Checkmarx One
Checkmarx One is an application security platform used for scanning, prioritizing, and addressing security vulnerabilities in your organization's applications, projects, or source code. You can bring code, project, and application data from Checkmarx One into Brinqa to manage your application security and construct a unified view of your attack surface, thus strengthening your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Checkmarx One and how to obtain that information from Checkmarx. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Checkmarx One from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Checkmarx One with Brinqa:
-
API URL: The Checkmarx One API URL. The default URL is
https://ast.checkmarx.net/. -
Client ID and Client secret: The client ID and client secret associated with the Checkmarx One account, which must have permissions to log in to the API server and return data.
-
Login URL: The Checkmarx One login URL. The default URL is
https://iam.checkmarx.net/. -
Client Realm: The Checkmarx One Realm client configuration. The client realm represents a specific area within the Checkmarx One platform used for managing users, roles, and permissions.
Generate a Checkmarx One client secret
For the Checkmarx One connector to use the Checkmarx One API, you must provide a client secret. Checkmarx One does not allow retrieving the client secret for an existing user, therefore, you must generate a new client secret instead. To do so, follow these steps:
-
Log in to your Checkmarx One portal.
-
On the left-hand side of the page, click Settings, and then click Identity and Access Management.
-
Click OAuth Clients, and then click Create Client.
-
Provide a Client ID and click Create client.
The page reloads and your new client ID displays.
-
Click Regenerate.
A window appears with your new client secret. You cannot view it again. Copy the client secret and save it in a secure location.
-
Click Ok.
-
Scroll down to Role mapping, locate the
ast-viewerrole, and click Add.This permission allows for viewing the Checkmarx One projects, scans, and results.
-
Click Save Client.
If you do not have the permissions to create a client secret, contact your Checkmarx One administrator. For additional information, see Checkmarx One documentation.
Obtain your Checkmarx One client realm
There are two ways you can obtain your client realm. You can obtain your Checkmarx One client by following these steps:
-
Log in to your Checkmarx One portal.
-
On the left-hand side of the page, click Identity and Access Management.
-
Once you are on the Identity and Access Management page, locate the
{client-realm}value in the URL of the page.The Client Realm is an alphanumeric value, and the URL should resemble the following:
https://iam.checkmarx.net/auth/admin/{client-realm}/console/#/realms/{client-realm}, where{client-realm}represents the actual Client Realm value that you must use in authenticating Checkmarx One with Brinqa.
You can also obtain your Checkmarx One client realm by following these steps:
-
Log in to your Checkmarx One portal.
-
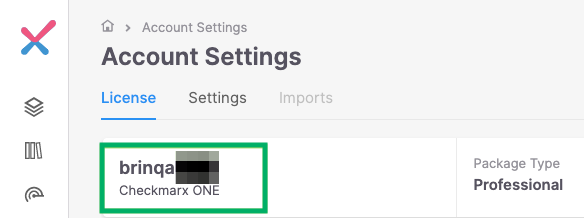
Click Account Settings, represented by a gear icon.
The Client Realm displays under the License tab:
Additional settings
The Checkmarx One connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 2.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the Checkmarx API before giving up and reporting a failure. The default setting is 5.
Types of data to retrieve
The Checkmarx One connector can retrieve the following types of data from the Checkmarx One API:
Table 1: Data retrieved from Checkmarx One
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Application | Yes | Application |
| Assessment | Yes | Assessment |
| Code Project | Yes | Code Project |
| Infrastructure Code As Finding | Yes | Static Code Finding |
| Infrastructure Code Finding Definition | Yes | Static Code Finding Definition |
| Open Source Finding | Yes | Open Source Code Finding |
| Open Source Finding Definition | Yes | Open Source Code Finding Definition |
| Package | Yes | Package |
| Static Code Finding | Yes | Static Code Finding |
| Static Code Finding Definition | Yes | Static Code Finding Definition |
For detailed steps on how to view the data retrieved from Checkmarx One in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Application
Table 2: Application attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | categories |
| createdAt | firstSeen |
| criticality | criticality |
| description | description |
| id | uid |
| name | name |
| tags | tags |
| updatedAt | sourceLastModified |
Assessment
Table 3: Assessment attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| branch | Local variable |
| createdAt | startTime |
| id | uid |
| initiator | Local variable |
| loc | linesOfCode |
| projectId | targets |
| projectName | Local variable |
| sourceOrigin | Local variable |
| sourceType | Local variable |
| status | status |
| tags | tags |
| updated At | endTime |
Code Project
Table 4: Code Project attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| applications | applications |
| createdAt | firstSeen |
| criticality | criticality |
| description | description |
| groups | tags(group:id) |
| id | uid |
| mainBranch | Local variable |
| name | name |
| repoUrl | Local variable |
| tags | tags(key:value) |
| updatedAt | sourceLastModified |
Infrastructure Code As Finding
