CrowdStrike Endpoint Security
As part of our ongoing efforts to align with the broader suite of CrowdStrike solutions, the connector formerly known as CrowdStrike has been renamed to CrowdStrike Endpoint Security. This change was introduced in connector version 3.2.0.
CrowdStrike Endpoint Security is an endpoint protection and threat intelligence tool. You can bring device and security data from CrowdStrike Endpoint Security into Brinqa to construct a unified view of your attack surface and strengthen your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with CrowdStrike Endpoint Security and how to obtain that information from CrowdStrike. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select CrowdStrike Endpoint Security from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate CrowdStrike Endpoint Security with Brinqa:
-
API URL: The CrowdStrike API URL. The default API URL is
https://api.crowdstrike.com.For additional information on the CrowdStrike API URL, see CrowdStrike documentation.
-
Client ID and Client secret: The client ID and client secret associated with the CrowdStrike Endpoint Security account, which must have permissions to log in to the API server and return data.
Generate a CrowdStrike client secret
For the CrowdStrike Endpoint Security connector to use the CrowdStrike API, you must provide a client secret. CrowdStrike Endpoint Security does not allow retrieving the client secret for an existing user, therefore, you must generate a new client secret instead. To do so, follow these steps:
-
Log in to your organization's CrowdStrike Falcon portal as an administrator.
-
From the navigation menu, click Support and resources, and then click API clients and keys.
-
Click Create API client.
The Create API client window displays.
-
Fill out the Client name, Description, and select the appropriate API scopes for the user.
-
Click Create.
Your new client ID, client secret, and recommended Base URL display. You cannot view the client secret again after this. Copy and save it to a secure location.
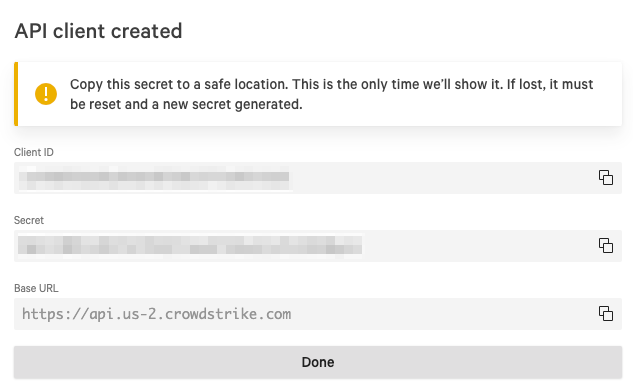
If you do not have permissions to create a client secret, contact your CrowdStrike Endpoint Security administrator. For additional information, see CrowdStrike documentation.
Additional settings
The CrowdStrike Endpoint Security connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 5000. It is not recommended to go over 5000.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 4.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the CrowdStrike API before giving up and reporting a failure. The default setting is 10.
Types of data to retrieve
The CrowdStrike Endpoint Security connector can retrieve the following types of data from the CrowdStrike API:
Table 1: Data retrieved from CrowdStrike
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Device | Yes | Host |
| Evaluation Logic | No | Not mapped |
| Vulnerability | Yes | Vulnerability |
| Vulnerability Definition | Yes | Vulnerability Definition |
Because the Evaluation Logic object is not mapped by the connector, you must manually create or clone a unified data model (UDM) and explicitly map its attributes in your custom UDM if you want to use this data. Please contact your Customer Success Manager for assistance with UDM customization or attribute mapping.
