Microsoft Intune
Microsoft Intune is a cloud-based endpoint protection management tool. You can bring host and mobile device data from Microsoft Intune into Brinqa to gain a comprehensive view of your hosts and take action to address any potential vulnerabilities on those assets to strengthen your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Microsoft Intune and how to obtain that information from Microsoft. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Microsoft Intune from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Microsoft Intune with Brinqa:
-
API URL: The Microsoft Graph API URL. The default URL is
https://graph.microsoft.com. -
Login URL: The Microsoft Azure authentication URL. The default URL is
https://login.microsoftonline.com. -
Client ID and Client secret: The client ID and client secret associated with the service principal, which must have permissions to log in to the Microsoft Azure Active Directory (Active AD) and return data from the Graph API.
-
Tenant ID: The unique identifier for the Active AD tenant associated with the service principal.
Register a Microsoft Azure application
You must create a new application for the Microsoft Intune connector to authenticate with Azure AD and access the Graph API. To register an application in your Azure AD tenant, follow these steps:
-
Log in to your Microsoft Azure Portal as an administrator.
-
Navigate to and click Microsoft Entra ID.
-
On the left-hand side of the page, click App registrations, and then click New registration.
-
Give your new application a name, select the supported account types, and provide an optional Redirect URI. If you do not have a redirect URI, you can leave the field as is.
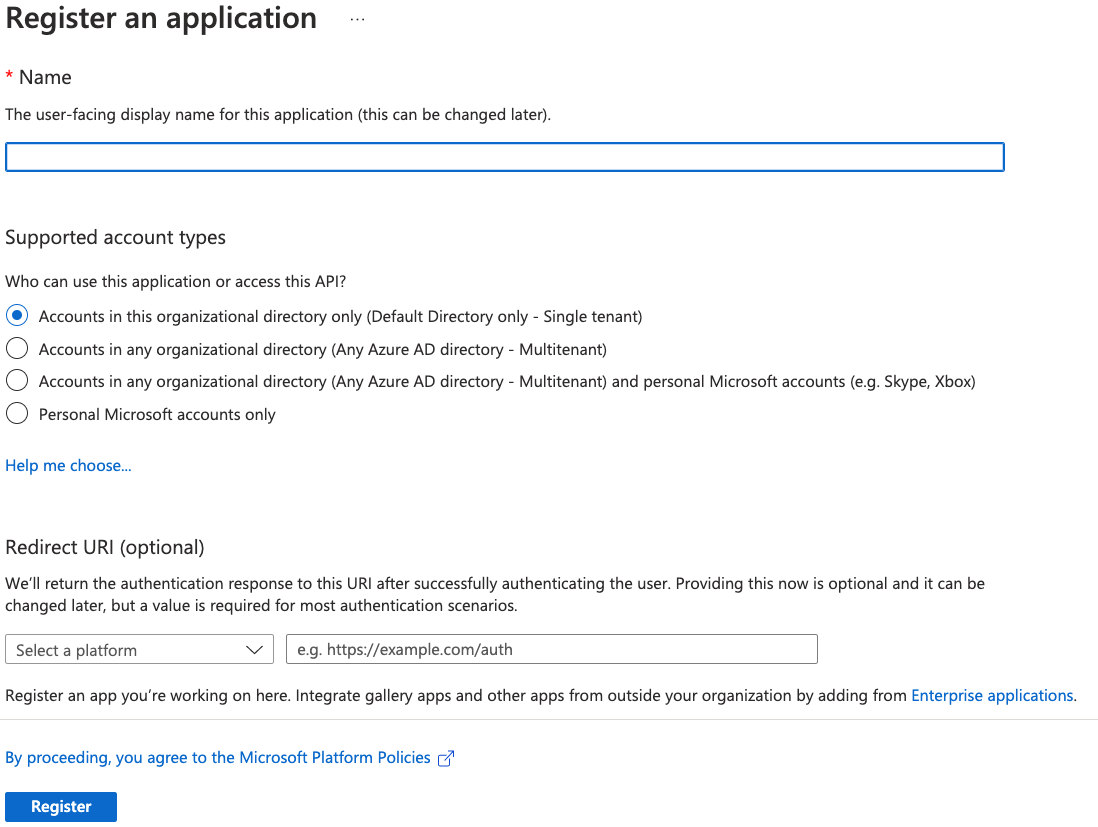
-
Click Register.
For additional details about registering an application in Azure AD and creating a service principal, see Microsoft Azure documentation.
