Aqua SaaS
Aqua SaaS is a container security tool that provides workload protection and security for containers, Kubernetes, and serverless applications. You can bring container, host, and security data from Aqua into Brinqa to construct a unified view of your attack surface, thus strengthening your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Aqua SaaS and how to obtain that information from Aqua. See create a data integration for step-by-step instructions on setting up the integration.
The Aqua SaaS connector differs from the Aqua Enterprise connector only in its authentication method. Instead of a username and password, the Aqua SaaS connector uses an API key and API secret. The underlying APIs, data retrieved, operation options, and data mappings remain the same as the Aqua Enterprise connector.
Required connection settings
When setting up a data integration, select Aqua SaaS from the Connector dropdown. If you cannot find the connector in the dropdown, make sure you have installed it first. You must provide the following information to authenticate Aqua SaaS with Brinqa:
-
API URL: Your organization’s Aqua SaaS API URL. If the URL is unknown, you can retrieve it by contacting Aqua Support. The default URL format is
https://<server_name>.cloud.aquasec.com. -
Auth URL: The Aqua API Server URL, specific to the region of your Aqua SaaS environment. The default URL format is
https://<region>.api.cloudsploit.com. Replace<region>with the specific region of your Aqua API server. If your server is in the US, the URL would behttps://api.cloudsploit.com/.The following table lists the Aqua SaaS login URL for each region. Please refer to Aqua Platform documentation for accuracy:
Table 1: Aqua login URLs
Region URL US https://api.cloudsploit.com/EU https://eu-1.api.cloudsploit.com/Singapore https://asia-1.api.cloudsploit.com/Sydney https://ap-2.api.cloudsploit.com/ -
API key and API secret: The API credentials associated with the Aqua SaaS account, which must have permissions to log in to the API server and return data. For additional information, see Generate Aqua SaaS API credentials.
Generate Aqua SaaS API credentials
For the Aqua SaaS connector to retrieve data from the Aqua API, you must provide API credentials with the necessary permissions. To do so, follow these steps:
-
Log in to your organization's Aqua portal as an administrator.
-
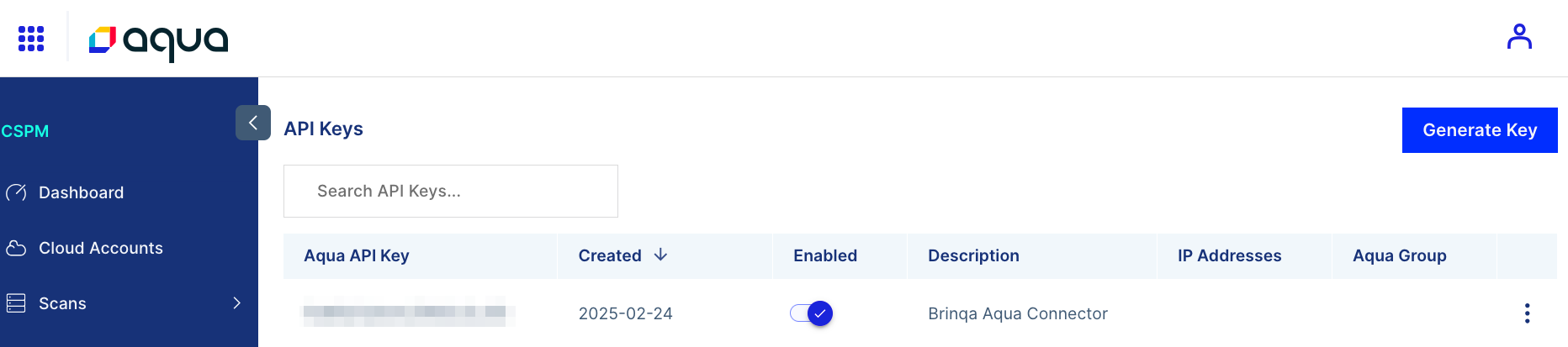
Navigate to Account Management > Settings > API Keys.
