys platform API Server URL. For information on how to determine your Qualys API URL, see Qualys documentation.
-
Username and Password: The user name and password associated with the Qualys user, which must have permissions to log in to the API server and return data.
Create a Qualys user
To ensure that the user account that the Qualys PC connector uses to access the Qualys API has the appropriate permissions, follow these steps.
-
Log in to your organization's Qualys server.
-
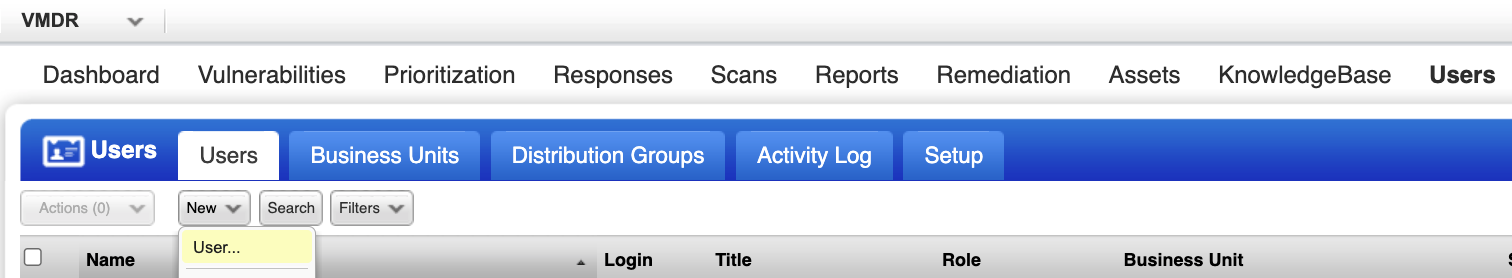
Navigate to Users, and then select the Users tab.
-
Click New and select User. The New User dialog displays.
-
Fill out the general information for the new user.
-
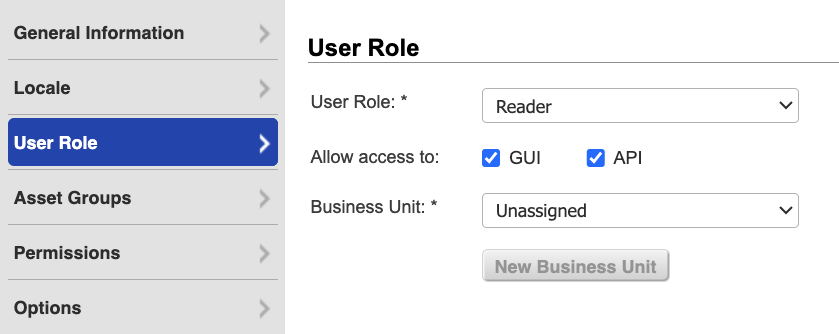
Click User Role on the left menu.
-
From the User Role dropdown, select Reader.
-
Select GUI and API to enable API access, and leave Business Unit as Unassigned.
noteGUI access allows the user to log in to the Qualys GUI (graphical user interface). After you create the new Qualys user, log in to the Qualys GUI using the new credentials. The system prompts the user to reset their password. The Qualys connector will not function until you complete the password reset.
-
-
Click Asset Groups.
- From the Add asset groups dropdown, select All or only the asset groups the Qualys user needs access to.
-
Click Permissions and select all of the available permissions.
-
Click Options to modify the notification options as needed.
-
Click Save.
The new Qualys user with appropriate permissions to retrieve data displays on the Qualys Users page.
If you do not wish to create a new Qualys user, you can leverage an existing user with the appropriate permissions.
If you do not have the permissions to create a Qualys user, contact your Qualys administrator. For additional information, see Qualys documentation on user roles and permissions.
Additional settings
The Qualys PC connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 2.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the Qualys API before giving up and reporting a failure. The default setting is 5.
