Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is an endpoint protection tool that detects malware, network-based attacks, and flags phishing sites in your network. You can bring host and security data from Microsoft Defender into Brinqa to help you detect and respond to security threats, and gain a comprehensive view of your attack surface to strengthen your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Microsoft Defender for Endpoint and how to obtain that information from Microsoft. See create a data integration for step-by-step instructions on setting up the integration.
Connection settings
When setting up a data integration, select Microsoft Defender for Endpoint from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Microsoft Defender for Endpoint with Brinqa:
-
API URL: The Microsoft Defender for Endpoint API URL. The default URL is
https://api.securitycenter.microsoft.com. -
Login URL: The Microsoft Azure authentication URL. The default URL is
https://login.microsoftonline.com. -
Client ID: The client ID associated with the service principal, which must have permissions to log in to Microsoft Azure Active Directory (Active AD) and return data from the Defender API. Required for all authentication methods.
-
Client secret: The client secret associated with the service principal. Required if you are not using certificate-based authentication.
-
Tenant ID: The unique identifier for the Active AD tenant associated with the service principal. Required for all authentication methods.
-
Private key: The private key associated with the service principal certificate. Required if you are not using a client secret.
You must provide either a client secret or a private key. If you don’t provide either, the connector cannot authenticate. If you provide both values, the connector uses private key for authentication.
Register a Microsoft Azure application
You must create a new application for the Microsoft Defender for Endpoint connector to authenticate with Azure AD and access the Microsoft Defender for Endpoint APIs. To register an application in your Azure AD tenant, follow these steps:
-
Log in to your Microsoft Azure Portal as an administrator.
-
Navigate to and click Microsoft Entra ID.
-
On the left-hand side of the page, click App registrations, and then click New registration.
-
Give your new application a name, select the supported account types, and provide an optional Redirect URI. If you do not have a redirect URI, you can leave the field as is.
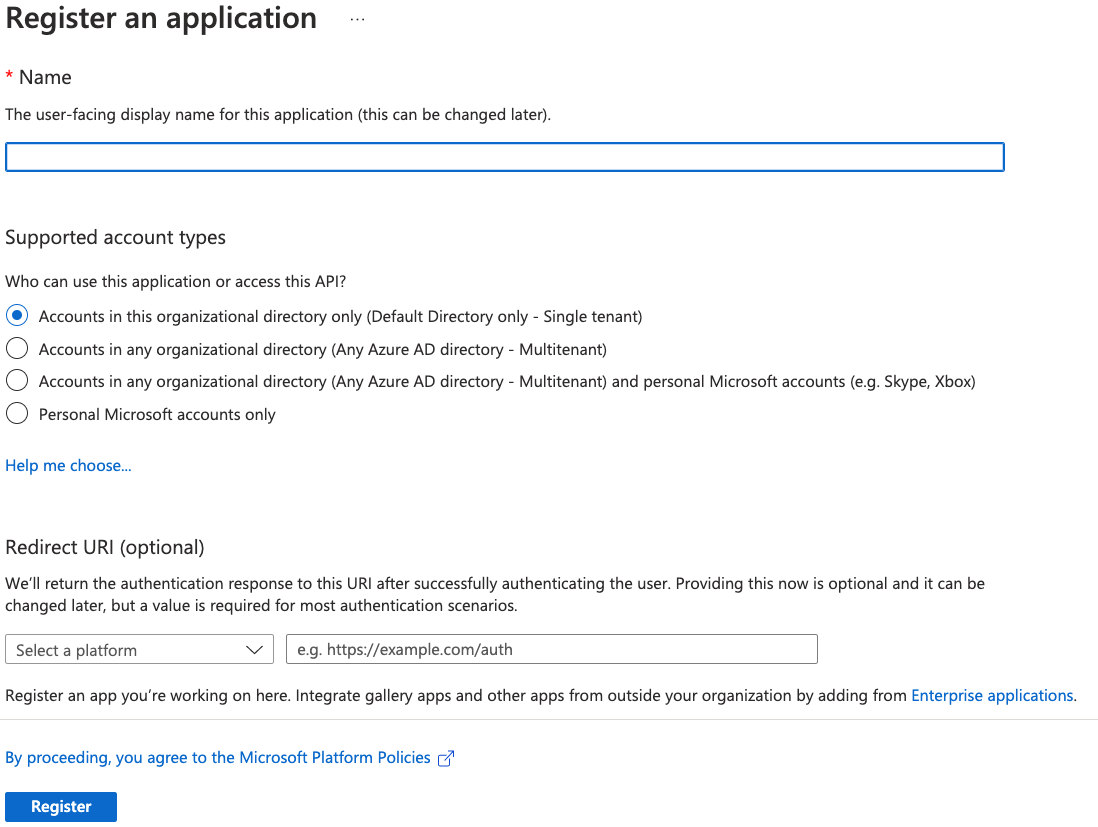
-
Click Register.