-
Click Generate Key.
-
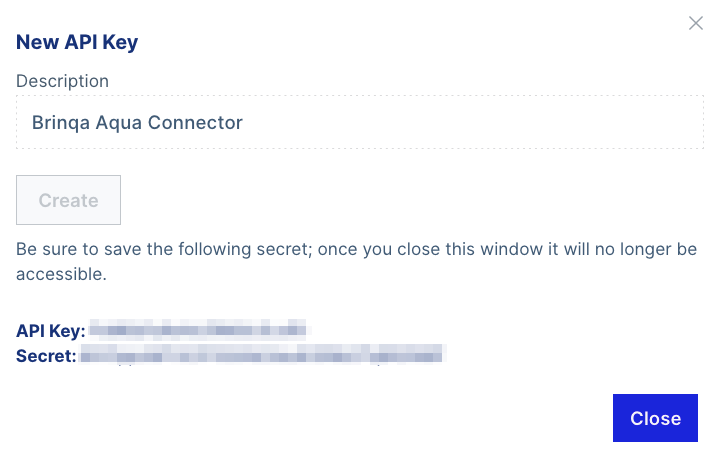
Provide a Description for the API key, and then click Create.
Your API key and API secret display. You cannot view the API secret again after this. Copy and save it to a secure location.
-
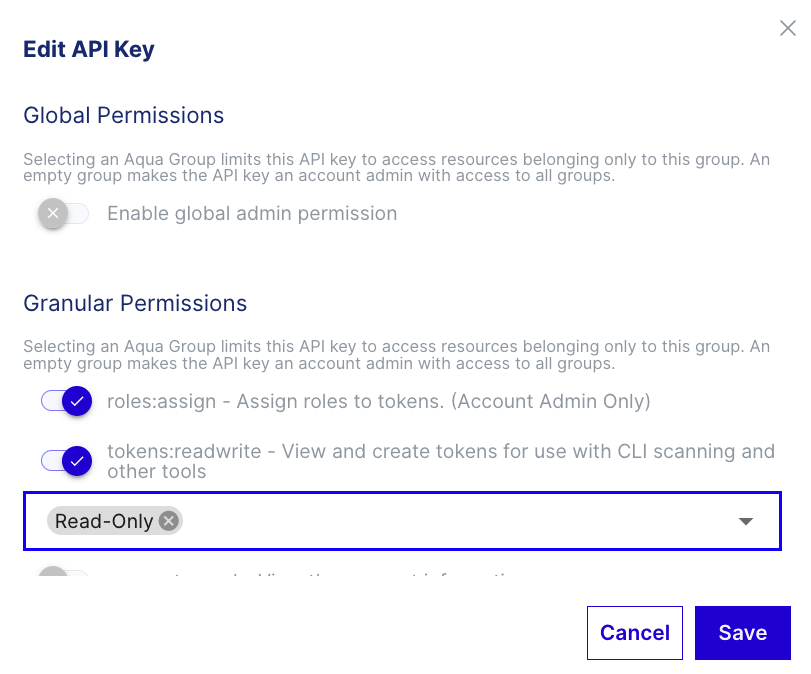
After generating the API key, click the kebab (three vertical dots) next to the new API key, and then click Edit.
-
Disable the Global Permissions toggle and enable the following Granular Permissions, as these are the minimum permissions required to retrieve data from the Aqua API:
-
roles:assign -
tokens:readwrite- Click the dropdown under the
tokens-readwritepermission and select Read-Only.
- Click the dropdown under the
-
-
Click Save.
If you do not have permissions to generate API credentials, contact your Aqua administrator. For additional information, see Aqua Platform documentation on API credentials and API key permissions.
Additional settings
The Aqua SaaS connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 4.
-
Request timeout (secs): The maximum time allotted, in seconds, before a request times out. The default setting is 120 seconds. Although it is not recommended, you can also enter zero (0) to disable timeouts.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the Aqua API before giving up and reporting a failure. The default setting is 5.