For detailed steps on how to view the data retrieved from CrowdStrike in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Device
Table 2: Device attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| agent_load_flags | Local variable |
| agent_local_time | Local variable |
| agent_version | Local variable |
| bios_manufacturer | Local variable |
| bios_version | Local variable |
| build_number | Local variable |
| chassis_type_desc | Local variable |
| cid | Local variable |
| connection_ip | name, ipAddresses, Local variable |
| connection_mac_address | Local variable |
| default_gateway_ip | ipAddresses, Local variable |
| device_id | uid |
| device_policies_device_control | Local variable |
| device_policies_global_config | Local variable |
| device_policies_prevention | Local variable |
| device_policies_remote_response | Local variable |
| device_policies_sensor_update | Local variable |
| external_ip | name, ipAddresses, publicIpAddress, publicIpAddresses |
| first_login_timestamp | firstLogin |
| first_login_user | firstLoginUser |
| first_seen | firstSeen |
| groups | Local variable |
| hostname | name, hostnames, hostname(normalize), privateDnsName(calculate), privateDnsNames |
| instance_id | instanceId |
| kernel_version | Local variable |
| last_login_timestamp | lastLogin |
| last_login_user | lastLoginUser |
| last_reboot | lastStarted |
| last_seen | lastSeen |
| local_ip | ipAddresses, privateIpAddresses |
| mac_address | macAddresses(normalize) |
| machine_domain | Local variable |
| major_version | Local variable |
| minor_version | Local variable |
| modified_timestamp | sourceLastModified |
| notes | Local variable |
| os_build | Local variable |
| os_product_name | operatingSystem, description, Local variable |
| os_version | operatingSystem, Local variable |
| ou | Local variable |
| platform_id | Local variable |
| platform_name | Local variable |
| product_type_desc | categories |
| provision_status | Local variable |
| reduced_functionality_mode | Local variable |
| release_group | Local variable |
| serial_number | name, serialNumber |
| service_pack_major | Local variable |
| service_pack_minor | Local variable |
| service_provider | Local variable |
| service_provider_account_id | Local variable |
| site_name | Local variable |
| status | status(normalize) |
| system_manufacturer | Local variable |
| system_product_name | description, model |
| tags | tags |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Vulnerability
Table 3: Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| aid | targets |
| app.evaluation_logic.id | Local variable |
| cid | Local variable |
| closed_timestamp | lastFixed |
| created_timestamp | firstFound, sourceCreatedDate |
| cve_exprt_rating | Local variable |
| cve_severity | severity (normalized), sourceSeverity |
| host.host_info.hostname | hostnames |
| host.host_info.host_last_seen_timestamp | lastFound |
| host.host_info.local_ip | ipAddresses |
| id | uid |
| lastUpdated | lastFound |
| remediations | results, recommendation |
| status | status (normalized), statusCategory |
| updated_timestamp | sourceLastModified |
| vid | type, uid |
| vulnerability.closed_timestamp | lastFound |
| vulnerability.updated_timestamp | lastFound |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Vulnerability Definition
Table 4: Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| app_product_name_version | name |
| app_product_name_version() | affected |
| cve_description | summary, description |
| cve_exploit_status | exploitability (calculated) |
| cve_exprt_rating | Local variable |
| cve_published_date | publishedDate |
| cve_references | references |
| cve_severity | severity (normalized), sourceSeverity |
| cve_spotlight_published_date | publishedDate |
| cve_vector | cvss (calculated) |
| remediation | patchAvailable |
| remediations | results, recommendation |
| vid | type, uid |
| vulnerabilityId | name, cveIds, cveRecords |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the CrowdStrike Endpoint Security connector:
Table 5: CrowdStrike Endpoint Security DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Device | LAST_SEEN NOT IN LAST 7 Days | 30 days after inactivity | Uses the LAST_SEEN attribute to identify devices that are inactive within the last 7 days, and then purges the records after 30 days of inactivity. |
| Vulnerability | Inactivity is delegated to the Device object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated device, and then purges the records after 30 days of inactivity. |
CrowdStrike Vulnerability Definitions
CrowdStrike Endpoint Security provides comprehensive visibility into vulnerabilities across your network. However, CrowdStrike does not provide a dedicated API for directly retrieving vulnerability definitions. To bridge this gap, Brinqa has developed a distinct method for generating vulnerability definitions using data from CrowdStrike.