Table 5: Infrastructure Code As Finding attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ID | uid |
| actualValue | results |
| assessment | firstScanID |
| category | categories |
| comments | Local variable |
| description | description |
| expectedValue | Not mapped |
| fileName | path |
| firstFoundAt | firstFound |
| firstScanID | assessment |
| foundAt | lastFound |
| group | Not mapped |
| issueType | Not mapped |
| line | path |
| platform | Local variable |
| queryID | type, uid |
| queryName | name |
| queryURL | Not mapped |
| searchKey | Not mapped |
| searchValue | Not mapped |
| severity | severity, severityScore |
| similarityID | Local variable |
| state | Local variable |
| status | status, statusCategory, providerStatus, sourceStatus |
| type | categories |
| value | results |
Infrastructure Code Finding Definition
Table 6: Infrastructure Code Finding Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | categories |
| description | description |
| queryID | uid |
| queryName | name |
| severity | severity, severityScore |
Open Source Finding
Table 7: Open Source Finding attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| cveName | Not mapped |
| epssPercentile | EPSS percentile |
| epssValue | EPSS score |
| exploitableMethods | Local variable |
| firstFoundAt | firstFound |
| id | type, uid, cveIds, cveRecords |
| isViolatingPolicy | tags |
| packageId | targets |
| packageId | uid |
| status | status |
| statusCategory | statusCategory |
Open Source Finding Definition
Table 8: Open Source Finding Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| cvss | Not mapped |
| cvssList | Use CVSS calculator |
| cwe | cweIds, weaknesses |
| description | description |
| fixResolutionText | Local variable |
| id | uid, cveIds, cveRecords |
| publishDate | publishedDate |
| recommendations | recommendation |
| references | references |
| referencesData | Not mapped |
| score | Local variable |
| severity | severity, severityScore |
| type | Not mapped |
Package
Table 9: Package attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| highVulnerabilityCount | Local variable |
| id | uid |
| IsDevelopmentDependency | tags (Development) |
| IsDirectDependency | tags (DIRECT_DEPENDENCY) |
| IsNpmVerified | tags (NPM_VERIFIED) |
| IsTestDependency | tags (TEST_DEPENDENCY) |
| IsViolatingPolicy | tags (VIOLATING) |
| Locations | path |
| lowVulnerabilityCount | Local variable |
| matchType | Not mapped |
| Name | name |
| newestVersion | latestVersion |
| NewestVersionReleaseDate | sourceLastModified |
| numberOfVersionsSinceLastUpdate | Local variable |
| outdated | outdated |
| packageRepository | Local variable |
| projectId | projects |
| ReleaseDate | firstSeen |
| riskScore | Local variable |
| scanId | Local variable |
| severity | Local variable |
| version | currentVersion |
Static Code Finding
Table 10: Static Code Finding attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| compliances | Local variable |
| confidenceLevel | Local variable |
| firstFoundAt | firstFound |
| firstScanId | assessment |
| foundAt | lastFound |
| group | tags(group:value) |
| languageName | languages |
| nodes | results |
| path | path |
| pathSystemId | uid |
| queryId | type |
| queryName | name |
| resultHash | uid |
| similarityId | Local variable |
| state | Local variable |
| status | status, statusCategory, providerStatus, sourceStatus |
| uniqueId | Local variable |
Static Code Finding Definition
Table 11: Static Code Finding Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| cause | description, Local variable |
| cweID | cweIds, weaknesses |
| generalRecommendations | recommendation, Local variable |
| queryDescriptionId | name |
| queryId | uid |
| queryName | name |
| resultDescription | description, Local variable |
| risk | description, Local variable |
| samples.code | recommendation |
| samples.progLanguage | recommendation |
| samples.title | recommendation |
| severity | severity, severityScore |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Use CVSS calculator indicates that the CVSS (Common Vulnerability Scoring System) vectors and scores aren't directly mapped to a specific attribute on the UDM. Instead, a specialized library calculates the CVSS scores from the provided CVSS vector strings.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the Checkmarx One connector:
Table 12: Checkmarx One DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Application | LAST_CAPTURED NOT IN LAST 180 Days | 30 days after inactivity | Uses the LAST_CAPTURED attribute to identify applications not scanned in the last 180 days, and then purges the records after 30 days of inactivity. |
| Infrastructure Code Finding | Inactivity is delegated to the Application object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated application, and then purges the records after 30 days of inactivity. |
| Open Source Finding | Inactivity is delegated to the Application object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated application, and then purges the records after 30 days of inactivity. |
| Static Code Finding | Inactivity is delegated to the Application object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated application, and then purges the records after 30 days of inactivity. |
Operation options
The Checkmarx One connector supports the following operation options. See connector operation options for information about how to apply them.