Types of data to retrieve
The Qualys PC connector can retrieve the following types of data from the Qualys API:
Table 1: Data retrieved from Qualys
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Control | Yes | Violation Definition |
| Host | Yes | Host |
| Policy | No | Not mapped |
| Violation | Yes | Violation |
For detailed steps on how to view the data retrieved from Qualys PC in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Control
Table 2: Control attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORY | Local variable |
| CHECK_TYPE | Local variable |
| CREATED_DATE | sourceCreatedDate |
| CRITICALITY | severity, sourceSeverity, severityScore |
| FRAMEWORK_LIST (name) | Local variable |
| ID | uid |
| STATEMENT | Local variable |
| SUB_CATEGORY | Local variable |
| TECHNOLOGY_LIST (name) | Local variable |
| UPDATE_DATE | sourceLastModified |
Host
Table 3: Host attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ACCOUNT_ID | Local variable |
| AVAILABILITY_ZONE | Local variable |
| CATEGORIES_ASSET_CATEGORY | categories |
| FIRST_DISCOVERED | firstSeen |
| host.getASSETCRITICALITYSCORE | Local variable |
| host.getASSETRISKSCORE | Local variable |
| host.getASSETID | Local variable |
| host.getCLOUDPROVIDER | Local variable |
| host.getCLOUDPROVIDERTAGS | Local variable |
| host.getCLOUDRESOURCEID | cloudInstanceId |
| host.getCLOUDSERVICE | Local variable |
| host.getDNSDATA.getDOMAIN | Local variable |
| host.getDNSDATA.getFQDN | publicDnsName, privateDnsName |
| host.getIP | publicIpAddresses |
| host.getLASTVMAUTHSCANNEDDATE | Local variable |
| host.getLASTVULNSCANDATETIME | lastSeen |
| host.getNETBIOS | hostnames |
| host.getOS | Local variable |
| host.getOWNER | Local variable |
| host.getQGHOSTID | Local variable |
| host.getTAGS.getTAG | tags |
| host.getTRACKINGMETHOD | Local variable |
| host.getID | uid |
| HOSTNAME | Local variable |
| IMAGE_ID | Local variable |
| INSTANCE_ID | cloudInstanceId |
| INSTANCE_STATE | status |
| INSTANCE_TYPE | Local variable |
| IPV6 | Local variable |
| LOCAL_HOSTNAME | privateDnsName |
| LOCATION | Local variable |
| MAC | Local variable |
| MAC_ADDRESS | macAddresses |
| MACHINE_TYPE | Local variable |
| NAME | name |
| NETWORK | Local variable |
| OS_TYPE | Local variable |
| PRIVATE_IP | Local variable |
| PRIVATE_IPV4 | Local variable |
| PROJECT_ID | Local variable |
| PUBLIC_HOSTNAME | publicDnsName |
| PUBLIC_IPV4 | publicIpAddresses |
| REGION | Local variable |
| RESOURCE_GROUP_NAME | Local variable |
| SECURITY_GROUP | Local variable |
| STATE | status |
| SUBNET | Local variable |
| SUBSCRIPTION_ID | Local variable |
| VM_ID | Local variable |
| ZONE | Local variable |
Policy
Table 4: Policy attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ASSET_GROUP_IDS | Local variable |
| CREATED | sourceCreatedDate |
| EVALUATE_NOW | Local variable |
| ID | uid |
| INCLUDE_AGENT_IPS | Local variable |
| IS_LOCKED | Local variable |
| LAST_EVALUATED | lastAssessed |
| LAST_MODIFIED | sourceLastModified |
| STATUS | status |
| TAG_EXCLUDE_SELECTOR | Local variable |
| TAG_INCLUDE_SELECTOR | Local variable |
| TAG_SET_EXCLUDE | Local variable |
| TAG_SET_INCLUDE | Local variable |
| TITLE | name |
| POLICY_ID | Local variabl |
| POLICY_TITLE | Local variable |
Violation
Table 5: Violation attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CAUSE_OF_FAILURE.ADDED_DIRECTORIES | Local variable |
| CAUSE_OF_FAILURE.CONTENT_CHANGED_DIRECTORIES | Local variable |
| CAUSE_OF_FAILURE.DIRECTORY_FIM_UDC | Local variable |
| CAUSE_OF_FAILURE.MISSING | Local variable |
| CAUSE_OF_FAILURE.PERMISSION_CHANGED_DIRECTORIES | Local variable |
| CAUSE_OF_FAILURE.REMOVED_DIRECTORIES | Local variable |
| CAUSE_OF_FAILURE.UNEXPECTED | Local variable |
| CONTROL_ID | rationale, type |
| EXTENDED_EVIDENCE | Local variable |
| FIRST_FAIL_DATE | firstFailed |
| FIRST_PASS_DATE | firstPassed |
| HOST_ID | targets |
| ID | uid |
| LAST_FAIL_DATE | lastFailed |
| LAST_PASS_DATE | lastPassed |
| name (Technology) | Local variable |
| policyId | Local variable |
| policyTitle | Local variable |