Take the following Vulnerability Definition ID for example:
ae83df32fef2184aaf5075b7e75e8edf_2a49280e6eaa5ebe5fdecdd337fcae14
The Vulnerability Definition ID is composed of two parts: [CrowdStrike Customer ID]_[CrowdStrike Definition ID]
-
CrowdStrike Customer ID (CID): The first part of the Vulnerability Definition ID serves as a unique identifier for your organization, ensuring that the vulnerability data is specific to your CrowdStrike Endpoint Security environment.
-
CrowdStrike Definition ID: The second part of the Vulnerability Definition ID directly corresponds to the unique identifier of the vulnerability in your CrowdStrike Endpoint Security environment.
In the above example, ae83df32fef2184aaf5075b7e75e8edf represents the CrowdStrike Customer ID, and 2a49280e6eaa5ebe5fdecdd337fcae14 is the CrowdStrike Definition ID. This format ensures that each vulnerability definition is accurately tied to the vulnerability identified within your organization's specific context.
Operation options
The CrowdStrike Endpoint Security connector supports the following operation options. See connector operation options for information about how to apply them.
Table 6: CrowdStrike Endpoint Security connector operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Device | product_type_desc | Mobile, Server, Workstation | A comma-separated list of device types. Return only devices of the specified types. | Key: product_type_desc Value: Workstation,Server. This key and value combination only retrieves Workstation and Server devices. |
| status | contained, containment_pending, lift_containment_pending, normal | A comma-separated list of device status values. Return only devices with the specified statuses. | Key: status Value: contained,normal. This key and value combination only retrieves devices with the contained and normal status. | |
| platform_name | Linux, Mac, Windows | A comma-separated list of platform names. Return only devices with the specified platform names. | Key: platform_name Value: Mac,Windows. This key and value combination only retrieves Mac and Windows devices. | |
| last_seen >= | Date in ISO 8601 format (e.g., 2024-07-17T00:00:00Z) | Return only devices that have been seen after the specified date. | Key: last_seen >= Value: 2024-07-01T00:00:00Z. This key and value combination only retrieves devices seen after July 1, 2024. | |
| Vulnerability, Vulnerability Definition | cve.id | Any CVE ID | Return only vulnerabilities associated with the specified CVE IDs. | Key: cve.id Value: CVE-2023-1234. This key and value combination only retrieves vulnerabilities with the CVE-2023-1234 ID. |
| cve.exprt_rating | UNKNOWN, LOW, MEDIUM, HIGH, CRITICAL | A comma-separated list of CVE expert ratings. Return only vulnerabilities with the specified expert ratings. | Key: cve.exprt_rating Value: HIGH,CRITICAL. This key and value combination retrieves only vulnerabilities with high and critical ratings. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The CrowdStrike Endpoint Security connector uses the CrowdStrike API. Specifically, it uses the following endpoints:
Table 7: CrowdStrike Endpoint Security API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Device | GET /devices/entities/devices/v2 |
GET /devices/queries/devices-scroll/v1 | |
| Evaluation Logic | GET /spotlight/combined/evaluation-logic/v1 |
| Vulnerability | GET /spotlight/combined/vulnerabilities/v1 |
| Vulnerability Definition | GET /spotlight/combined/vulnerabilities/v1 |
Changelog
The CrowdStrike Endpoint Security connector has undergone the following changes:
Table 8: CrowdStrike Endpoint Security connector changelog
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
| Version | Description | Date Published |
|---|---|---|
| 3.2.17 | No change. | February 28th, 2026 |
| 3.2.16 | Updated dependencies. | February 28th, 2026 |
| 3.2.15 | Added the LAST_CAPTURED attribute to all objects and refactored code. | February 28th, 2026 |
