Amazon Inspector
Amazon Inspector by Amazon Web Services (AWS) is a security assessment tool that scans your AWS environments to identify vulnerabilities and deviations from best practices. You can bring AWS EC2 instance, cloud, code, and other security data from Amazon Inspector into Brinqa to gain a comprehensive view of your AWS security posture, thus strengthening your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Amazon Inspector and how to obtain that information from Amazon. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Amazon Inspector from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Amazon Inspector with Brinqa:
-
Access key ID and Secret access key: The access keys associated with the Amazon Inspector account, which must have permissions to log in to the API server and return data. For additional information, see Create an IAM user for Amazon Inspector access.
-
Default region: The AWS region for the Amazon Inspector connector. If not specified, the connector uses the AWS default region provider chain to automatically determine the most appropriate region. This ensures that the connector adheres to the recommended AWS practices for region selection. For additional information on AWS regions, refer to the AWS documentation.
-
Assume role: The Amazon Resource Name (ARN) for the role that the connector assumes when accessing AWS services, which must have permissions to log in to the API server and return data.
Create an IAM user for Amazon Inspector access
For the Amazon Inspector connector to interact with the Amazon Inspector API, you must provide specific AWS credentials and permissions. To do so, follow these steps:
-
Log in to your organization's AWS Management Console as an administrator.
-
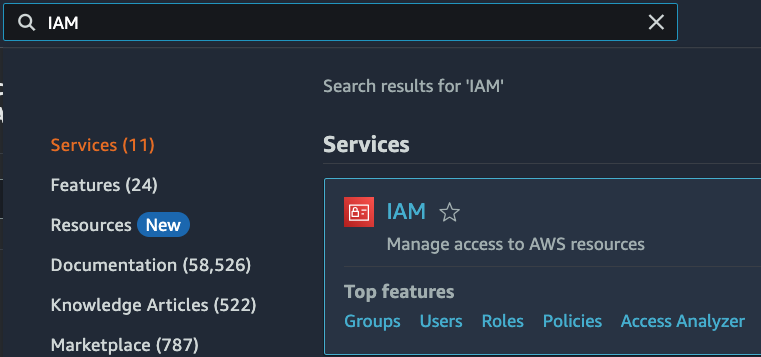
Navigate to the Identity and Access Management (IAM) dashboard.
-
From the navigation pane under Access management, click Users, and then click Create user.
