Mend.io
Mend.io (formerly WhiteSource) is an application security tool used for scanning, prioritizing, and remediating security vulnerabilities in your organization's applications and code projects. You can bring application, code project, package, and security data from Mend.io into the Brinqa to prioritize and address potential vulnerabilities.
This document details the information you must provide for the connector to authenticate with Mend.io and how to obtain that information from Mend.io. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Mend from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Mend.io with Brinqa:
-
Server URL: The Mend.io server URL. The default URL is
https://app.whitesourcesoftware.com. -
API Key and User Key: The API keys associated with the Mend.io account, which must have permissions to log in to the API server and return data.
Generate Mend.io API keys
For the Mend.io connector to access the Mend.io API, you must provide API keys. To do so, follow these steps:
-
Log in to your organization's Mend.io account as an administrator.
-
Click the User profile and then click Profile from the dropdown.
-
Click the User Keys tab, then locate the User Keys and Product Tokens sections on the page.
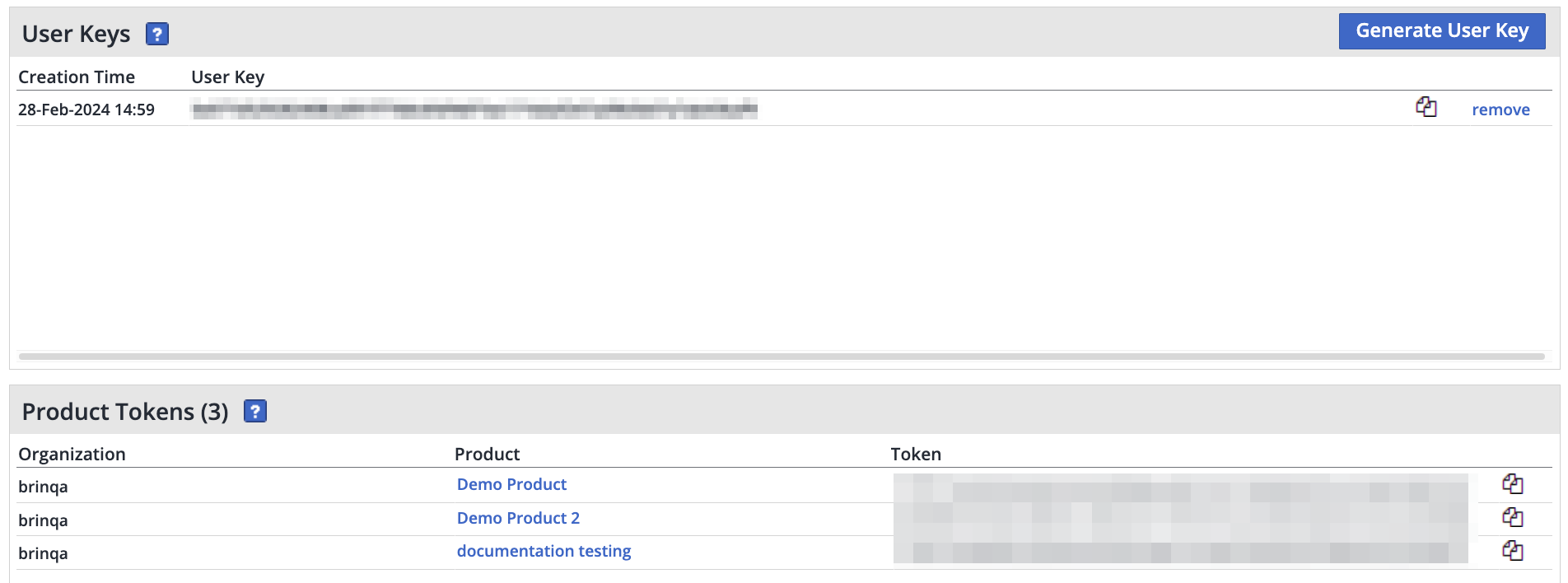
-
Copy the User Key and paste it into the User Key field of the integration configuration.
-
Copy the Product Token and paste it into the API Key field of the integration configuration.
If multiple product tokens are listed, select the token associated with the product you're integrating with Brinqa. This may depend on your specific use case or the particular data you need to access.
If you do not have the permissions to create API keys, contact your Mend.io administrator. For additional information, see the Mend.io documentation.
Additional settings
The Mend.io connector contains an additional option for specific configuration:
- Parallel requests: The maximum number of parallel API requests. The default setting is 8.