Types of data to retrieve
The Aqua SaaS connector can retrieve the following types of data from the Aqua API:
Table 2: Data retrieved from Aqua SaaS
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Container | Yes | Container |
| Container Image | Yes | Container Image |
| Function | No | Not mapped |
| Host | Yes | Host |
| Vulnerability | Yes | Vulnerability |
| Vulnerability Definition | Yes | Vulnerability Definition |
For detailed steps on how to view the data retrieved from Aqua in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Container
Table 3: Container attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| account_id | Local variable |
| agent_exists | Local variable |
| aqua_service | Local variable |
| assurance_results | Local variable |
| cluster_name | Local variable |
| compliant | Local variable |
| container_type | type |
| create_time | firstSeen |
| critical | Local variable |
| high | Local variable |
| have_secrets | Local variable |
| host_enforcer_group | Local variable |
| host_id | targets, Local variable |
| host_lname | Local variable |
| host_name | host |
| id | uid |
| image_assurance_compliant | Local variable |
| image_digest | Local variable |
| image_id | Local variable |
| image_name | image |
| is_disallowed | Local variable |
| is_evaluated | Local variable |
| is_privileged | Local variable |
| is_profiling | Local variable |
| is_registered | Local variable |
| is_root | Local variable |
| ke_exists | Local variable |
| last_vuln_time_seen | Local variable |
| level3 | Local variable |
| low | Local variable |
| malware | Local variable |
| medium | Local variable |
| modify_time | lastSeen |
| mutable | Local variable |
| name | name |
| namespace_name | Local variable |
| network_mode | Local variable |
| origin_image_name | Local variable |
| owner_name | owner |
| permission | Local variable |
| registry_image_name | Local variable |
| risk | riskScore |
| risk_level | Local variable |
| runtime_malware_count | Local variable |
| runtime_profile_name | Local variable |
| scan_status | Local variable |
| secrets | Local variable |
| sensitive | Local variable |
| server_digest | Local variable |
| start_time | firstSeen |
| status | status |
| system_container | Local variable |
| total | Local variable |
| valid_digest | Local variable |
| vulnerabilities | Local variable |
| vulnerability_risk | Local variable |
Container Image
Table 4: Container Image attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| assurance_results | Local variable |
| asset_type | Local variable |
| author | author |
| blacklisted | Local variable |
| cf_org | Local variable |
| cf_space | Local variable |
| created | firstSeen, sourceCreatedDate |
| disallowed | disallowed |
| digest | digest |
| docker_id | Local variable |
| dta_severity_score | Local variable |
| dta_skipped | Local variable |
| dta_skipped_reason | Local variable |
| first_scan_failed | Local variable |
| high_vulns | Local variable |
| image_build_date | Local variable |
| image_uid | Local variable |
| labels | Local variable |
| low_vulns | Local variable |
| malware | Local variable |
| metadata | Local variable |
| microenforcer_detected | Local variable |
| mutable | Local variable |
| name | uid, name |
| neg_vulns | Local variable |
| newer_image_exists | Local variable |
| os | operatingSystem |
| os_version | osVersion |
| parent_layers_id | Local variable |
| partial_results | Local variable |
| pending_disallowed | Local variable |
| permission | Local variable |
| permission_lastupdate | Local variable |
| policy_failures | Local variable |
| registry | registry |
| registry_type | registryType |
| repository | repository |
| scan_date | lastAssessed, lastSeen |
| scan_error | scanError |
| scan_status | scanStatus |
| security_findings | Local variable |
| sensitive_data | Local variable |
| size | Local variable |
| tag | tag |
| type | Local variable |
| vulns_found | Local variable |
| whitelisted | whitelisted |
Host
Table 5: Host attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| account_id | Local variable |
| cloud_info | mapped |
| cluster_id | Local variable |
| created_date | sourceCreatedDate |
| id | uid |
| is_agentless | agentless |
| is_enforced | enforced |
| is_gateway_exists | gatewayExists |
| name | name |
| node_id | uid |
| permission | Local variable |
| security_issues | mapped |
| status | Local variable |
| type | Local variable |
Vulnerability
Table 6: Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| acknowledgeScope | Local variable |