For additional details about registering an application in Azure AD and creating a service principal, see Microsoft Azure documentation.
Obtain Microsoft Azure credentials
After you have created your new Microsoft Azure application, your client and tenant ID display. Copy the Application (client) ID and Directory (tenant) ID as show below:
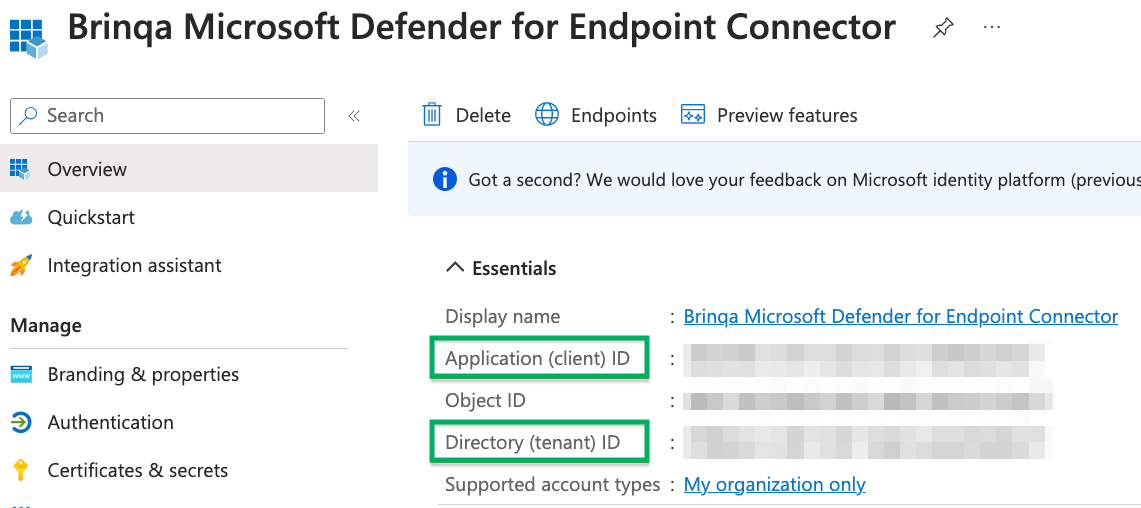
To obtain your client secret, follow these steps:
-
Click Certificates & secrets and then click New client secret.
-
Provide a description, set an expiry date, and then click Add.
The new client secret displays. You cannot view the client secret again. There is both a Value and Secret ID. The Value field is what is needed for authentication. Copy the Value field and save it in a secure location.
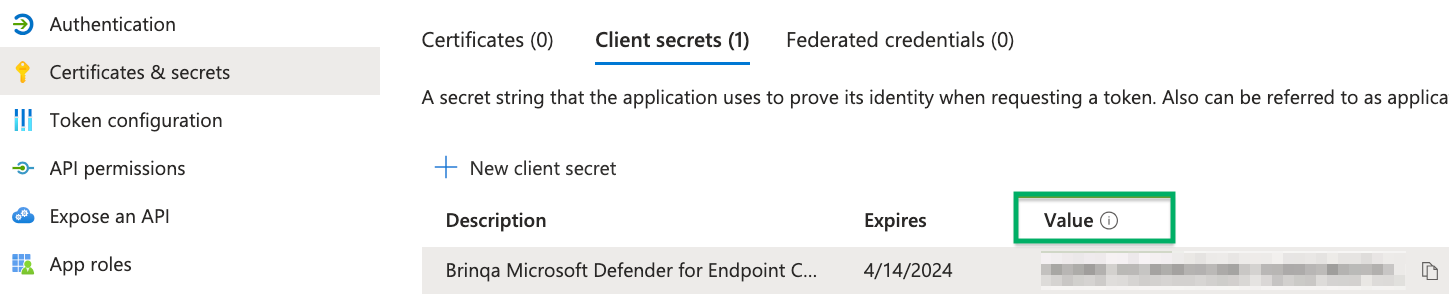
Assign permissions
After you have created your new Microsoft Azure application and obtained the authentication credentials, you must assign the required permissions for the application to access your data. To do so, follow these steps:
-
Navigate to API permissions > Add a permission > APIs my organization uses and select WindowsDefenderATP.