Obtain Microsoft Azure credentials
After you have created your new Microsoft Azure application, your client and tenant ID display. Copy the Application (client) ID and Directory (tenant) ID as shown below:
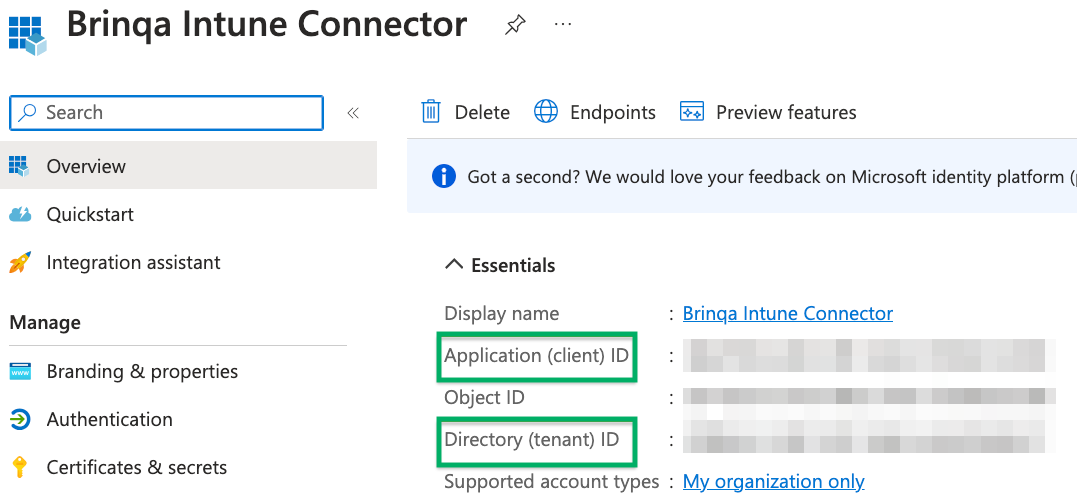
To obtain your client secret, follow these steps:
-
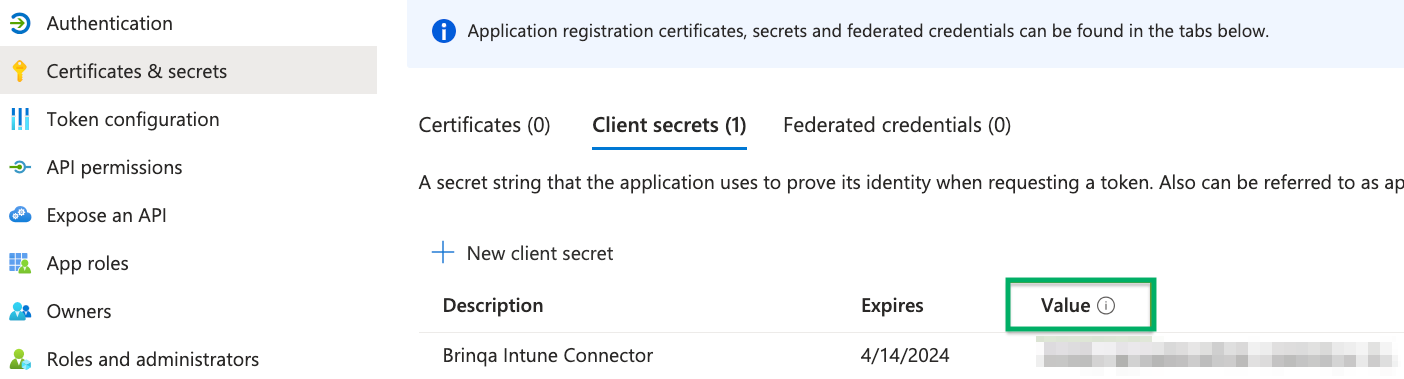
Click Certificates & secrets and then click New client secret.
-
Provide a description, set an expiry date, and then click Add.
The new client secret displays. You cannot view the client secret again. There is both a Value and Secret ID. The Value field is needed for authentication. Copy the Value field and save it in a secure location.
Assign permissions
After you have created your new Microsoft Azure application and obtained the authentication credentials, you must assign the required permissions for the application to access your data. To do so, follow these steps:
-
Navigate to API permissions > Add a permission > Microsoft Graph.
-
Click Application permissions, grant the following permissions, and then click Add permissions.
-
Directory:
Directory.Read.All -
User:
User.Read.All
-
-
Click Add a permission and repeat the same steps for Delegated permissions. Grant the following permissions and click Add permissions.