-
Provide a User name, leave the Provide user access to AWS Management Console option unchecked, and then click Next.
-
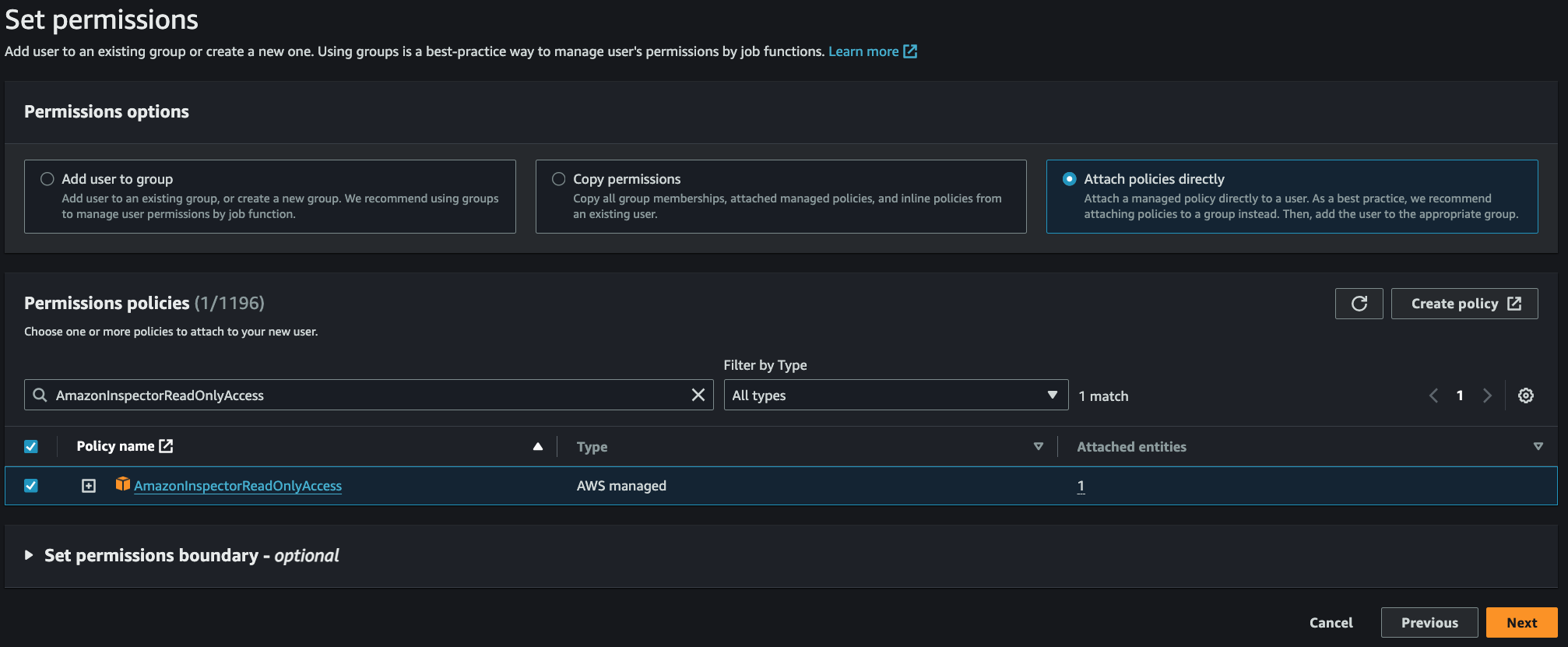
Click the Attach policies directly option, search for and select the AmazonInspectorReadOnlyAccess permission.
-
Click Next and then click Create user.
The Users page displays and the new IAM user is available in the Users table.
If you do not have permissions to create a new IAM user, contact your AWS administrator. For additional information, see AWS documentation.
Obtain Amazon Inspector access keys
To obtain the access keys required for the integration, follow these steps:
-
Log in to your organization's AWS Management Console as an administrator.
-
Navigate to the IAM dashboard.
-
From the navigation pane under Access management, click Users.
-
Choose the IAM user you created in the earlier steps.
-
Click the Security credentials tab and then click Create access key.
-
Select the Application running outside AWS use case and then click Next.
-
Provide a description and then click Create access key.
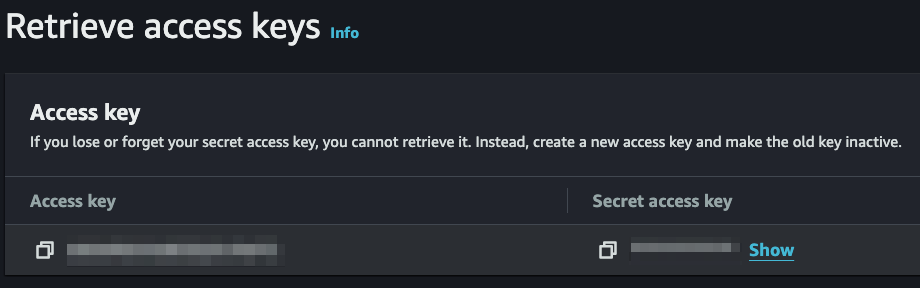
Your new access keys display. You cannot view the keys again after this. Copy and save them to a safe and secure location.
noteIf you do not have permissions to create access keys, contact your AWS administrator. For additional information, see AWS documentation.
Create a role and assign permissions
After obtaining the Amazon Inspector access keys, the next step is to create a role and obtain the ARN that is required for the integration. To do so, follow these steps:
-
From the IAM dashboard, click Roles, and then click Create role.
-
Choose AWS account for the Trusted entity type and click Next.
-
Search for and select the AmazonInspectorReadOnlyAccess permission from the list of permissions and click Next.
-
Assign a name and description and then click Create role.