| POSTURE_MODIFIED_DATE | sourceLastModified |
| PREVIOUS_STATUS | Local variable |
| REMEDIATION | Local variable |
| STATUS | status, statusCategory |
| techId | Local variable |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the Qualys PC connector:
Table 6: Qualys PC DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Host | LAST_SEEN NOT IN LAST 180 Days | 30 days after inactivity | Uses the LAST_SEEN attribute to identify hosts that are inactive within the last 180 days, and then purges the records after 30 days of inactivity. |
| Violation | Inactivity is delegated to the Host object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated host, and then purges the records after 30 days of inactivity. |
Operation options
The Qualys PC connector supports the following operation options. See connector operation options for information about how to apply them.
Expand the sections below to view the supported operation options per connector object.
Control
Table 7: Control operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Control | asset_group_ids | Any Qualys asset group ID | A comma-separated list of asset group IDs. You can use this option to retrieve controls from the specified Qualys asset groups. | Key: asset_group_ids Value: 101,202. This key and value combination only retrieves controls associated with the specified asset group IDs. |
| control_ids | Any Qualys control ID | A comma-separated list of control IDs. You can use this option to retrieve specific controls from the specified Qualys control IDs. | Key: control_ids Value: A1,B2. This key and value combination only retrieves controls with the specified control IDs. | |
| criticality_labels | MINIMAL, MEDIUM, SERIOUS, CRITICAL, URGENT | A comma-separated list of criticality labels. You can use this option to retrieve controls from Qualys based on their specified criticality label. | Key: criticality_labels Value: CRITICAL,URGENT. This key and value combination only retrieves controls with the specified criticality labels. | |
| criticality_values | 1, 2, 3, 4, 5 | A comma-separated list of criticality values. You can use this option to retrieve controls from Qualys based on their specified criticality value. | Key: criticality_values Value: 4,5. This key and value combination only retrieves controls with the specified criticality values. | |
| host_ids | Any Qualys host ID | A comma-separated list of host IDs. You can use this option to retrieve controls that are associated with specific hosts in Qualys. | Key: host_ids Value: 12345,67890. This key and value combination only retrieves controls associated with the specified host IDs. | |
| ids | Any Qualys control ID | A comma-separated list of control IDs. You can use this option to retrieve specific controls from Qualys by their unique identifiers. | Key: ids Value: C101,C202. This key and value combination only retrieves controls with the specified control IDs. | |
| ips | Any IP addresses or ranges | You can use this option to retrieve controls associated with specific IP addresses or ranges in Qualys. | Key: ips Value: 192.168.1.1,10.0.0.1-10.0.0.10. This key and value combination only retrieves controls associated with the specified IP addresses or ranges. | |
| status | active, closed, open, reopened | You can use this option to retrieve controls based on the specified status. | Key: status Value: active. This key and value combination only retrieves active controls. |
Host
Table 8: Host operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Host | ag_ids | Any Qualys asset group ID | You can use this option to retrieve hosts with the specified Qualys asset group IDs. You can use either a comma-separated list or specify a range with a dash. | Key: ag_ids Value: 386941-386945. This key and value combination only retrieves hosts associated with the specified asset group IDs. |
| ag_titles | Any Qualys asset group title | A comma-separated list of asset group titles. You can use this option to retrieve hosts with the specified Qualys asset group title. | Key: ag_titles Value: AssetGroup1,AssetGroup2. This key and value combination only retrieves hosts associated with the specified asset group titles. | |