-
Click Application permissions, grant the following permissions, and then click Add permissions:
-
Machine:
Machine.Read.All -
Security Recommendation:
SecurityRecommendation.Read.All -
Software:
Software.Read.All -
User:
User.Read.All -
Vulnerability:
Vulnerability.Read.All
-
-
Click Grant admin consent for default directory, and then click Yes in the confirmation dialog. Your API permissions should resemble the following:
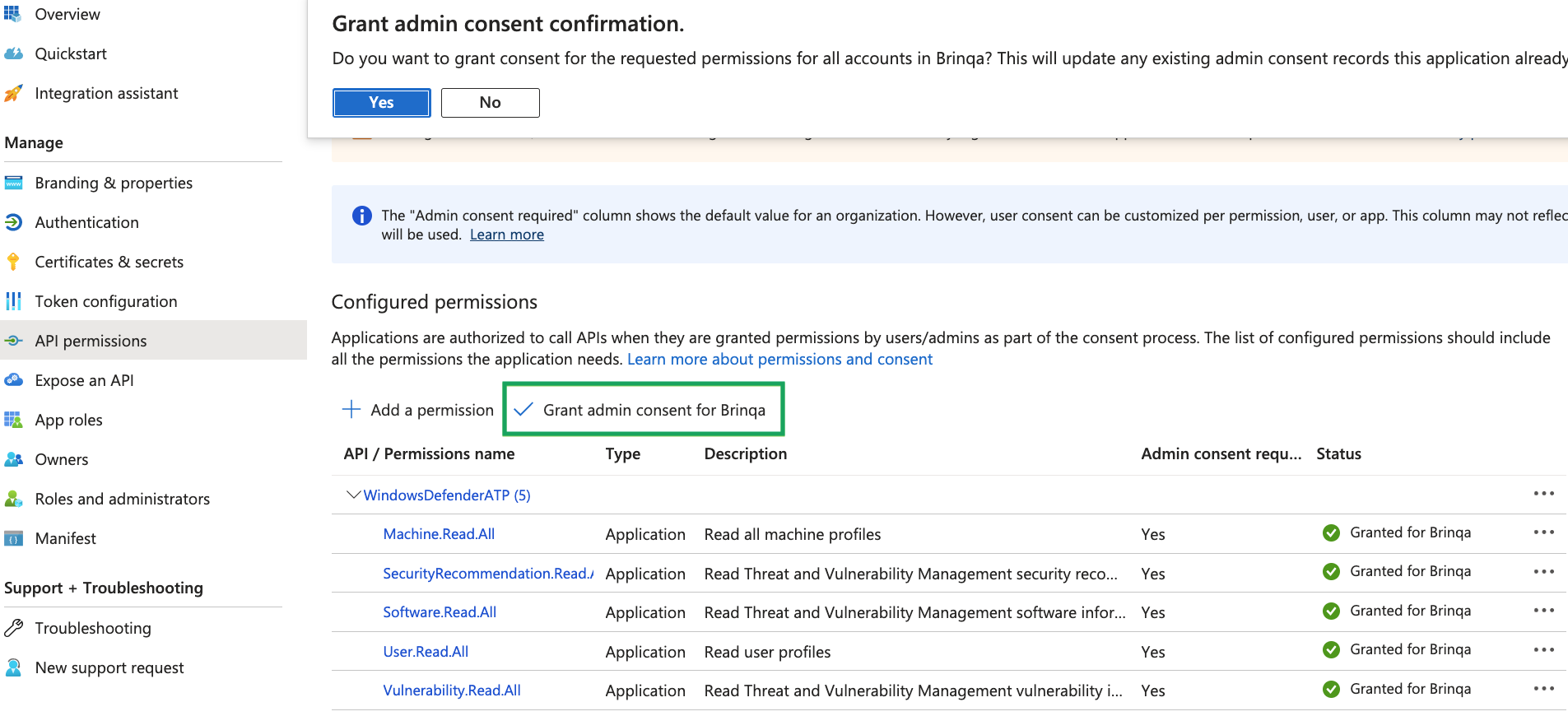
For additional information about Azure AD permissions, see Microsoft Azure documentation.