-
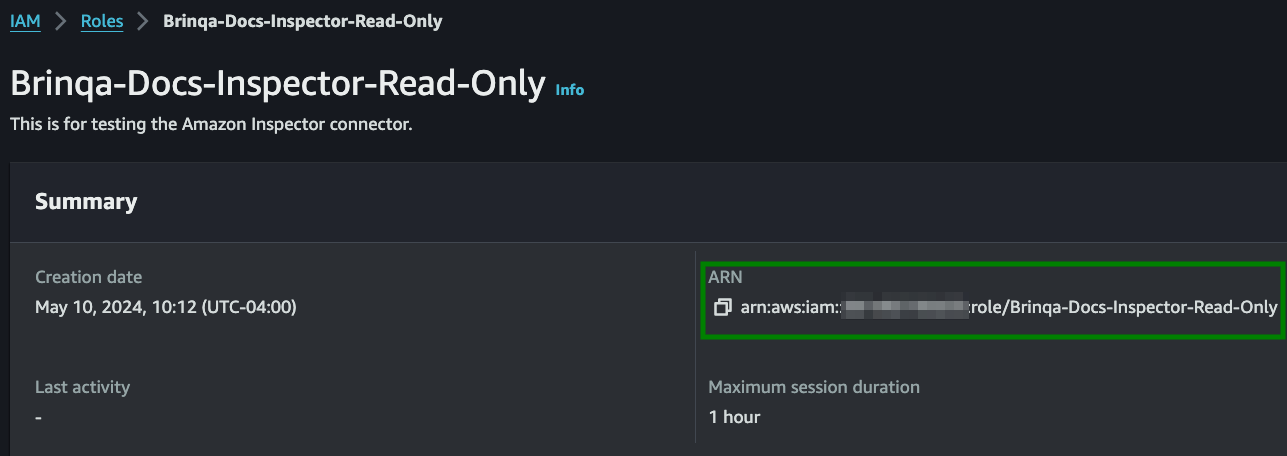
Back on the Roles page, click the new role and copy the value in the ARN field as shown below. The ARN, along with the access key ID and secret access key, are required for authentication in the integration configuration:
 note
noteIf you do not have the permissions to create roles, contact your AWS administrator. For additional information, see AWS documentation.
Additional settings
The Amazon Inspector connector contains an additional option for specific configuration:
-
Session duration: The duration, in seconds, for the assumed role session. This determines the time period during which the credentials issued by the assumed role remain valid. The default setting is 900 seconds, or 15 minutes.
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 4.
Types of data to retrieve
The Amazon Inspector connector can retrieve the following types of data from the AWS SDK:
Table 1: Data retrieved from Amazon Inspector
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| AWS EC2 Instance | Yes | Host |
| Cloud Resource | Yes | Cloud Resource |
| Code Vulnerability | Yes | Static Code Finding |
| Code Vulnerability Definition | Yes | Static Code Finding Definition |
| Network Reachability Finding | Yes | Violation |
| Network Reachability Finding Definition | Yes | Violation Definition |
| Package Vulnerability | Yes | Vulnerability |
| Package Vulnerability Definition | Yes | Vulnerability Definition |
For detailed steps on how to view the data retrieved from Amazon Inspector in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
AWS EC2 Instance
Table 2: AWS EC2 Instance attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CLOUD_ACCOUNT_ID | cloudAccountID |
| CATEGORIES | categories |
| IMAGE_ID | image |
| IAM_INSTANCE_PROFILE_ARN | Local variable |
| IN_USE_COUNT | Local variable |
| IP_V4_ADDRESSES | ipAddresses, privateIpAddresses, publicIpAddresses |
| IP_V6_ADDRESSES | ipAddresses, privateIpAddresses, publicIpAddresses |
| KEY_NAME | Local variable |
| LAUNCHED_AT | Local variable |
| LAST_USED | lastUsed |
| NAME | name |
| REGION | region |
| SUBNET_ID | Local variable |
| TAGS | tags |
| TYPE | type |
| UID | uid |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Cloud Resource
Table 3: Cloud Resource attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ARCHITECTURE | Local variable |
| AUTHOR | Local variable |
| CLOUD_ACCOUNT_ID | cloudAccountID |
| CATEGORIES | categories |
| CODE_SHA_256 | Local variable |
| ECR_CONTAINER_IMAGE_PLATFORM | Local variable |
| EXECUTION_ROLE_ARN | Local variable |
| FUNCTION_NAME | Local variable |
| IMAGE_HASH | Local variable |
| IN_USE_COUNT | Local variable |
| LAMBDA_FUNCTION_VPC_ID | Local variable |
| LAST_MODIFIED_AT | sourceLastModified |
| LAST_USED | lastUsed |
| LAYERS | Local variable |
| NAME | name |
| PACKAGE_TYPE | Local variable |
| PUSHED_AT | sourceCreatedDate |
| REPOSITORY_NAME | repository |
| REGION | region |
| REGISTRY | registry |
| RUN_TIME | Local variable |
| SECURITY_GROUP_IDS | Local variable |
| SUBNET_IDS | Local variable |
| TAGS | tags |
| UID | uid |
| VERSION | currentVersion |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Code Vulnerability
Table 4: Code Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORIES | categories |
| CLOUD_ACCOUNT_ID | cloudAccountId |
| FIRST_FOUND | firstFound |
| INSPECTOR_SCORE | Local variable |
| LAST_FOUND | lastFound |
| PATH | path |
| SOURCE_STATUS | sourceStatus |
| STATUS | status |
| STATUS_CATEGORY | statusCategory |