| ars_max | Any asset risk score (ARS) value | You can use this option to only retrieve hosts with an ARS value less than or equal to the specified ARS max value. | Key: ars_max Value: 100. This key and value combination only retrieves host records with an ARS value of 100 or less. | |
| ars_min | Any ARS value | You can use this option to only retrieve hosts with an ARS value greater than or equal to the specified ARS min value. | Key: ars_min Value: 50. This key and value combination only retrieves hosts with an ARS value of 50 or more. | |
| host_metadata | all, azure, ec2, google | Retrieve host metadata for all cloud providers (Azure, EC2, Google) or only the specified cloud providers. | Key: host_metadata Value: all. This key and value combination retrieves metadata for hosts from all your cloud providers. | |
| host_metadata_fields | Any host metadata field attribute | A comma-separated list of host metadata field attributes. The connector retrieves only the specified host metadata field attributes. | Key: host_metadata_fields Value: instance_id,region. This key and value combination only retrieves the instance_id and region host metadata attributes. | |
| id_max | Any Qualys host ID | You can use this option to retrieve hosts up to and including the specified host ID value. | Key: id_max Value: H500. This key and value combination retrieves hosts with ID values up to and including H500. | |
| id_min | Any Qualys host ID | You can use this option to retrieve hosts starting from and including the specified host ID value. | Key: id_min Value: H100. This key and value combination retrieves hosts with ID values starting from and including H100. | |
| ids | Any Qualys host IDs | You can use this option to retrieve specific hosts from Qualys by their unique identifiers. You can use either a comma-separated list or specify a range with a dash. | Key: ids Value: H101,H202. This key and value combination only retrieves controls with the specified control IDs. | |
| ips | Any IP addresses or ranges | You can use this option to retrieve specific hosts from Qualys by the specified IP addresses. You can use either a comma-separated list or specify a range with a dash. | Key: ips Value: 10.10.10.1-10.10.10.100. This key and value combination only retrieves hosts associated with the specified range of IP addresses. | |
| network_ids | Any Qualys custom network IDs | A comma-separated list of custom network IDs. You can use this option to only retrieve hosts associated with the specified network IDs. | Key: network_ids Value: N101,N202. This key and value combination only retrieves hosts associated with the specified custom network IDs. | |
| os_pattern | Any regular expression that matches an operating system. | You can use this option to retrieve hosts with operating systems that match a specific regular expression. | Key: os_pattern Value: ^Windows.*. This key and value combination only retrieves hosts with operating systems starting with Windows. | |
| show_ars | 0, 1 | You can use this option to determine whether the ARS value is retrieved. Specify 1 to display the ARS value or 0 to omit it. | Key: show_ars Value: 1. This key and value combination displays the ARS value in the output. | |
| show_ars_factors | 0, 1 | You can use this option to determine whether the ARS contributing factors associated with each host displays in the output. Specify 1 to show the factors or 0 to omit them. | Key: show_ars_factors Value: 1. This key and value combination displays the ARS contributing factors for each host record retrieved. | |
| tag_exclude_selector | any, all | You can this option to determine how hosts are excluded based on tag matching. Set to any to exclude hosts that match at least one of the selected tags, or set to all to exclude hosts that match all of the selected tags. | Key: tag_exclude_selector Value: any. This key and value combination excludes hosts that match at least one of the selected tags. | |