Generate a private key and certificate
If you choose to authenticate using a private key, you must generate a private key and certificate, upload the certificate to Azure, and then enter the combined string into the Private key field in the integration configuration.
Use your organization's approved method to generate the private key and certificate. If no method is available, or for testing purposes, you can follow the steps below to create a self-signed certificate using OpenSSL:
-
Open your terminal and generate a new private key:
openssl genpkey -algorithm RSA -out private_key.pem -
Generate a certificate signing request (CSR). Enter the required information when prompted:
openssl req -new -key private_key.pem -out csr.pem -
Generate a self-signed certificate:
openssl x509 -req -in csr.pem -signkey private_key.pem -out certificate.pem -
In the Microsoft Azure Portal, navigate to your registered Azure application.
-
On the left-hand side of the page, click Certificates & secrets, click the Certificates tab, and then click Upload certificate.
Upload the
certificate.pemfile you created in step 3. -
Click Add.
-
Combine
private_key.pemandcertificate.peminto a single string, and paste the result into the Private key field in the integration configuration. Use the following format:-----BEGIN PRIVATE KEY-----
<contents of private_key.pem>
-----END PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
<contents of certificate.pem>
-----END CERTIFICATE-----
For more information, see the Microsoft documentation on certificate credentials.
Additional settings
The Microsoft Defender for Endpoint connector contains additional options for specific configuration:
-
Maximum retries: The maximum number of times that the integration attempts to connect to the Microsoft Defender for Endpoint API before giving up and reporting a failure. The default setting is 5.
-
Fail sync on error: Select this option to fail the sync if an error occurs while downloading or processing the export file. If this option is not selected, the connector logs the error but continues processing.
Types of data to retrieve
The Microsoft Defender for Endpoint connector can retrieve the following types of data from the Microsoft Defender API:
Table 1: Data retrieved from Microsoft Defender
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Installed Package | No | Installed Package |
| Machine | Yes | Host |
| Package | No | Package |
| Vulnerability | No | Vulnerability |
| Vulnerability Definition | No | Vulnerability Definition |
For detailed steps on how to view the data retrieved from Microsoft Defender for Endpoint in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Installed Package
Table 2: Installed Package attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| computerDnsName | dnsNames |
| machine.id | targets |
| name | name |
| osPlatform | os |
| rbacGroupId | Local variable |
| rbacGroupName | Local variable |
| software.id | type |
| status | status |
| uid | uid |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Machine
Table 3: Machine attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| aadDeviceId | aadDeviceId, name |
| agentVersion | Local variable |
| CATEGORIES | categories |
| cloudProvider | cloudProvider |
| computerDnsName | hostnames, privateDnsNames, publicDnsNames |
| defenderAvStatus | Local variable |
| deviceValue | Local variable |
| exclusionReason | Local variable |
| exposureLevel | Local variable |
| healthStatus | status |
| id | uid |
| ipAddresses | ipAddresses, privateIpAddresses, publicIpAddress |
| isAadJoined | Local variable |
| isExcluded | Local variable |
| isPotentialDuplication | Local variable |
| lastSeen | lastSeen |
| macAddresses | macAddresses |
| machineTags | tags, instanceId |
| managedBy | Local variable |
| managedByStatus | Local variable |
| mergedIntoMachineId | Local variable |
| onBoardingStatus | Local variable |
| osArchitecture | description, os |
| osBuild | description, os |
| osPlatform | description, os |
| osProcessor | Local variable |
| osVersion | os |
| rbacGroupId | Local variable |
| rbacGroupName | Local variable |
| resourceId | Local variable |
| riskScore | Local variable |
| subscriptionId | Local variable |
| team_id | Local variable |
| team_name | Local variable |
| uptime | Local variable |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Package
Table 4: Package attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| activeAlert | Local variable |
| categories | categories |
| exposedMachines | Local variable |
| id | uid |
| impactScore | Local variable |
| name | name |
| publicExploit | Local variable |
| Status | status |
| vendor | Local variable |
| versions | Local variable |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Vulnerability
Table 5: Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| cveId | type |
| deviceId | targets, deviceId |
| deviceName | hostnames, deviceName |
| diskPaths | diskPaths |
| eventTimestamp | sourceLastModified, lastFixed |
| firstSeenTimestamp | firstFound |
| id | uid |
| lastSeenTimestamp | lastFound |
| rbacGroupName | rbacGroupName |
| recommendedSecurityUpdate | recommendedSecurityUpdate |
| recommendedSecurityUpdateId | recommendedSecurityUpdateId |
| registryPaths | registryPaths |
| results | results |
| softwareName | softwareName |
| softwareVendor | softwareVendor |
| softwareVersion | softwareVersion |
| sourceCreatedDate | sourceCreatedDate |
| status | status, statusCategory |
| vulnerabilitySeverityLevel | severity, sourceSeverity |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Vulnerability Definition
