Contrast Security
Contrast Security is an application security tool. You can bring application, library, server, and security check data from Contrast Security into Brinqa to gain a unified view of your attack surface and strengthen your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Contrast Security and how to obtain that information from Contrast Security. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Contrast Security from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Contrast Security with Brinqa:
-
Server URL: The Contrast Security server URL. The default URL is
https://app.contrastsecurity.com. -
Username: The username associated with the Contrast Security account, which must have permissions to log in to the API server and return data.
-
Service key and API key: The access keys associated with the Contrast Security account, which must have permissions to log in to the API server and return data.
Obtain Contrast Security API keys
For the Contrast Security connector to use the Contrast Security API, you must generate a service key and API key. To do so, follow these steps:
-
Log in to your organization's Contrast Security portal as an administrator.
-
Navigate to your user profile and click User Settings.
-
The API Key and Service Key are displayed in the Your Keys > Your API Keys section on the page.
Although you can return to this page to view the access keys, you should handle them with care by ensuring that they are stored in a secure location.
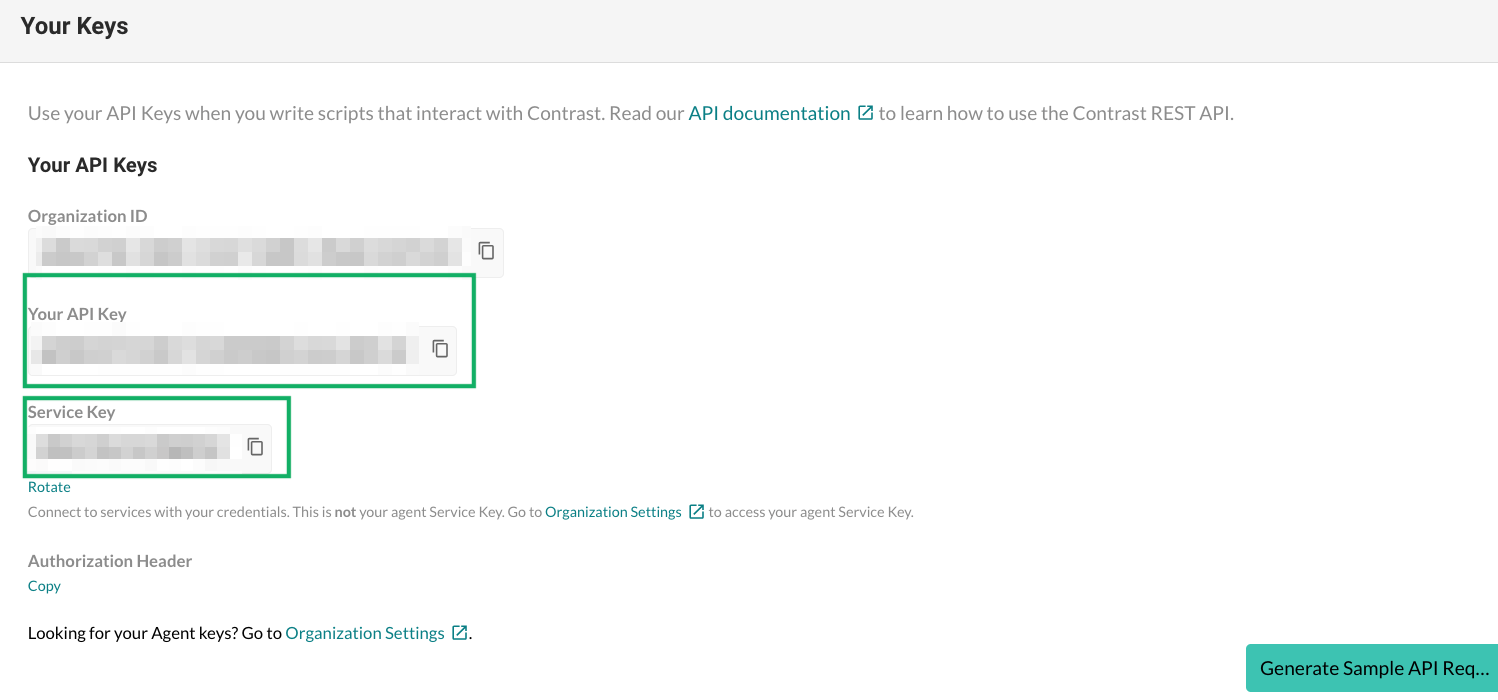
-
If you are unsure of the API URL needed for authentication, click Generate Sample API Request.