-
Device:
Device.Read.All -
DeviceManagementApps:
DeviceManagementApps.Read.All -
DeviceManagementConfiguration:
DeviceManagementConfiguration.Read.All -
DeviceManagementManagedDevices:
DeviceManagementManagedDevices.Read.All -
DeviceManagementRBAC:
DeviceManagementRBAC.Read.All -
DeviceManagementServiceConfig:
DeviceManagementServiceConfig.Read.All -
Directory:
Directory.Read.All -
User:
User.Read.All
-
-
Click Grant admin consent for default directory, and then click Yes in the confirmation dialog. Your API permissions should resemble the following:
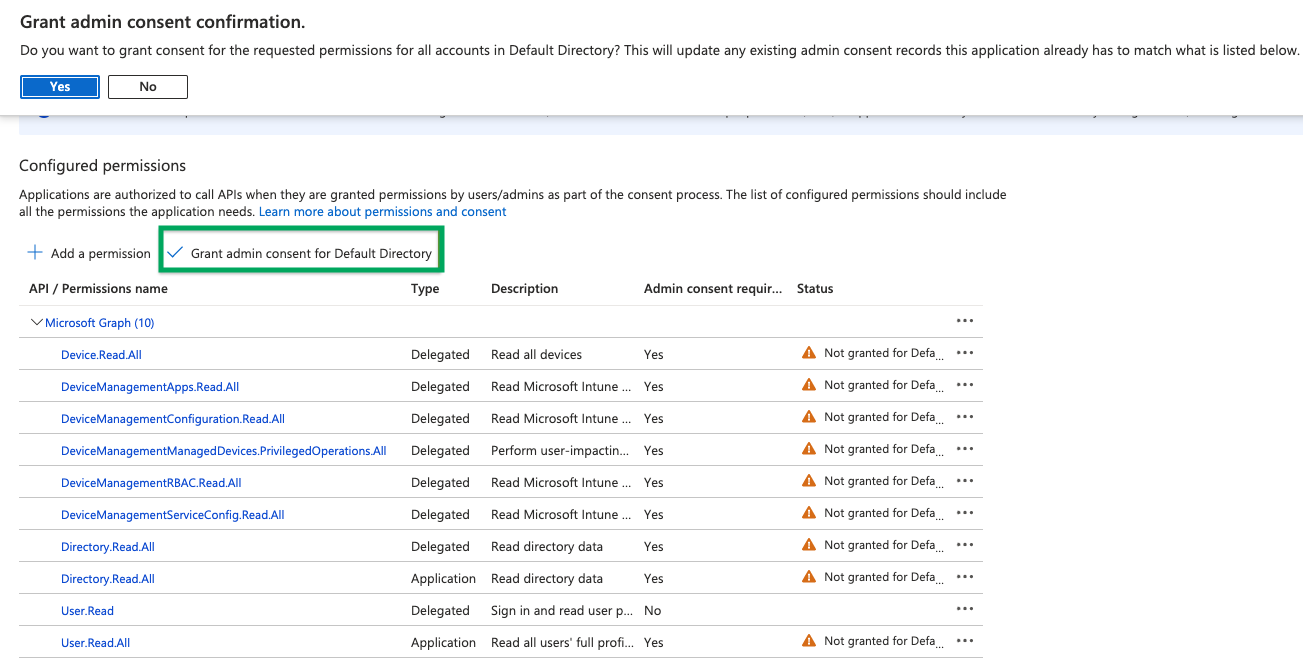
For additional information about Azure AD permissions, see Microsoft Azure documentation.
Types of data to retrieve
The Microsoft Intune connector can retrieve the following types of data from the Microsoft Graph API:
Table 1: Data retrieved from Microsoft Intune
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Host | Yes | Host |
| Mobile Device | Yes | Device |
For detailed steps on how to view the data retrieved from Microsoft Intune in the Brinqa Platform, see How to view your data.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the Microsoft Intune connector:
Table 2: Microsoft Intune DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Host | LAST_SEEN NOT IN LAST 30 Days | 30 days after inactivity | Uses the LAST_SEEN attribute to identify hosts that are inactive within the last 30 days, and then purges the records after 30 days of inactivity. |
| Mobile Device | LAST_SEEN NOT IN LAST 30 Days | 30 days after inactivity | Uses the LAST_SEEN attribute to identify mobile devices that are inactive within the last 30 days, and then purges the records after 30 days of inactivity. |
Operation options
The Microsoft Intune connector supports operation options. See connector operation options for information about how to apply them.
The Microsoft Intune connector supports the filter operation option for both the Host and Mobile device connector objects. Filter is the key and for the supported values, see Microsoft documentation on using the filter query parameter.