Types of data to retrieve
The Mend.io connector can retrieve the following types of data from the Mend.io API:
Table 1: Data retrieved from Mend.io
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Application | Yes | Application |
| Code Project | Yes | Code Project |
| Open Source Finding | Yes | Open Source Finding |
| Open Source Finding Definition | Yes | Open Source Finding Definition |
| Package | Yes | Package |
| Violation | Yes | Violation |
| Violation Definition | Yes | Violation Definition |
For detailed steps on how to view the data retrieved from Mend.io in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Application
Table 2: Application attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORIES | categories |
| CREATION_DATE | sourceCreatedDate |
| LAST_MODIFIED | sourceLastModified |
| NAME | name |
| SYS_ID | uid |
Code Project
Table 3: Code Project attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORIES | categories |
| CREATION_DATE | sourceCreatedDate |
| LAST_MODIFIED | sourceLastModified |
| NAME | name |
| PRODUCT_ID | Local variable |
| PRODUCT_NAME | Local variable |
| SYS_ID | uid |
| TAGS | tags |
Open Source Finding
Table 4: Open Source Finding attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| LIBRARY_ID | Local variable, targets |
| LIBRARY_NAME | Local variable |
| PROJECT_ID | Local variable, targets |
| PRODUCT_ID | Local variable, targets |
| PROJECT_NAME | Local variable |
| PRODUCT_NAME | Local variable |
| SYS_ID | uid |
| TITLE | Local variable |
| VULNERABILITY_ID | uid, name |
Open Source Finding Definition
Table 5: Open Source Finding Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CVSSV2_BASE_SCORE | Use CVSS calculator |
| CVSSV3_BASE_SCORE | Use CVSS calculator |
| CVSSV3_SEVERITY | Local variable |
| CVSSV3_VECTOR | Use CVSS calculator |
| DATE_PUBLISHED | publishedDate |
| DESCRIPTION | description |
| LAST_FOUND | lastFound |
| LIBRARY_ID | Local variable, targets |
| LIBRARY_NAME | Local variable |
| PROJECT_ID | Local variable, targets |
| PRODUCT_ID | Local variable, targets |
| PROJECT_NAME | Local variable |
| PRODUCT_NAME | Local variable |
| REFS | references |
| SEVERITY | severity, sourceSeverity, severityScore |
| SOLUTION | recommendation |
Package
Table 6: Package attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ARTIFACT_ID | localVariable |
| CATEGORIES | categories |
| COORDINATES | localVariable |
| DESCRIPTION | description |
| FILE_NAME | fileName |
| FORMAT | type |
| GROUP_ID | localVariable |
| LICENSES | licences |
| NAME | name |
| PRODUCTS | localVariable, targets |
| PROJECTS | projects, targets |
| SHA_1 | localVariable |
| SYS_ID | uid |
| VERSION | currentVersion |
Violation
Table 7: Violation attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ALERT_TYPE | type, uid, name |
| DESCRIPTION | description |
| DIRECT_DEPENDENCY | Local variable |
| LAST_FOUND | lastFound |
| LEVEL | severity, sourceSeverity, severityScore |
| LIBRARY_ID | Local variable, target |
| LIBRARY_NAME | Local variable |
| PROJECT_ID | Local variable, target |
| PROJECT_NAME | Local variable |
| PRODUCT_ID | Local variable, target |
| PRODUCT_NAME | Local variable |
| SYS_ID | uid |
Violation
Table 8: Violation Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ALERT_TYPE | name, type, uid |
| DESCRIPTION | description |
| DIRECT_DEPENDENCY | Local variable |
| LEVEL | severity, sourceSeverity, severityScore |
| LIBRARY_NAME | Local variable |
| PRODUCT_NAME | Local variable |
| PROJECT_NAME | Local variable |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models (UDM). They only exist on the source data model (SDM).
Use CVSS calculator indicates that the CVSS (Common Vulnerability Scoring System) vectors and scores aren't directly mapped to a specific attribute on the UDM. Instead, a specialized library calculates the CVSS scores from the provided CVSS vector strings.
Operation options
The Mend.io connector supports the following operation options. See connector operation options for information about how to apply them.
Table 9: Mend.io connector operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Code Project | projectTags | true, false | Enables or disables filtering of code projects based on project tags. When set to true, the connector retrieves code projects that have been specifically tagged. | Key: projectTags Value: true. This key and value combination only retrieves code projects that have been specifically tagged. |
| Package | nameAsIdentifier | true, false | Determines whether the package name should be treated as a unique identifier for the purpose of data retrieval. When set to true, it ensures that only packages with unique names are considered, potentially reducing duplicates. | Key: nameAsIdentifier Value: true. This key and value combination only retrieves packages where the name is treated as a unique identifier. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The Mend.io connector uses the Mend.io API v1.4. Specifically, it uses the following requestType values within the single API endpoint (/api/v1.4):
Table 10: Mend.io API v1.4 Supported Request Types
| Connector Object | Request Type |
|---|---|
| Application | getAllProducts |
| Code Project | getAllProducts, getOrganizationProductVitals, getProjectTags |
| Open Source Finding | getAllProducts, getAllProjects, getProjectAlertsByType |
| Open Source Finding Definition | getAllProducts, getAllProjects, getProjectAlertsByType |
| Package | getAllProducts, getAllProjects, getProjectInventoryReport |
| Violation | getProjectAlertsByType |
| Violation Definition | getProjectAlertsByType |
Changelog
The Mend.io connector has undergone the following changes:
Table 11: Mend.io connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.0.3 | Fixed an issue where findings were incorrectly tied to the wrong assets due to reused numeric UIDs across different asset types. As a result:
| October 21st, 2024 |
| 3.0.2 | Changed the DIRECT_DEPENDENCY attribute type on the Violation object from string to boolean to resolve a data type mismatch error. | September 10th, 2024 |
| 3.0.1 | - The Static Code Finding object has been renamed to Violation to accurately reflect that the data represents policy violations against library usage, such as new versions, multiple versions in use, and invalid versions. - The Static Code Finding Definition object has been renamed to Violation Definition to align with the new classification of the data. - Fixed an issue with the Violation Definition object where the UIDs were incorrectly generated. The UIDs are now correctly constructed by combining the Name and Description fields to ensure proper identification of each violation. | July 22nd, 2024 |
| 3.0.0 | Initial Integration+ release. | February 29th, 2024 |