| tag_include_selector | any, all | You can use this option to determine how hosts are included based on tag matching. Set to any to retrieve hosts that match at least one of the selected tags, or set to all to retrieve hosts that match all of the selected tags. | Key: tag_include_selector Value: all. This key and value combination only retrieves hosts that match all of the selected tags. | |
| tag_set_by | id, name | You can use this option to determine how the tag set for hosts are retrieved. Set to id to retrieve tag sets by providing tag IDs, or set to name to retrieve tag sets by providing tag names. | Key: tag_set_by Value: name. This key and value combination only retrieves tag sets for hosts based on tag names. | |
| tag_set_exclude | Tag name or IDs | You can use this option to specify a set of tags for exclusion. Hosts matching these tags will be excluded from the results. Provide the tag names or IDs for identification, with multiple entries separated by commas. | Key: tag_set_exclude Value: TagName1,TagName2. This key and value combination excludes hosts that match the specified tag names. | |
| tag_set_include | Tag name or IDs | You can use this option to specify a set of tags for inclusion. Hosts matching these tags will be included in the results. Provide the tag names or IDs for identification, with multiple entries separated by commas. | Key: tag_set_include Value: TagName1,TagName2. This key and value combination only retrieves hosts that match the specified tag names. | |
| use_tags | 0, 1 | You can use this option to indicate how hosts are retrieved. Set to 0 to retrieve hosts based on IP addresses/ranges and/or asset groups, or set to 1 to retrieve hosts based on asset tags. | Key: use_tags Value: 1. This key and value combination only retrieves hosts based on asset tags. |
Violation
Table 9: Violation operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Violation | asset_group_ids | Any Qualys asset group ID | A comma-separated list of asset group IDs. You can use this option to retrieve violations associated with specific Qualys asset groups. | Key: asset_group_ids Value: 101,202. This key and value combination only retrieves violations associated with the specified asset group IDs. |
| control_ids | Any Qualys control ID | A comma-separated list of control IDs. You can use this option to retrieve violations associated to specific controls in Qualys. | Key: control_ids Value: C101,C202. This key and value combination only retrieves violations associated the specified control IDs. | |
| criticality_labels | MINIMAL, MEDIUM, SERIOUS, CRITICAL, URGENT | A comma-separated list of criticality labels. You can use this option to retrieve violations based on their criticality labels in Qualys. | Key: criticality_labels Value: CRITICAL,URGENT. This key and value combination only retrieves violations with the specified criticality labels. | |
| criticality_values | 1, 2, 3, 4, 5 | A comma-separated list of criticality values. You can use this option to retrieve violations from Qualys based on their specified criticality value. | Key: criticality_values Value: 4,5. This key and value combination only retrieves violations with the specified criticality values. | |
| host_ids | Any Qualys host ID | A comma-separated list of host IDs. You can use this option to retrieve violations that are associated with specific hosts in Qualys. | Key: host_ids Value: 12345,67890. This key and value combination only retrieves violations associated with the specified host IDs. | |
| ids | Any Qualys violation ID | A comma-separated list of violation IDs. You can this option to retrieve specific violations from Qualys by their unique identifiers. | Key: ids Value: V101,V202. This key and value combination only retrieves violations with the specified violation IDs. | |
| ips | Any IP addresses or ranges | You can use this option to retrieve violations associated with specific IP addresses or ranges in Qualys. | Key: ips Value: 192.168.1.1,10.0.0.1-10.0.0.10. This key and value combination only retrieves violations associated with the specified IP addresses or ranges. | |