Table 13: Checkmarx One connector operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Infrastructure Code Finding | project-ids | Any Checkmarx One project ID number. | A comma-separated list of project ID numbers. You can use this option to retrieve infrastructure code findings from the specified Checkmarx One projects. | Key: project-ids Value: 1d60e327-8c98-42c5-932f-73a4b91f58e3. This key and value combination only retrieves data from Checkmarx One that pertains to the specified project ID. |
| Infrastructure Code Finding Definition | project-ids | Any Checkmarx One project ID number. | A comma-separated list of project ID numbers. You can use this option to retrieve infrastructure code finding definitions from the specified Checkmarx One projects. | Key: project-ids Value: f9d4bc6a-2e15-4a7c-8b90-1e036cd8e773. This key and value combination only retrieves data from Checkmarx One that pertains to the specified project ID. |
| Open Source Finding | project-ids | Any Checkmarx One project ID number. | A comma-separated list of project ID numbers. You can use this option to retrieve open source findings from the specified Checkmarx One projects. | Key: project-ids Value: 97c2ba45-0186-4d3d-92e3-e3518f760d32. This key and value combination only retrieves data from Checkmarx One that pertains to the specified project ID. |
| Open Source Finding Definition | project-ids | Any Checkmarx One project ID number. | A comma-separated list of project ID numbers. You can use this option to retrieve open source finding definitions from the specified Checkmarx One projects. | Key: project-ids Value: 27e3d460-d410-3f98-85c2-2cb541871a9e. This key and value combination only retrieves data from Checkmarx One that pertains to the specified project ID. |
| Packages | project-ids | Any Checkmarx One project ID number. | A comma-separated list of project ID numbers. You can use this option to retrieve packages from the specified Checkmarx One projects. | Key: project-ids Value: e8c6d4f2-a1b9-4e30-9d6c-75f7c803b520. This key and value combination only retrieves data from Checkmarx One that pertains to the specified project ID. |
| Static Code Finding | project-ids | Any Checkmarx One project ID number. | A comma-separated list of project ID numbers. You can use this option to retrieve static code findings from the specified Checkmarx One projects. | Key: project-ids Value: 45a2bc89-7613-4e0d-92f5-c378d01256ef. This key and value combination only retrieves data from Checkmarx One that pertains to the specified project ID. |
| Static Code Finding Definition | project-ids | Any Checkmarx One project ID number. | A comma-separated list of project ID numbers. You can use this option to retrieve static code finding definitions from the specified Checkmarx One projects. | Key: project-ids Value: 83d4fe29-9601-4c3b-81a7-f215b36279de, 45a2bc97-6810-3d4f-92e3-d760f51832ce. This key and value combination only retrieves data from Checkmarx One that pertains to the specified project IDs. |
To locate your Checkmarx One project IDs, follow these steps:
-
Log in to your Checkmarx One portal.
-
Click the Projects tab to see a list of projects in your account.
-
Locate the ID column next to the corresponding project name. You'll find an icon in the ID column. Click this icon to obtain the project ID.
The project ID is an alphanumeric value and is typically in the following format:
45a2bc89-7613-4e0d-92f5-c378d01256ef.
The option keys and values are case-sensitive as they are shown in this documentation
Stateless behavior
The Checkmarx One connector is a stateless connector. This means that once a finding is fixed or closed in Checkmarx One, it is no longer returned by the Checkmarx One API. As a result, the Brinqa Platform does not receive a status update and cannot automatically reflect that the finding has been resolved. This behavior differs from stateful connectors, which continue to return findings even after their status changes. Since Checkmarx One only reports currently-active findings, you must make some additional configurations in Brinqa to represent the full vulnerability lifecycle.
To ensure that fixed or closed findings from Checkmarx One are accurately represented in the Brinqa Platform, consider the following:
-
Use DLM to manage the data lifecycle of findings by enabling lifecycle policy that marks findings as
inactiveif they are not returned by the connector after a specified period (e.g., 7–14 days). This identifies findings that have likely been fixed or resolved in the source system. -
Create a custom status configuration model that updates the status of findings to
Confirmed fixedorAssumed fixedwhen their state is set toinactive. Normalizing inferred states likeinactiveto standardized values such asConfirmed fixedhelps maintain clarity and consistency across the Brinqa Platform, especially when working with stateless connectors that do not report fixed findings directly.