Table 6: Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| cvssV3 | cvssV3BaseScore |
| description | description, summary |
| exploitTypes | Local variable |
| exploitUris | exploits, references |
| exploitVerified, publicExploit, exploitInKit | exploitability |
| id | cveIds, cveRecords, uid |
| name | cveIds, name |
| publishedOn | publishedDate |
| recommendation.isHasUnpatchableCve | patchAvailable |
| recommendations.getRelatedComponent | affected |
| recommendation.getRecommendationName | recommendation |
| severity | severity, sourceSeverity |
| updatedOn | sourceLastModified |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the Microsoft Defender for Endpoint connector:
Table 7: Microsoft Defender for Endpoint DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Machine | LAST_SEEN NOT IN LAST 7 Days | 30 days after inactivity | Uses the LAST_SEEN attribute to identify machines inactive for the last 7 days, and then purges the records after 30 days of inactivity. |
| Vulnerability | DEVICE_LAST_SEEN NOT IN LAST 7 Days OR LAST_CAPTURED NOT IN LAST 1 Day | 30 days after inactivity | Uses the DEVICE_LAST_SEEN attribute to identify vulnerabilities inactive for the last 7 days or the LAST_CAPTURED attribute for vulnerabilities inactive in the last day, and then purges the records after 30 days of inactivity. |
Operation options
The Microsoft Defender for Endpoint connector supports the following operation options. See connector operation options for information about how to apply them.
Click the sections below to view the supported operation options per connector object.
Installed Package
Table 8: Installed Package operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Package | id | Any installed package ID | Retrieve installed packages with the specified ID. | Key: id Value: microsoft-_-edge. This key and value combination only retrieves installed packages with the microsoft-_-edge ID. |
| name | Any installed package name | Retrieve installed packages with the specified name. | Key: name Value: edge. This key and value combination only retrieves installed packages with the edge name. | |
| vendor | Any installed package vendor | Retrieve installed packages with the specified vendor name. | Key: vendor Value: microsoft. This key and value combination only retrieves installed packages with the microsoft vendor name. |
Machine
Table 9: Machine operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Machine | aadDeviceId | Any unique identifier for a Azure Active Directory machine | Retrieve machines with the specified Azure Active Directory device ID. | Key: aadDeviceId Value: 12345678-abcd-1234-ef00-123456abcdef. This key and value combination only retrieves machines whose Azure Active Directory device ID is 12345678-abcd-1234-ef00-123456abcdef. |
| computerDnsName | Any fully-qualified name of a machine. | Retrieve machines with the specified DNS name. | Key: computerDnsName Value: desktop-1212.brinqa.com. This key and value combination only retrieves the machine whose DNS name is desktop-1212.brinqa.com. | |
| exposureLevel | None, Low, Medium, High | Retrieve machines with the specified exposure level as evaluated by Microsoft Defender for Endpoint. | Key: exposureLevel Value: Medium. This key and value combination only retrieves machines with a medium exposure level. | |
| healthStatus | Active, Inactive, ImpairedCoummunication, NoSensorData, NoSensorDataImpairedCommunication, Unknown | Retrieve machines with the specified heatlh status as evaluated by Microsoft Defender for Endpoint. | Key: healthStatus Value: Active. This key and value combination only retrieves machines with an active health status. | |
| lastIpAddress | Any IP address associated with a machine | Retrieve machines with the associated IP address. | Key: lastIpAddress Value: 192.0.2.53. This key and value combination only retrieves machines associated with an IP address of 192.0.2.53. | |
| lastSeen | Any date and time value in the ISO 8601 format. | Retrieve machines based on the last time Microsoft Defender for Endpoint received a full device report for the machine. | Key: lastSeen Value: 2023-01-01TO0:00:00Z. This key and value combination only retrieves machines whose full device report was received on January 1st, 2023. | |
| onboardingStatus | onboarded, CanBeOnboarded, InsufficientInfo, Unsupported | Retrieve machines with the specified onboarding status. | Key: onboardingStatus Value: Unsupported. This key and value combination only retrieves machines that have an unsupported onboarding status. | |
| osPlatform | A comma-separated list of operating systems. | Retrieve machines running on the specified operating systems. | Key: osPlatform Value: Windows 11, macOS. This key and value combination only retrieves machines running on Windows 11 and macOS. | |
| rbacGroupId | Any RBAC group ID | Retrieve machines with the specified RBAC group ID. | Key: rbacGroupId Value: 7b3f5c5c-c4c4 This key and value combination only retrieves machines with the RBAC group ID of 7b3f5c5c-c4c4. | |
| riskScore | None, Informational, Low, Medium, High | Retrieve machines with the specified risk score as evaluated by Microsoft Defender for Endpoint. | Key: riskScore Value: High. This key and value combination only retrieves machines with a high risk score. |
You can also use advanced filter syntax to combine multiple criteria. For example: filter: "osPlatform ne 'iOS' and osPlatform ne 'Android' and osPlatform ne 'Linux'" retrieves machines that are not running iOS, Android, or Linux. This syntax supports operators like ne (not equal), eq (equal), and logical operators like and, or.