The API request includes the correct API URL.
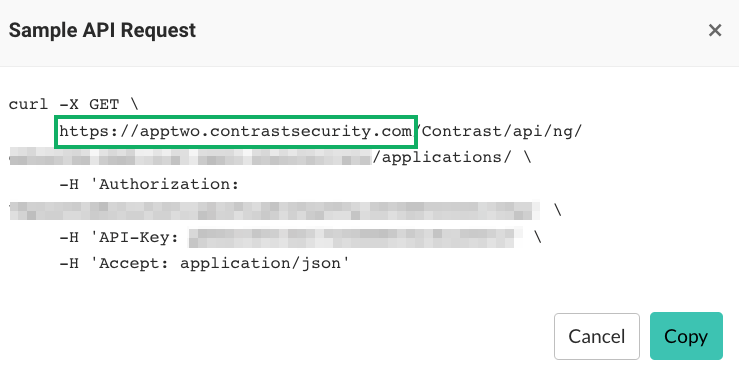
If you do not have permissions to create API keys, contact your Contrast Security administrator. For additional information, see Contrast Security documentation.
Additional settings
The Contrast Security connector contains additional options for specific configuration:
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the Contrast Security API before giving up and reporting a failureThe default setting is 5.
-
Parallel requests: The maximum number of parallel API requests. The default setting is 4.
-
Include vulnerability analysis, consequence, and solution: Specifies whether to retrieve additional vulnerability details. When enabled, the connector retrieves the following attributes for vulnerabilities and vulnerability definitions:
- ANALYSIS
- CONSEQUENCE
- RECOMMENDATION
- REFERENCES
- WEAKNESSES
The connector makes two additional API calls when this setting is enabled:
-
/ng/{orgUuid}/traces/{traceUuid}/story(retrieves ANALYSIS and CONSEQUENCE) -
/ng/{orgUuid}/traces/{traceUuid}/recommendation(retrieves RECOMMENDATION, REFERENCES, and WEAKNESSES)
cautionEnabling this setting increases the number of API requests, which may impact performance.
Types of data to retrieve
The Contrast Security connector can retrieve the following types of data from the Contrast Security API:
Table 1: Data retrieved from Contrast Security
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Application | Yes | Application |
| Library | Yes | Package |
| Server | Yes | Host |
| Vulnerability | Yes | Vulnerability |
| Vulnerability Definition | Yes | Vulnerability Definition |
For detailed steps on how to view the data retrieved from Contrast Security in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes:
Application
Table 2: Application attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| app_id | uid |
| archived | Local variable |
| assess | Local variable |
| assessPending | Local variable |
| categories | categories |
| code | Local variable |
| code_shorthand | Local variable |
| created | firstSeen |
| defend | Local variable |
| defendPending | Local variable |
| importance | Local variable |
| importance_description | Local variable |
| last_seen | lastSeen |
| language | language |
| license.level | Local variable |
| master | Local variable |
| name | name |
| notes | Local variable |
| parentApplicationId | Local variable |
| path | path |
| platform.grade | Local variable |
| platform.letter_grade | Local variable |
| roles | Local variable |
| scores.grade | Local variable |
| scores.letter_grade | Local variable |
| security.grade | Local variable |
| security.letter_grade | Local variable |
| servers_without_defend | Local variable |
| short_name | Local variable |
| size | Local variable |
| size_shorthand | Local variable |
| status | status, sourceStatus |
| tags | tags |
| techs | Local variable |
| total_modules | Local variable |
Library
Table 3: Library
| Source Field Name | Maps to Attribute |
|---|---|
| agePenalty | Local variable |
| app_language | language |
| apps | Local variable |
| categories | categories |
| classes_used | Local variable |
| class_count | Local variable |
| custom | Local variable |
| file_name | name |
| file_version | Local variable |
| grade | Local variable |
| group | Local variable |
| hash | uid |
| invalid_version | Local variable |
| latest_release_date | Local variable |
| latest_version | Local variable |
| loc | Local variable |
| loc_shorthand | Local variable |
| months_outdated | Local variable |
| ossEnabled | Local variable |
| release_date | Local variable |
| restricted | Local variable |
| score | Local variable |
| servers | Local variable |
| source_status | sourceStatus |
| status | status |
| tags | tags |
| total_vulnerabilities | Local variable |