If you need additional assistance with configuring DLM or creating a new status configuration model, or have questions about stateless connectors, please contact your Brinqa Support team.
APIs
The Checkmarx One connector uses the Checkmarx One REST API. Specifically, it uses the following endpoints:
Table 14: Checkmarx One REST API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Application | GET /api/applications |
| Assessment | GET /api/scans?from-date= |
| Code Project | GET /api/applications |
GET /api/projects | |
| Infrastructure Code Finding | GET /api/kics-results?scan-id= |
| Infrastructure Code Finding Definition | GET /api/kics-results?scan-id= |
| Open Source Finding | GET /api/sca/export/requests |
GET /api/sca/export/requests/{id}/download | |
| Open Source Finding Definition | GET /api/sca/export/requests |
GET /api/sca/export/requests/{id}/download | |
| Package | GET /api/sca/export/requests |
GET /api/sca/export/requests/{id}/download | |
| Static Code Finding | GET /api/sast-results?scan-id= |
| Static Code Finding Definition | GET /api/sast-results?scan-id= |
GET /api/queries/descriptions |
Changelog
The Checkmarx One connector has undergone the following changes:
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
Table 15: Checkmarx One connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.2.5 | - Replaced the deprecated /api/sca/risk-management/reporting/packages API endpoint with the /api/sca/export/requests endpoint. - Updated the attribute mappings for the Package object. - Improved performance and resource management. | January 30th, 2026 |
| 3.2.4 | - Added a new "Maximum retries" setting in Additional settings. - Code cleanup and maintenance. | October 30th, 2025 |
| 3.2.3 | No change. | September 18th, 2025 |
| 3.2.2 | Fixed an issue where the connector was not populating exploitability information for CVEs on the Open Source Finding Definition object. This was due to the EXPLOITABLE_METHODS attribute being assigned to the wrong object. As a result, the EXPLOITABLE_METHODS attribute has been moved to the Open Source Finding object. | August 27th, 2025 |
| 3.2.1 | Fixed an issue where the Open Source Finding object sync was failing. | July 18th, 2025 |
| 3.2.0 | - The api/sca/risk-management/risk-reports API endpoint is being deprecated by Checkmarx. As a result, it has been replaced with the api/sca/export/requests API endpoint. - Fixed an issue where the connector was not retrieving all findings from Checkmarx. As a result, Pagination has now been introduced on the api/projects/last-scan API endpoint to ensure all findings are retrieved. - Fixed an issue where Static Code Findings were incorrectly linked to the first scan instead of the last scan. The connector now correctly associates Static Code Findings with the last scan for more accurate assessment tracking. | March 12th, 2025 |
| 3.1.3 | Fixed an issue where the connector was not properly ingesting exploitability information. As a result, the EXPLOITABLE_METHODS attribute type on the Open Source Finding Definition object has been changed from string to multi-value. | February 25th, 2025 |
| 3.1.2 | - Fixed an issue where objects using the /api/risk-management/risk-reports/ endpoint were taking longer than expected to sync. - Improved performance by preventing unnecessary retries on 404 errors. - Fixed an issue where the connector was not properly identifying the correct scan type when retrieving the last scan for different object types. | February 12th, 2025 |
| 3.1.1 | - Added support for Data lifecycle management to the Application, Infrastructure Code Finding, Open Source Finding, and Static Code Finding objects. - Added the LAST_CAPTURED attribute to the Application object. - Added the PROVIDER_STATUS and SOURCE_STATUS attributes to the Infrastructure Code Finding, Open Source Finding, and Static Code Finding objects. - Added the LAST_CAPTURED attribute to the Static Code Finding object. | January 28th, 2025 |
| 3.1.0 | Code cleanup and general maintenance. | January 7th, 2025 |
| 3.0.8 | No change. | October 1st, 2024 |
| 3.0.7 | No change. | August 16th, 2024 |
| 3.0.6 | No change. | August 6th, 2024 |
| 3.0.5 | Changed the CRITICALITY attribute type on the Application object from string to integer. | July 8th, 2024 |
| 3.0.4 | No change. | June 6th, 2024 |
| 3.0.3 | No change. | March 3rd, 2024 |
| 3.0.2 | Restructured the code to align with the latest Connector Framework. | February 11th, 2024 |
| 3.0.1 | Enhanced the Static Code Finding object to return UNKNOWN when file name is missing in the source. | December 6th, 2023 |
| 3.0.0 | Initial Integration+ release. | April 14th, 2023 |