Package
Table 10: Package operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Package | id | Any package ID | Retrieve packages with the specified ID. | Key: id Value: microsoft-_-edge. This key and value combination only retrieves packages with the microsoft-_-edge ID. |
| name | Any package name | Retrieve packages with the specified name. | Key: name Value: edge. This key and value combination only retrieves packages with the edge name. | |
| vendor | Any package vendor | Retrieve packages with the specified vendor name. | Key: vendor Value: microsoft. This key and value combination only retrieves packages with the microsoft vendor name. |
Vulnerability
Table 11: Vulnerability operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Vulnerability | rbacGroupId | Any RBAC group ID | Retrieve vulnerabilities associated with the specified RBAC group ID. | Key: rbacGroupId Value: 7b3f5c5c-c4c4 This key and value combination only retrieves vulnerabilities associated with the RBAC group ID of 7b3f5c5c-c4c4. |
| severity | Low, Medium, High, or Critical | Retrieve vulnerabilities with the specified severity level. | Key: severity Value: Critical. This key and value combination only retrieves the critical vulnerabilities. | |
| status | active, fixed | Retrieve only active or fixed vulnerabilities. | Key: status Value: active. This key and value combination only retrieves active vulnerabilities. |
Vulnerability Definition
Table 12: Vulnerability Definition operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Vulnerability Definition | id | A comma-separated list of vulnerability IDs. | Retrieve vulnerabilities with the specified IDs. | Key: id Value: CVE-2023-22664. This key and value combination only retrieves vulnerabilities pertaining to CVE-2023-22664. |
| cvssV3 | Any CVSS v3 (Common Vulnerability Scoring System) score | Retrieve vulnerabilities with the specified CVSS v3 score. | Key: cvssV3 Value: 6.3. This key and value combination only retrieves vulnerabilities that have a CVSS v3 score of 6.3. | |
| description | Any CVE description | Retrieve vulnerabilities with the specified description. | Key: description Value: A memory corruption vulnerability exists in Microsoft Exchange Server when the server fails to properly handle objects in memory. This key and value combination only retrieves vulnerabilities associated with the specified CVE description. | |
| name | Any CVE name | Retrieve vulnerabilities with the specified CVE name. | Key: name Value: CVE-2019-0608. This key and value combination only retrieves vulnerabilities associated with CVE-2019-0608. | |
| publishedOn | Any date and time value in the ISO 8601 format | Retrieve vulnerabilities published on the specified date. | Key: publishedOn Value: 2023-02-09TO9:45:00Z. This key and value combination only retrieves vulnerabilities published on February 9th, 2023 at 9:45AM. | |
| severity | Low, Medium, High, or Critical | Retrieve vulnerabilities with the specified severity level. | Key: severity Value: Critical. This key and value combination only retrieves the critical vulnerabilities. | |
| updatedOn | Any date and time value in the ISO 8601 format | Retrieve vulnerabilities that were last updated on the specified date. | Key: updatedOn Value: 2023-02-09TO9:45:00Z. This key and value combination only retrieves vulnerabilities updated on February 9th, 2023 at 9:45AM. |
The option keys and values are case-sensitive as they are shown in this documentation.
