Adaptive Shield
Adaptive Shield is an identity management tool that helps remediate SaaS configuration issues. You can bring alert, integrated user, integration, and security check data from Adaptive Shield into Brinqa to construct a unified view of your attack surface, thus strengthening your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Adaptive Shield and how to obtain that information from Adaptive Shield. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Adaptive Shield from the Connector dropdown. If you cannot find the connector in the dropdown, make sure you have installed it first. You must provide the following information to authenticate Adaptive Shield with Brinqa:
-
API URL: The Adaptive Shield API URL. The API URL depends on the region where your Adaptive Shield environment is deployed:
-
US:
https://api.adaptive-shield.com -
EU:
https://eu.api.adaptive-shield.com
-
-
Access token: The API key associated with the Adaptive Shield account, which must have permissions to log in to the API server and return data.
The API key inherits the scope and permissions of the associated Adaptive Shield user account, meaning it can only retrieve data that the user account can view in the Adaptive Shield UI.
Generate an Adaptive Shield API key
For the Adaptive Shield connector to retrieve data from the Adaptive Shield API, you must provide an API key. To do so, follow these steps:
-
Log in to your organization's Adaptive Shield portal as an administrator.
-
Navigate to your user profile and click User Settings
-
Click the API tab and then click Generate new key.
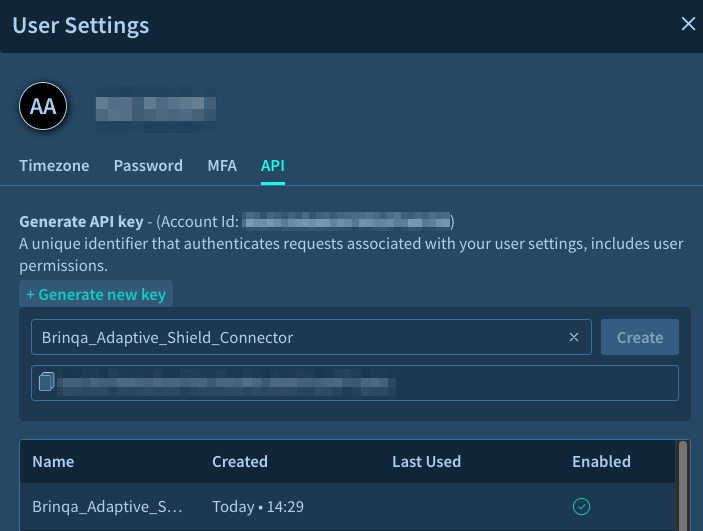
-
Provide a Name for the key, and then click Create.
Your new API key displays. You can not view the key again after this. Copy and save it to a secure location.
If you do not have permissions to generate an API key, contact your Adaptive Shield administrator. For additional information, see Adaptive Shield documentation.
Additional settings
The Adaptive Shield connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 4.
-
Maximum retries : The maximum number of times that the integration attempts to connect to the Adaptive Shield API before giving up and reporting a failure. The default setting is 5.
Types of data to retrieve
The Adaptive Shield connector can retrieve the following types of data from the Adaptive Shield API:
Table 1: Data retrieved from Adaptive Shield
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Alert | Yes | Alert |
| Alert Definition | Yes | Alert Definition |
| Compliance Control | No | Not mapped |
| Device | No | Device |
| Host | No | Host |
| Integrated User | Yes | Person |
| Integration | Yes | Cloud Resource |
| Violation | Yes | Violation |
| Violation Definition | Yes | Violation Definition |
For detailed steps on how to view the data retrieved from Adaptive Shield in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Alert
Table 2: Alert attribute mappings
| Source Field Name | Maps to Attribute | Maps to UDM |
|---|---|---|
| account_id | Local variable | Not mapped |
| affected_diff | Local variable | Not mapped |
| alert_type | category | Alert Definition |
| description | description | Alert Definition |
| id | uid | Alert |
| integration.id | targets | Alert |
| is_archived | Local variable | Not mapped |
| new_affected_count | Local variable | Not mapped |
| security_check_api_link | Local variable | Not mapped |
| source | Local variable | Not mapped |
| source_id | type | Alert |
| source_id | uid | Alert Definition |
| timestamp | sourceCreatedDate | Alert |
| user_who_archived | Local variable | Not mapped |
Device
Table 3: Device attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| account_id | Local variable |
| device_name | name |
| globally_compliant | Local variable |
| globally_managed | Local variable |
| id | uid |
| last_seen | lastSeen |
| os | Local variable |
| os_version | Local variable |
| platform | Local variable |
| reporters.integration_id | Local variable |
| user_email | emails |
Host
Table 4: Host attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| account_id | Local variable |
| device_name | name |
| globally_compliant | Local variable |
| globally_managed | Local variable |
| id | uid |
| last_seen | lastSeen |
| mac_address_list | macAddresses |
| os | Local variable |
| os_version | Local variable |
| platform | Local variable |
| reporters.integration_id | Local variable |
| user_email | emails |
Integrated User
Table 5: Integrated User attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| account_id | Local variable |
| company | Local variable |
| country | Local variable |
| department | Local variable |
| domain | Local variable |
| emails | |
| enabled | Local variable |
| exposures | Local variable |
| exposures_total | Local variable |
| full_name | name |
| integrations | Local variable |
| integrations_total | Local variable |
| login_names | Local variable |
| roles | Local variable |
| title | description |
| user_item_identity | uid |
Integration
Table 6: Integration attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| account_id | Local variable |
| alias | Local variable |
| created_time | sourceCreatedDate |
| enabled | Local variable |
| id | uid |
| integration_status | status |
| issues | Local variable |
| last_run | lastScanned |
| saas_id | Local variable |
| saas_name | Local variable |
Violation
Table 7: Violation attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| account_id | Local variable |
| affected | Local variable |
| base_check_id | Local variable |
| created_by | Local variable |
| creation_date | sourceCreatedDate, firstFound |
| dismiss_expiration_date | Local variable |
| dismiss_reason | Local variable |
| integration_id | targets |
| is_global | Local variable |
| name | type |
| saas_name | Local variable |
| status | status, sourceStatus, statusCategory |
| status_last_changed_date | sourceLastModified |
| status_reason | Local variable |
| user_who_dismissed | Local variable |
| id | uid, Local variable |
Violation Definition
Table 8: Violation Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| compliance.control_code | Local variable |
| details | description |
| impact | severity (normalized), severityScore, sourceSeverity |
| name | uid, name |
| remediation_plan | recommendation |
| security_check_type | categories |
| security_domain | categories |
| status_reason | description |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Operation options
The Adaptive Shield connector supports the following operation options. See connector operation options for information about how to apply them.