| acknowledgedAuthor | Local variable |
| acknowledgedDate | Local variable |
| ackExpirationConfiguredAt | Local variable |
| ackExpirationConfiguredBy | Local variable |
| ackExpirationDays | Local variable |
| baseImageName | Local variable |
| baseImageVulnerability | Local variable |
| cloudFoundryApplication | Local variable |
| cloudFoundryOrganization | Local variable |
| cloudFoundrySpace | Local variable |
| cluster | Local variable |
| container | Local variable |
| customSeverity | customSeverity |
| deployment | Local variable |
| enforcerGroup | Local variable |
| firstFound | firstFound |
| hasNetworkAttackVector | Local variable |
| heuristicRefId | Local variable |
| imageDigest | targets, imageDigest |
| imageName | targets, imageName |
| imageUid | targets, imageUid |
| lastFound | lastFound |
| layerId | Local variable |
| licenses | Local variable |
| namespace | namespace |
| nvdCvssv2Severity | Local variable |
| nvdCvssv2Vectors | Local variable |
| nvdCvssv3Score | Local variable |
| nvdCvssv3Severity | Local variable |
| nvdCvssv3Vectors | Local variable |
| organizationName | Local variable |
| os | Local variable |
| osVersion | Local variable |
| publishDateSource | Local variable |
| qualysIds | Local variable |
| referencedBy | Local variable |
| registry | Local variable |
| repositoryId | Local variable |
| repositoryName | Local variable |
| resource | results, affected |
| resourceArch | Local variable |
| resourceHash | Local variable |
| resourcePath | Local variable |
| resourceType | Local variable |
| runningWorkloadsCount | runningWorkloadsCount |
| scanId | Local variable |
| severity | sourceSeverity |
| siblingPackage | Local variable |
| solution | recommendation |
| status | providerStatus, sourceStatus, status |
| temporalVector | Local variable |
| vendorCvssv2Score | Local variable |
| vendorCvssv2Severity | Local variable |
| vendorCvssv2Vectors | Local variable |
| vendorCvssv3Score | Local variable |
| vendorCvssv3Severity | Local variable |
| vendorCvssv3Vectors | Local variable |
| vulnerabilityId | Local variable |
| vulnerabilityName | name, type, cveIds, cveRecords |
| vulnerabilityResourceId | Local variable |
| workloads | hasRunningWorkloads |
Vulnerability Definition
Table 7: Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| aquaEvalScore | Local variable |
| aquaScore | Local variable |
| aquaUniqueId | Local variable |
| aquaVectors | Local variable |
| cisaDueDate | cisaDueDate |
| cisaPublishedDate | cisaAddedDate |
| classification | classification |
| cpe | affected |
| description | description |
| epssPercentile | epssPercentile |
| epssScore | epssScore |
| exploitAvailability | exploitability, references |
| exploitType | cisaExploited, exploitability, exploitType |
| fixVersion | fixedVersion |
| format | Local variable |
| hasNetworkAttackVector | Local variable |
| installedVersion | affectedVersion |
| modificationDate | sourceLastModified |
| nvdCvssv2Score | cvssV2BaseScore |
| nvdUrl | references |
| publishDate | publishedDate |
| remoteExploit | remoteExploit |
| resource | results, affected |
| severity | severity, sourceSeverity, severityScore |
| vendorCvssv3Severity | vendorSeverity |
| vendorStatement | vendorStatement |
| vendorUrl | references |
| vulnerabilityName | name, type, cveIds, cveRecords |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the Aqua SaaS connector:
Table 8: Aqua SaaS DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Container | LAST_SEEN NOT IN LAST 7 DAYS | 30 days after inactivity | Uses the LAST_SEEN attribute to identify containers that are inactive within the last 7 days, and then purges the records after 30 days of inactivity. |
| Container Image | LAST_SEEN NOT IN LAST 7 DAYS | 30 days after inactivity | Uses the LAST_SEEN attribute to identify container images that are inactive within the last 7 days, and then purges the records after 30 days of inactivity. |
| Host | LAST_SEEN NOT IN LAST 7 DAYS | 30 days after inactivity | Uses the LAST_SEEN attribute to identify hosts that are inactive within the last 7 days, and then purges the records after 30 days of inactivity. |
| Vulnerability | LAST_CAPTURED NOT IN LAST 7 DAYS | 30 days after inactivity | Uses the LAST_CAPTURED attribute to identify vulnerabilities that are inactive within the last 7 days, and then purges the records after 30 days of inactivity. |
Operation options
The Aqua SaaS connector supports the following operation options. See connector operation options for information about how to apply them.