Synchronization types
When using the Microsoft Defender for Endpoint connector, it's important to understand the different sync interval types available:
-
Beginning of Time (BoT)
- BoT syncs comprehensively pull all available data from your Microsoft Defender for Endpoint environment, as specified by your integration configuration. You should use a BoT sync for initial setups or complete data refreshes.
-
Delta
- Delta syncs retrieve only the data that has changed over the last 14 days since your last sync. You should use delta syncs after running an initial BoT sync for regular updates, capturing new, resolved, or updated data without reprocessing all historical data.
APIs
The Microsoft defender connector uses the Microsoft Defender for Endpoint API. Specifically, it uses the following endpoints:
Table 13: Microsoft Defender for Endpoint API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Installed Package | GET /api/software/{softwareId}/distributions GET /api/Software/{softwareId}/machineReferences |
| Machine | GET /api/machines |
| Package | GET /api/software/{softwareId}/distributions |
| Vulnerability | GET /api/machines/SoftwareVulnerabilityChangesByMachine |
GET /api/machines/SoftwareVulnerabilitiesExport | |
| Vulnerability Definition | GET /api/recommendations |
GET /api/recommendationsId/vulnerabilities | |
GET /api/vulnerabilities |
Changelog
The Microsoft Defender for Endpoint connector has undergone the following changes:
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
Table 14: Microsoft Defender for Endpoint connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.4.28 | No change. | February 4th, 2026 |
| 3.4.27 | Fixed an issue where operation options for filtering Machine objects by RBAC group ID were returning more records than expected. Updated documentation to clarify the correct filter syntax. | January 26th, 2026 |
| 3.4.26 | No change. | November 17th, 2025 |
| 3.4.25 | No change. | November 17th, 2025 |
| 3.4.24 | Resolved an issue that previously limited Machine record collection to 10,000 records; the connector now retrieves all available Machine or Package records beyond this limit. | November 10th, 2025 |
| 3.4.23 | - Added a DEVICE_LAST_SEEN attribute to the Vulnerability object. - Updated the data lifecycle management strategy for the Vulnerability object to use the DEVICE_LAST_SEEN attribute. | October 23rd, 2025 |
| 3.4.22 | No change. | October 16th, 2025 |
| 3.4.21 | Reverted the changes implemented in 3.4.20, removing the package ID attachment to the TYPE attribute in the Vulnerability object. If you previously upgraded to 3.4.20 and purged data as recommended, you may need to purge again before upgrading to this version. | October 15th, 2025 |
| 3.4.20 | Fixed an issue where the incorrect recommendations were populating for the Vulnerability Definition object. As a result, the RECOMMENDATION_ID attribute was added to the Vulnerability Definition object. This will impact how UID's are generated for vulnerability definitions. Therefore, it is strongly recommended to purge existing data associated with this connector before updating to v3.4.20. | September 17th, 2025 |
| 3.4.19 | No change. | August 5th, 2025 |
| 3.4.18 | Fixed an issue where the connector sync was marked as successful despite the Vulnerability object sync encountering java.io.EOFException errors. As a result, a new additional setting has been added to provide more control over sync behavior: Fail sync on error | August 4th, 2025 |
| 3.4.17 | Added the following attributes to the Vulnerability object:
| August 1st, 2025 |
| 3.4.16 | Fixed an issue where Vulnerability Definition names were not generated correctly. The connector now uses the Vulnerability Definition NAME attribute when available, and falls back to the CVE_ID attribute if the name is not available. | June 11th, 2025 |
| 3.4.15 | Fixed an issue where the Machine object sync was failing with a NullPointerException error. | May 27th, 2025 |
| 3.4.14 | No change. | May 21st, 2025 |
| 3.4.13 | No change. | May 20th, 2025 |
| 3.4.12 | No change. | April 22nd, 2025 |
| 3.4.11 | - Fixed an issue where the connector was not retrieving complete data during delta syncs for the Host and Vulnerability objects. - Fixed an issue where the Vulnerability Definition name was missing. The connector now uses the vulnerability ID if the name is not provided by the API. - Renamed the PATCH_AVAILABLE attribute to PATCHABLE on the Vulnerability Definition object. | April 7th, 2025 |