| policy_id | Any valid Qualys policy ID | The connector retrieves only the violations associated with the specified Qualys policy ID. | Key: policy_id Value: 445832. This key and value combination only retrieves violation information associated with policy ID 445832. | |
| policy_ids | Any valid Qualys policy IDs | A comma-separated list of valid Qualys policy IDs. The connector retrieves only violations associated with the specified Qualys policy IDs. | Key: policy_ids Value: 445832,445736. This key and value combination only retrieves violation information associated with policy IDs 445832 and 445736. | |
| status | active, closed, open, reopened | You can use this option to retrieve violations based on the specified status. | Key: status Value: closed. This key and value combination only retrieves closed violations. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The Qualys Policy Compliance connector uses the Qualys PC API v2 and v4. Specifically, it uses the following endpoints:
Table 10: Qualys PC API v2 Endpoints
| Connector Object | API Endpoint |
|---|---|
| Control | GET /api/2.0/fo/compliance/control/ |
GET /api/2.0/fo/compliance/policy/ | |
| Host | GET /api/4.0/fo/asset/host/ |
| Policy | GET /api/2.0/fo/compliance/policy/ |
| Violation | GET api/2.0/fo/compliance/posture/info |
GET /api/2.0/fo/compliance/policy/ |
Changelog
The Qualys Policy Compliance connector has undergone the following changes:
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
Table 11: Qualys PC connector changelog
| Version | Description | Date Published |
|---|---|---|
| 5.3.30 | Added the NETBIOS_HOSTNAME and DNS_HOSTNAME attributes to the Host object. | February 3rd, 2026 |
| 5.3.29 | No change. | January 26th, 2026 |
| 5.3.28 | No change. | December 26th, 2025 |
| 5.3.27 | No change. | November 25th, 2025 |
| 5.3.26 | No change. | November 19th, 2025 |
| 5.3.25 | No change. | October 30th, 2025 |
| 5.3.24 | No change. | September 9th, 2025 |
| 5.3.23 | No change. | August 15th, 2025 |
| 5.3.22 | No change. | August 5th, 2025 |
| 5.3.21 | Changed the IS_LOCKED attribute type on the Policy object from boolean to string to resolve a data type mismatch error. | August 5th, 2025 |
| 5.3.20 | No change. | July 11th, 2025 |
| 5.3.19 | No change. | July 2nd, 2025 |
| 5.3.18 | No change. | June 30th, 2025 |
| 5.3.17 | No change. | May 7th, 2025 |
| 5.3.16 | No change. | April 23rd, 2025 |
| 5.3.15 | No change. | April 8th, 2025 |
| 5.3.14 | Updated the API endpoint used to retrieve Host data from Qualys. The connector now uses /api/4.0/fo/asset/host/ instead of the deprecated /api/2.0/fo/asset/host/ endpoint. | March 26th, 2025 |
| 5.3.13 | - The connector now retrieves the Policy object from Qualys to ensure that violations are correctly linked to their associated policies. | March 12th, 2025 |
| 5.3.12 | No change. | March 3rd, 2025 |
| 5.3.11 | No change. | February 28th, 2025 |
| 5.3.10 | Added support for Data lifecycle management to the Host and Violation objects. | January 29th, 2025 |
| 5.3.9 | No change. | December 30th, 2024 |
| 5.3.8 | No change. | November 14th, 2024 |
| 5.3.7 | No change. | November 12th, 2024 |
| 5.3.6 | No change. | November 7th, 2024 |
| 5.3.5 | No change. | October 21st, 2024 |
| 5.3.4 | No change. | September 23rd, 2024 |
| 5.3.3 | No change. | September 20th, 2024 |
| 5.3.2 | No change. | August 23rd, 2024 |
| 5.3.1 | No change. | August 15th, 2024 |
| 5.3.0 | No change. | August 12th, 2024 |
| 5.2.4 | No change. | July 26th, 2024 |
| 5.2.3 | No change. | July 2nd, 2024 |
| 5.2.2 | No change. | June 26th, 2024 |
| 5.2.1 | No change. | May 15th, 2024 |
| 5.2.0 | No change. | May 7th, 2024 |
| 5.1.13 | Added the following API parameters:
| April 16th, 2024 |
| 5.1.12 | No change. | April 5th, 2024 |
| 5.1.11 | Updated dependencies. | March 11th, 2024 |
| 5.1.10 | Updated dependencies. | March 8th, 2024 |
| 5.1.9 | Fixed an issue where syncing of the Control or Violation objects would intermittently fail. | February 8th, 2024 |
| 5.1.8 | Added asset risk score (ARS) related operation options such as ars_max, ars_min, show_ars, and show_ars_factors to the Host connector object. | January 25th, 2024 |
| 5.1.7 | Initial Integration+ release. | September 19th, 2023 |