Container Image
Table 9: Container Image operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Container Image | name | Any container name | Retrieves only containers with the specified name. Key: name Value: kubernetes. This key and value combination only retrieves containers named kubernetes. | |
| repository | Any container repository | Retrieves only containers from the specified repository. | Key: repository Value: angular-spring. This key and value combination only retrieves containers from the angular-spring repository. |
Vulnerability
Table 10: Vulnerability operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Vulnerability | acknowledge_status | true, false | Filter vulnerabilities by whether they are acknowledged (suppressed) in Aqua. | Key: acknowledge_status Value: true. This key and value combination only retrieves acknowledged vulnerabilities. |
| asset_types | functions, hosts, images | A comma-separated list of asset types. Filter vulnerabilities based on the type of asset they affect. | Key: asset_types Value: hosts,images. This key and value combination only retrieves vulnerabilities associated with hosts or images. | |
| exploit_availability | available, not_available | Filter vulnerabilities by whether or not they have an exploit available, as determined by Aqua. | Key: exploit_availability Value: available. This key and value combination only retrieves vulnerabilities that have an exploit available. | |
| exploit_type | dos, local, remote, web apps | A comma-separated list of types of exploits. Filter vulnerabilities by their exploit type. | Key: exploit_type Value: dos,remote. This key and value combination only retrieves vulnerabilities with the dos or remote exploit type. | |
| fix_availability | true, false | Filter vulnerabilities by whether a vendor fix is available, as determined by Aqua. | Key: fix_availability Value: true. This key and value combination only retrieves vulnerabilities with an available fix. | |
| has_workloads | true, false | Filter vulnerabilities based on whether they are associated with running workloads. For additional information, see Aqua documentation. | Key: has_workloads Value: true. This key and value combination only retrieves vulnerabilities that are associated with workloads. | |
| include_vpatch_info | true, false | Retrieves suppressed findings from Aqua. | Key: include_vpatch_info Value: true. This key and value combination retrieves suppressed findings from Aqua. | |
| namespace_names | Any Aqua resource namespace name | A comma-separated list of namespace names. Retrieves only vulnerabilities from the specified namespace names. For additional information, see Aqua documentation. | Key: namespace_names Value: default,kube-system,kube-public. This key and value combination only retrieves vulnerabilities from the specified namespaces. | |
| network_attack | true, false | Filter vulnerabilities by whether they are classified as network-exploitable, as determined by Aqua. | Key: network_attack Value: true. This key and value combination only retrieves vulnerabilities with known network attack vectors. | |
| patch_status | patch_available, patched_audit, patched_enforce, no_patch | A comma-separated list of patch statuses. Filter vulnerabilities by their virtual patch (vShield) status. | Key: patch_status Value: patch_available,patched_enforce. This key and value combination only retrieves vulnerabilities with the patched_enforce or patch_available patch status. | |
| severities | negligible, low, medium, high, critical | A comma-separated list of severity levels. Filter vulnerabilities based on their severity. For additional information, see Aqua documentation. | Key: severities Value: high,critical. This key and value combination only retrieves vulnerabilities with high or critical severity. | |