| 3.4.10 | The Client secret and Private key connection settings are now optional. If both are provided, the connector prioritizes the Private key for authentication. | April 1st, 2025 |
| 3.4.9 | Added support for a new optional authentication method using a private key and certificate. For additional information, see Microsoft documentation. | March 26th, 2025 |
| 3.4.8 | No change. | February 12th, 2025 |
| 3.4.7 | No change. | January 28th, 2025 |
| 3.4.5 | Added support for CVSS calculations to the Vulnerability Definition object. As a result, the following attributes have been added to Vulnerability Definition:
| December 19th, 2024 |
| 3.4.4 | No change. | December 6th, 2024 |
| 3.4.3 | No change. | November 28th, 2024 |
| 3.4.2 | No change. | October 7th, 2024 |
| 3.4.1 | Added support for Data lifecycle management to the Machine and Vulnerability objects. | September 27th, 2024 |
| 3.4.0 | No change. | September 17th, 2024 |
| 3.3.10 | Code cleanup and general maintenance. | September 4th, 2024 |
| 3.3.9 | No change. | August 27th, 2024 |
| 3.3.8 | Removed the WEAKNESSES attribute from the Package object. | July 24th, 2024 |
| 3.3.7 | No change. | July 24th, 2024 |
| 3.3.6 | Changed the WEAKNESS attribute type on the Package object from integer to string. | July 8th, 2024 |
| 3.3.5 | - Added three new operation options for the Vulnerability object: rbacGroupId, severity, and status. - Changed the SOURCE_RISK_SCORE attribute on the Machine object to SOURCE_RISK_RATING. | May 20th, 2024 |
| 3.3.4 | Code cleanup and general maintenance. | May 20th, 2024 |
| 3.3.3 | No change. | May 20th, 2024 |
| 3.3.2 | No change. | May 9th, 2024 |
| 3.3.1 | The connector now retrieves the Installed Package and Package objects from Microsoft. | May 3rd, 2024 |
| 3.3.0 | No change. | April 30th, 2024 |
| 3.2.2 | Mapped Affected Software in a CVE to the AFFECTED attribute on the Vulnerability Definition object. | April 26th, 2024 |
| 3.2.1 | Code cleanup and general maintenance. | April 19th, 2024 |
| 3.2.0 | Code cleanup and general maintenance. | April 4th, 2024 |
| 3.1.18 | Code cleanup and general maintenance. | April 4th, 2024 |
| 3.1.17 | Added the following attributes to the Machine object:
| March 24th, 2024 |
| 3.1.16 | No change. | March 14th, 2024 |
| 3.1.15 | Fixed an issue where the EXPLOITABILITY attribute in all Vulnerability Definition records was incorrectly set to 'Actively used'. | February 11th, 2024 |
| 3.1.14 | Set the INSTANCE_ID attribute in the Machine object if the source specifies a value using the instanceId tag. | February 2nd, 2024 |
| 3.1.13 | Made Vulnerability and Vulnerability Definition objects optional in data integration. | January 26th, 2024 |
| 3.1.12 | No change. | January 24th, 2024 |
| 3.1.11 | No change. | October 11th, 2023 |
| 3.1.9 | Added a delay in deleting temporary storage to avoid syncing issues. | July 20th, 2023 |
| 3.1.8 | The connector now uses updatedOn instead of publishedOn to fetch updates for the Vulnerability Definition object. | July 19th, 2023 |
| 3.1.7 | - Enhanced to make concurrent attempts to retrieve recommendations for vulnerabilities. However, in the event of failure, it proceeds without this data. - Increased the default setting for Maximum Retries to 10. | May 18th, 2023 |
| 3.1.6 | - Excluded 00000000-0000-0000-0000-000000000000 as a valid Azure Active Directory device ID. - Updated dependencies. | May 9th, 2023 |
| 3.1.5 | - Fixed a null pointer exception when there's no filter provided. - Fixed a null pointer exception when the Machine object is synced from the beginning of time. | May 8th, 2023 |
| 3.1.4 | Added filtering capability to the Machine and Vulnerability Definition objects. | April 3rd, 2023 |
| 3.1.3 | Code cleanup and general maintenance. | February 22nd, 2023 |
| 3.1.2 | Made the value of the HOSTNAME attribute consistent. | February 14th, 2023 |
| 3.1.1 | Tried to generate a name for the Machine object based on its DNS name, IP addresses, or Azure Active Directory device ID. | February 9th, 2023 |
| 3.1.0 | Ignored exceptions when downloading export files. | February 8th, 2023 |
| 3.0.3 | Initial Integration+ release. | February 7th, 2023 |