| 3.2.14 | - Added the remediation title to the RECOMMENDATION attribute on the Vulnerability Definition object. - Added the remediation title to the minimum and recommended remediation details in the RESULTS attribute on the Vulnerability object. - Added a new REMEDIATION_TITLES attribute to the Vulnerability Definition object. | February 13th, 2026 |
| 3.2.13 | Improved data processing performance and reduced storage requirements. | February 5th, 2026 |
| 3.2.12 | Fixed an issue where the connector would fail when processing vulnerabilities with missing CVSS vector data by adding proper null and empty value checks. | January 25th, 2026 |
| 3.2.11 | Enhanced to include CrowdStrike's recommended and minimum remediation details, which are mapped to the Results attribute in the Vulnerability data model. | January 2nd, 2026 |
| 3.2.10 | Added the PRODUCT_NAME_NORMALIZED attribute to the Vulnerability Definition object to retrieve product name from CrowdStrike findings without appending the version. | December 16th, 2025 |
| 3.2.9 | No change. | November 25th, 2025 |
| 3.2.8 | Simplified the LAST_FOUND attribute assignment logic for the Vulnerability object: - For vulnerabilities with an open status, LAST_FOUND is set to the host’s last seen time or the vulnerability’s last updated time. - For closed vulnerabilities, LAST_FOUND is set to the vulnerability’s closed timestamp if available; if not, the attribute is omitted. | October 2nd, 2025 |
| 3.2.7 | No change. | September 30th, 2025 |
| 3.2.6 | Fixed an issue where the LAST_FOUND date timestamp was not populating correctly for the Vulnerability object. As a result, the connector now uses improved logic to more accurately determine when a vulnerability was last observed. For open issues, the timestamp is based on the host’s last seen time or the vulnerability’s update time. For closed issues, the connector uses the vulnerability’s closed or updated timestamp. | September 25th, 2025 |
| 3.2.5 | No change. | September 12th, 2025 |
| 3.2.4 | Streamlined how the connector processes and stores data by leveraging each object’s unique attributes for optimized retrieval. These improvements make handling large data volumes more efficient and speed up Vulnerability Definition synchronization. Also reverted the changes introduced in version 3.2.3, as they impacted performance and the data is already present in a separate object (Evaluation Logic). | August 21st, 2025 |
| 3.2.3 | Replaced the EVALUATION_LOGIC attribute on the Vulnerability object with EVALUATION_RESULTS. The previous attribute only collected evaluation logic IDs. The new attribute collects the full evaluation logic details provided by CrowdStrike. | July 21st, 2025 |
| 3.2.2 | - Fixed an issue where the Vulnerability Definition object sync was failing due to a NoSuchFileException error. - Fixed an issue where FIRST_FOUND dates were being set after LAST_FOUND dates on vulnerabilities. This was caused by incorrect handling of missing or null scan values in the source data. | June 4th, 2025 |
| 3.2.1 | No change. | May 23rd, 2025 |
| 3.2.0 | The CrowdStrike connector has been renamed to "CrowdStrike Endpoint Security". If you were using the CrowdStrike connector, install the new connector, create a new integration, and reconfigure it accordingly. For additional information or assistance, please contact your Brinqa Support team. | March 12th, 2025 |
| 3.1.12 | - Fixed an issue where the TARGETS attribute on the Vulnerability object used a different UID format than the UID on the Host object, preventing vulnerabilities from being correctly associated with their respective hosts. - Renamed the HOSTNAME attribute to HOST_NAMES on the Vulnerability object. | January 27th, 2025 |
| 3.1.11 | Fixed an issue where the number of vulnerabilities synced was smaller than expected due to the connector only retrieving vulnerabilities with evaluation logic, according to CrowdStrike. | November 30th, 2024 |
| 3.1.10 | Moved the EVALUATION_LOGIC attribute from the Vulnerability Definition object to the Vulnerability object to reflect changes specific to each vulnerability. | September 8th, 2024 |