APIs
The Microsoft Intune connector uses the Microsoft Graph REST API v1.0. Specifically, it uses the following endpoint:
Table 3: Microsoft Intune API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Host | GET /v1.0/deviceManagement/managedDevices |
| Mobile Device | GET /v1.0/deviceManagement/managedDevices |
Changelog
The Microsoft Intune connector has undergone the following changes:
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
Table 4: Microsoft Intune connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.4.28 | No change. | February 4th, 2026 |
| 3.4.27 | No change. | January 26th, 2026 |
| 3.4.26 | No change. | November 17th, 2025 |
| 3.4.25 | No change. | November 17th, 2025 |
| 3.4.24 | No change. | November 10th, 2025 |
| 3.4.23 | No change. | October 23rd, 2025 |
| 3.4.22 | No change. | October 16th, 2025 |
| 3.4.21 | No change. | October 15th, 2025 |
| 3.4.20 | No change. | September 17th, 2025 |
| 3.4.19 | No change. | August 5th, 2025 |
| 3.4.18 | No change. | August 4th, 2025 |
| 3.4.17 | No change. | August 1st, 2025 |
| 3.4.16 | No change. | June 11th, 2025 |
| 3.4.15 | No change. | May 27th, 2025 |
| 3.4.14 | No change. | May 21st, 2025 |
| 3.4.13 | No change. | May 20th, 2025 |
| 3.4.12 | No change. | April 22nd, 2025 |
| 3.4.11 | Renamed the HOSTNAME attribute to HOST_NAMES on the Host object. | April 7th, 2025 |
| 3.4.10 | No change. | April 1st, 2025 |
| 3.4.9 | No change. | March 26th, 2025 |
| 3.4.8 | No change. | February 12th, 2025 |
| 3.4.7 | No change. | January 28th, 2025 |
| 3.4.5 | No change. | December 19th, 2024 |
| 3.4.4 | No change. | December 6th, 2024 |
| 3.4.3 | No change. | November 28th, 2024 |
| 3.4.2 | No change. | October 7th, 2024 |
| 3.4.1 | Added support for Data lifecycle management to the Host and Mobile Device objects. | September 27th, 2024 |
| 3.4.0 | No change. | September 17th, 2024 |
| 3.3.10 | Code cleanup and general maintenance. | September 4th, 2024 |
| 3.3.9 | No change. | August 27th, 2024 |
| 3.3.8 | No change. | July 24th, 2024 |
| 3.3.7 | No change. | July 24th, 2024 |
| 3.3.6 | No change. | July 8th, 2024 |
| 3.3.5 | No change. | May 20th, 2024 |
| 3.3.4 | No change. | May 20th, 2024 |
| 3.3.3 | No change. | May 20th, 2024 |
| 3.3.2 | No change. | May 9th, 2024 |
| 3.3.1 | No change. | May 3rd, 2024 |
| 3.3.0 | No change. | April 30th, 2024 |
| 3.2.2 | No change. | April 26th, 2024 |
| 3.2.1 | No change. | April 19th, 2024 |
| 3.2.0 | No change. | April 4th, 2024 |
| 3.1.18 | No change. | April 4th, 2024 |
| 3.1.17 | No change. | March 24th, 2024 |
| 3.1.16 | No change. | March 14th, 2024 |
| 3.1.15 | No change. | February 11th, 2024 |
| 3.1.14 | No change. | February 2nd, 2024 |
| 3.1.13 | No change. | January 26th, 2024 |
| 3.1.12 | No change. | January 24th, 2024 |
| 3.1.11 | No change. | October 11th, 2023 |
| 3.1.9 | No change. | July 20th, 2023 |
| 3.1.8 | No change. | July 19th, 2023 |
| 3.1.7 | No change. | May 18th, 2023 |
| 3.1.6 | - Excluded 00000000-0000-0000-0000-000000000000 as a valid Azure Active Directory device ID. - Updated dependencies. | May 9th, 2023 |
| 3.1.5 | Fixed a null pointer exception when there's no filter provided. | May 8th, 2023 |
| 3.1.4 | No change. | April 3rd, 2023 |
| 3.1.3 | No change. | February 22nd, 2023 |
| 3.1.2 | No change. | February 14th, 2023 |
| 3.1.1 | No change. | February 9th, 2023 |
| 3.1.0 | Code cleanup and general maintenance. | February 8th, 2023 |
| 3.0.3 | Code cleanup and general maintenance. | February 7th, 2023 |
| 3.0.2 | No change. | February 4th, 2023 |
| 3.0.1 | Normalized the MAC_ADDRESS attribute in the Computer object. | January 24th, 2023 |
| 3.0.0 | Initial Integration+ release. | January 23rd, 2023 |