| show_negligible | true, false | Show or hide vulnerabilities with negligible severity. | Key: show_negligible Value: true. This key and value combination includes vulnerabilities with negligible severity. |
Vulnerability Definition
Table 11: Vulnerability Definition operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Vulnerability Definition | asset_types | images, hosts, functions, code repositories, containers, vms, kubernetes resources | A comma-separated list of asset types. Filter vulnerabilities by their specified asset type. | Key: asset_types Value: hosts,images. This key and value combination only retrieves vulnerabilities associated with hosts or images. |
| exploit_availability | available, not available | Filter vulnerabilities by whether or not that have an exploit available, as determined by Aqua. | Key: exploit_availability Value: available This key and value combination only retrieves vulnerabilities that have an exploit available. | |
| exploit_type | dos, local, remote, web apps | A comma-separated list of types of exploits. Filter vulnerabilities by their exploit type. | Key: exploit_type Value: dos,remote. This key and value combination only retrieves vulnerabilities with the dos or remote exploit type. | |
| include_vpatch_info | 1 | Retrieves suppressed findings from Aqua. | Key: include_vpatch_info Value: 1. This key and value combination retrieves suppressed findings from Aqua. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The Aqua SaaS connector uses the Aqua Enterprise API v2. Specifically, it uses the following endpoints:
Table 12: Aqua SaaS API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Container | GET /api/v2/containers |
| Container Image | GET /api/v2/images/ |
| Function | GET /api/v2/serverless/functions |
| Host | GET /api/v2/infrastructure |
| Vulnerability | POST api/v2/risks/vulnerabilities/exporters/hosts/export |
GET api/v2/risks/vulnerabilities/exporters/hosts/jobs/exportId | |
POST api/v2/risks/vulnerabilities/exporters/hosts/stream | |
| Vulnerability Definition | POST api/v2/risks/vulnerabilities/exporters/hosts/export |
GET api/v2/risks/vulnerabilities/exporters/hosts/jobs/exportId | |
POST api/v2/risks/vulnerabilities/exporters/hosts/stream |
Changelog
The Aqua SaaS connector has undergone the following changes:
Table 13: Aqua SaaS connector changelog
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
| Version | Description | Date Published |
|---|---|---|
| 4.0.4 | Added support for Data lifecycle management to the Container, Container Image, Host, and Vulnerability objects. While this change was introduced in v3.1.3, it has now been fully implemented in the v4.0+ version of the connector. | September 5th, 2025 |
| 4.0.3 | - Added the NAMESPACE attribute to the Vulnerability object. - Added a new operation option to filter vulnerabilities by their namespace: namespace_names | February 21st, 2025 |
| 4.0.2 | Enhanced the connector to retrieve suppressed findings from Aqua. As a result, the following operation option has been added to the Vulnerability object: include_vpatch_info | February 12th, 2025 |
| 4.0.1 | Added the HAS_RUNNING_WORKLOADS and RUNNING_WORKLOADS_COUNT attributes to the Vulnerability object. | December 13th, 2024 |
| 4.0.0 | - Transitioned the Aqua SaaS connector to fully use the Aqua Enterprise API v2 to enhance performance and reliability. - Added two new operation options to filter vulnerabilities: exploit_availability and exploit_type. | December 9th, 2024 |
| 3.1.3 | Added support for Data lifecycle management to the Container, Container Image, Host, and Vulnerability objects. | January 21st, 2025 |
| 3.1.2 | Fixed an issue where the Vulnerability Definition object sync was failing. | November 26th, 2024 |
| 3.1.1 | Code cleanup and general maintenance. | November 7th, 2024 |
| 3.1.0 | Initial Integration+ release. | November 7th, 2024 |