Table 9: Adaptive Shield operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Compliance Control | include_compliance | true, false | If set to true, control codes and compliance data are included.This may impact performance due to additional API calls. | Key: include_compliance, Value: true.Retrieves control and compliance data associated with violations. |
| Device | integration_id | Any Adaptive Shield integration ID string | A comma-separated list of integration IDs. Use this option to limit the retrieved devices by their associated integration IDs. | Key: integration_id, Value: 6720f0e4cb44f5a5d7a6d1ef,6720f0e4cb44f5a5d7a6d1ef.Only retrieves devices with these integration IDs. |
| Host | integration_id | Any Adaptive Shield integration ID string | A comma-separated list of integration IDs. Use this option to limit the retrieved hosts by their associated integration IDs. | Key: integration_id, Value: 6720f0e4cb44f5a5d7a6d1ef,6720f0e4cb44f5a5d7a6d1ef.Only retrieves hosts with these integration IDs. |
| Violation | include_compliance | true, false | If set to true, control codes and compliance data are included.This may impact performance due to additional API calls. | Key: include_compliance, Value: true.Retrieves control and compliance data associated with violations. |
| Violation Definition | include_compliance | true, false | If set to true, control codes and compliance data are included.This may impact performance due to additional API calls. | Key: include_compliance, Value: true.Retrieves control and compliance data associated with violation definitions. |
APIs
The Adaptive Shield connector uses the Adaptive Shield API v1. Specifically, it uses the following endpoints:
Table 10: Adaptive Shield API Endpoints
| Connector Object | API Endpoint |
|---|---|
| Alert | GET /api/v1/accounts |
GET /api/v1/accounts/{accountId}/alerts | |
| Alert Definition | GET /api/v1/accounts |
GET /api/v1/accounts/{accountId}/alerts | |
| Compliance Control | GET /api/v1/accounts/{accountId}/security_checks/{securityCheckId}/compliance |
| Device | GET /api/v1/accounts/{accountId}/device_inventory |
| Host | GET /api/v1/accounts/{accountId}/device_inventory |
| Integrated User | GET /api/v1/accounts |
GET /api/v1/accounts/{accountId}/user_inventory | |
| Integration | GET /api/v1/accounts |
GET /api/v1/accounts/{accountId}/integrations | |
| Violation | GET /api/v1/accounts |
GET /api/v1/accounts/{accountId}/security_checks | |
GET /api/v1/accounts/{accountId}/security_checks/{securityCheckId}/affected | |
GET /api/v1/accounts/{accountId}/security_checks/{securityCheckId}/compliance | |
| Violation Definition | GET /api/v1/accounts |
GET /api/v1/accounts/{accountId}/security_checks | |
GET /api/v1/accounts/{accountId}/security_checks/{securityCheckId}/affected | |
GET /api/v1/accounts/{accountId}/security_checks/{securityCheckId}/compliance |
Changelog
The Adaptive Shield connector has undergone the following changes:
Table 11: Adaptive Shield connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.0.6 | Fixed an issue where duplicate Violation records were being created. This was caused by including fields such as DISMISS_EXPIRATION_DATE and DISMISS_REASON when generating the UID. The Violation object now uses only the ENTITY_NAME, INTEGRATION_ID, and SECURITY_CHECK_ID attributes to generate the UID. It is strongly recommended to purge existing data associated with this connector before updating to v3.0.6. | September 5th, 2025 |
| 3.0.5 | Fixed an issue where the Violation and Violation Definition object syncs were failing. | August 15th, 2025 |
| 3.0.4 | - The connector now retrieves the Compliance Control, Device, and Host objects from Adaptive Shield. - Added a new additional setting to help manage API throttling: Maximum retries. - The STATUS_REASON attribute on the Violation Definition now maps to the Description field in Brinqa. - The connector now supports operation options. - Added the CONTROL_CODES attribute to the Violation Definition object. - The Violation object has been enhanced to create distinct violations based on the affected data from Adaptive Shield. | July 30th, 2025 |
| 3.0.3 | Improved the description and recommendation fields on the Violation Definition object. | June 10th, 2025 |
| 3.0.2 | Fixed an issue where the Violation object sync was failing due to exceeding the API rate limit ("You cannot make more than 100 requests per minute"). Added rate limiting to prevent these errors. | May 7th, 2025 |
| 3.0.1 | Fixed an issue where the Violation object sync was failing. | April 7th, 2025 |
| 3.0.0 | Initial Integration+ release. | February 11th, 2025 |