| TARGETS | targets |
| TYPE | type |
| UID | uid |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Code Vulnerability Definition
Table 5: Code Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORIES | categories |
| CLOUD_ACCOUNT_ID | cloudAccountId |
| CWE_IDS | cweIds |
| DETECTOR_ID | Local variable |
| DETECTOR_NAME | Local variable |
| FIRST_FOUND | firstFound |
| INSPECTOR_SCORE | Local variable |
| LAST_FOUND | lastFound |
| RULE_ID | Local variable |
| SOURCE_STATUS | sourceStatus |
| STATUS | status |
| STATUS_CATEGORY | statusCategory |
| TAGS | tags |
| TARGETS | targets |
| TYPE | type |
| UID | uid |
| WEAKNESSES | weaknesses |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Network Reachability Finding
Table 6: Network Reachability Finding attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORIES | categories |
| CLOUD_ACCOUNT_ID | cloudAccountId |
| FIRST_FOUND | firstFound |
| INSPECTOR_SCORE | Local variable |
| LAST_FOUND | lastFound |
| PATH | path |
| PORT | port |
| SOURCE_STATUS | sourceStatus |
| STATUS | status |
| STATUS_CATEGORY | statusCategory |
| TARGETS | targets |
| TYPE | type |
| UID | uid |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Network Reachability Finding Definition
Table 7: Network Reachability Finding Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORIES | categories |
| CLOUD_ACCOUNT_ID | cloudAccountId |
| FIRST_FOUND | firstFound |
| INSPECTOR_SCORE | Local variable |
| LAST_FOUND | lastFound |
| SOURCE_STATUS | sourceStatus |
| STATUS | status |
| STATUS_CATEGORY | statusCategory |
| TARGETS | targets |
| TYPE | type |
| UID | uid |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Package Vulnerability
Table 8: Package Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| AFFECTED | affected |
| CATEGORIES | categories |
| CLOUD_ACCOUNT_ID | cloudAccountId |
| FIRST_FOUND | firstFound |
| INSPECTOR_SCORE | Local variable |
| LAST_FOUND | lastFound |
| SOURCE_STATUS | sourceStatus |
| STATUS | status |
| STATUS_CATEGORY | statusCategory |
| TARGETS | targets |
| TYPE | type |
| UID | uid |
| VULNERABILITY_ID | Local variable |
| VULNERABILITY_SOURCE | Local variable |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Package Vulnerability Definition
Table 9: Package Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| CATEGORIES | categories |
| CLOUD_ACCOUNT_ID | cloudAccountId |
| CVSS_V2_AC | cvssV2Ac |
| CVSS_V2_AI | cvssV2Ai |
| CVSS_V2_AU | cvssV2Au |
| CVSS_V2_AV | cvssV2Av |
| CVSS_V2_BASE_SCORE | cvssV2BaseScore |
| CVSS_V2_CI | cvssV2Ci |
| CVSS_V2_E | cvssV2E |
| CVSS_V2_II | cvssV2Ii |
| CVSS_V2_RC | cvssV2Rc |
| CVSS_V2_RL | cvssV2Rl |
| CVSS_V2_SEVERITY | cvssV2Severity |
| CVSS_V2_VECTOR | cvssV2Vector |
| CVSS_V3_AC | cvssV3Ac |
| CVSS_V3_AI | cvssV3Ai |
| CVSS_V3_AV | cvssV3Av |
| CVSS_V3_BASE_SCORE | cvssV3BaseScore |
| CVSS_V3_CI | cvssV3Ci |
| CVSS_V3_E | cvssV3E |
| CVSS_V3_II | cvssV3Ii |
| CVSS_V3_PR | cvssV3Pr |
| CVSS_V3_RC | cvssV3Rc |
| CVSS_V3_RL | cvssV3Rl |
| CVSS_V3_SEVERITY | cvssV3Severity |
| CVSS_V3_UI | cvssV3Ui |
| CVSS_V3_VECTOR | cvssV3Vector |
| FIRST_FOUND | firstFound |
| INSPECTOR_SCORE | Local variable |
| LAST_FOUND | lastFound |
| SOURCE_STATUS | sourceStatus |
| STATUS | status |
| STATUS_CATEGORY | statusCategory |
| TARGETS | targets |
| TYPE | type |
| UID | uid |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Operation options
The Amazon Inspector connector supports the following operation options. See connector operation options for information about how to apply them.