| 3.1.9 | Added the EVALUATION_LOGIC attribute to the Vulnerability Definition object to retrieve detailed evidence and contextual information from CrowdStrike findings. | August 30th, 2024 |
| 3.1.8 | Added support for Data lifecycle management to the Device and Vulnerability objects. | August 27th, 2024 |
| 3.1.7 | Added the AFFECTED attribute to the Vulnerability Definition object. | July 8th, 2024 |
| 3.1.6 | Changed the DEVICE_CONTROL_POLICY_ID attribute type on the Device object from boolean to string. | March 20th, 2024 |
| 3.1.5 | Fixed an issue where the Vulnerability and Vulnerability Definition syncs were failing. | March 4th, 2024 |
| 3.1.4 | Updated the method for setting the LAST_FOUND attribute in the Vulnerability object. | February 16th, 2024 |
| 3.1.3 | Code cleanup and general maintenance. | February 5th, 2024 |
| 3.1.2 | The connector now uses the LAST_SEEN_WITHIN attribute for the Vulnerability object sync. | February 5th, 2024 |
| 3.1.1. | Fixed an issue where the connector sync was timing out. | February 5th, 2024 |
| 3.1.0 | Changed the strategy of generating Vulnerability Definition records to use part of a CrowdStrike Vulnerability ID, which is unique per vulnerability type. See CrowdStrike Vulnerability Definitions for details. | February 5th, 2024 |
| 3.0.24 | Enhanced to display remediation information in the Results field of vulnerabilities. | February 2nd, 2024 |
| 3.0.23 | Code cleanup and general maintenance. | January 29th, 2024 |
| 3.0.22 | Added a new operation option to let you define your own own prefix if using multiple CrowdStrike sources: definitionUidPrefix. The default prefix is CSID. | January 18th, 2024 |
| 3.0.21 | Enhanced to update the Recommendation field when creating Vulnerability Definition objects. | December 27th, 2023 |
| 3.0.20 | Fixed an issue where Recommendation data from the Vulnerability Definition object was not being synced. | December 17th, 2023 |
| 3.0.19 | Fixed a parse error that would occur when syncing Device objects. | November 8th, 2023 |
| 3.0.18 | Improved the performance of the Vulnerability Definition object sync. | October 5th, 2023 |
| 3.0.17 | - Added some optional attributes in the Device object:
| August 21st, 2023 |
| 3.0.16 | Fixed an issue where data integration syncs took much longer than the previous version. | August 15th, 2023 |
| 3.0.15 | Added an extra line after the vulnerable product version field to improve the readability. | July 26th, 2023 |
| 3.0.14 | - Enhanced to list all vulnerable products in the Result field of vulnerabilities. - Updated dependencies. | July 26th, 2023 |
| 3.0.13 | Implemented a solution to handle parallel data integration syncs. | June 20th, 2023 |
| 3.0.12 | - Added the EX_PRT_RATING attribute to the Vulnerability object. - Prioritized EX_PRT_RATING from open vulnerabilities. | June 15th, 2023 |
| 3.0.11 | Added the PATCH_AVAILABLE attribute to the Vulnerability Definition object. | April 21st, 2023 |
| 3.0.10 | - Added the PRIVATE_DNS_NAME attribute to the Device object. - Normalized hostnames. | March 22nd, 2023 |
| 3.0.9 | Added the SERIAL_NUMBER attribute to the Device object. | March 14th, 2023 |
| 3.0.8 | Code cleanup and general maintenance. | February 26th, 2023 |
| 3.0.7 | - Fixed an issue where the Vulnerability Definition object sync was failing. - Added some missing attributes. | February 3rd, 2023 |
| 3.0.6 | Code cleanup and general maintenance. | February 2nd, 2023 |
| 3.0.5 | Code cleanup and general maintenance. | January 25th, 2023 |
| 3.0.4 | Code cleanup and general maintenance. | January 18th, 2023 |
| 3.0.3 | Fixed an issue where the ID reference on the Vulnerability Definition object was incorrect. | December 19th, 2022 |
| 3.0.2 | The Device API endpoint now uses v2 of the Crowdstrike API. | December 19th, 2022 |
| 3.0.1 | The connector now filters out expired vulnerabilities. | December 19th, 2022 |
| 3.0.0 | Initial Integration+ release. | December 18th, 2022 |