Table 9: Amazon Inspector operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Code Vulnerability, Network Reachability Finding, Package Vulnerability | severity | UNTRIAGED, INFORMATIONAL, LOW, MEDIUM, HIGH, CRITICAL | A comma-separated list of severity levels. Limit retrieved findings by the specified severity levels, as determined by Amazon Inspector. | Key: severity Value: CRITICAL,HIGH. This key and value combination only retrieves findings with a severity of CRITICAL or HIGH. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The Amazon Inspector connector uses the AWS SDK version 2.31.7.
Changelog
The Amazon Inspector connector has undergone the following changes:
Table 10: Amazon Inspector connector changelog
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
| Version | Description | Date Published |
|---|---|---|
| 3.0.19 | No change. | December 26th, 2025 |
| 3.0.18 | Added the IN_USE_COUNT and LAST_USED attributes to the AWS EC2 Instance and Cloud Resource objects. These attributes can help prioritize vulnerabilities based on how frequently an Amazon ECR image is deployed and when it was last used. | September 22nd, 2025 |
| 3.0.17 | Updated the connector icon. This change only affects the connector icon and does not impact functionality. You can update without making any changes to your existing configurations. | August 5th, 2025 |
| 3.0.16 | No change. | August 5th, 2025 |
| 3.0.15 | Fixed an issue where the full ARN was not being populated for the Cloud Resource and EC2 Instance objects. As a result, the CLOUD_ACCOUNT_ID attribute has been added to the AWS EC2 Instance and Cloud Resource objects. | July 29th, 2025 |
| 3.0.14 | - Improved sync performance for the Package Vulnerability object. - Added a new operation option on the Code Vulnerability, Network Reachability Finding, and Package Vulnerability objects to help filter by severity level: severity | June 4th, 2025 |
| 3.0.13 | - Fixed an issue where some Package Vulnerabilities associated with AWS EC2 instances were not displaying in Brinqa. - Updated the AWS SDK version from 2.25.6 to 2.31.7. | March 25th, 2025 |
| 3.0.12 | No change. | March 25th, 2025 |
| 3.0.11 | No change. | October 28th, 2024 |
| 3.0.10 | - Fixed an issue where CVE identifiers were not correctly mapped on the Vulnerability Definition object. - Fixed an issue where the SEVERITY and SOURCE_SEVERITY attributes were incorrectly mapped on the Code Vulnerability Definition and Package Vulnerability Definition objects. | September 27th, 2024 |
| 3.0.9 | Removed the PLATFORM and VPC_ID attributes from the AWS EC2 Instance object. | August 6th, 2024 |
| 3.0.8 | Added the following attributes to the AWS EC2 Instance object:
| July 19th, 2024 |
| 3.0.7 | Fixed some attribute type data mismatches. | June 5th, 2024 |
| 3.0.6 | Fixed an issue where syncs were resulting in a "No locks available" error. | May 29th, 2024 |
| 3.0.5 | Initial Integration+ release. | March 13th, 2024 |