| version | currentVersion |
| versionPenalty | Local variable |
| versions_behind | Local variable |
Server
Table 4: Server attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| Categories | categories |
| agent_version | Local variable |
| applications | Local variable |
| assess | Local variable |
| assessPending | Local variable |
| assess_last_update | Local variable |
| assess_sensors | Local variable |
| container | Local variable |
| defend | Local variable |
| defendPending | Local variable |
| defend_sensors | Local variable |
| defense_last_update | Local variable |
| environment | Local variable |
| hostname | hostnames |
| language | Local variable |
| last_activity | Local variable |
| last_startup | Local variable |
| latest_agent_version | Local variable |
| name | name |
| num_apps | Local variable |
| out_of_date | Local variable |
| path | path |
| server id | uid |
| status | status, sourceStatus |
| syslog_enabled | Local variable |
| syslog_ip_address | ipAddresses, publicIpAddresses, privateIpAddresses |
| tags | tags |
| type | Local variable |
Vulnerability
Table 5: Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| application | targets |
| closed_time | lastFixed |
| confidence | Local variable |
| discovered | Local variable |
| evidence | results |
| first_time_seen | firstFound |
| hasParentApp | Local variable |
| last_time_seen | lastFound |
| last_vuln_time_seen | Local variable |
| likelihood | Local variable |
| organization_name | Local variable |
| request | Local variable |
| status | status, sourceStatus, statusCategory |
| story.risk | Local variable |
| story.text | Local variable |
| sub_status | Local variable |
| tags | tags |
| total_traces_received | Local variable |
| uuid | uid, type |
| visible | Local variable |
Vulnerability Definition
Table 6: Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | categories |
| language | language |
| recommendation | recommendation |
| recommendation.cwe | weaknesses, references |
| rule_name | Local variable |
| rule_title | Local variable |
| severity | severity, sourceSeverity, severityScore |
| title | name |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Operation options
The Contrast Security connector supports the following operation options. See connector operation options for information about how to apply them.
Table 7: Contrast Security connector operation options
The Contrast Security connector supports the following operation options:
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Application | maxRetries | Any numeric value | Specifies the maximum number of times the integration attempts to retrieve application data before failing. | Key: maxRetries Value: 5. This key and value combination limits retry attempts to 5 for applications. |
| Library | maxRetries | Any numeric value | Specifies the maximum number of times the integration attempts to retrieve library data before failing. | Key: maxRetries Value: 5. This key and value combination limits retry attempts to 5 for libraries. |
| Server | maxRetries | Any numeric value | Specifies the maximum number of times the integration attempts to retrieve server data before failing. | Key: maxRetries Value: 5. This key and value combination limits retry attempts to 5 for servers. |
| Vulnerability, Vulnerability Definition | maxRetries | Any numeric value | Specifies the maximum number of times the integration attempts to retrieve vulnerability data before failing. | Key: maxRetries Value: 5. This key and value combination limits retry attempts to 5 for vulnerabilities. |
| severities | LOW, MEDIUM, HIGH, CRITICAL | A comma-separated list of severity levels. Filters vulnerabilities by their severity level, as determined by Contrast Security. | Key: severities Value: HIGH,CRITICAL. This key and value combination retrieves only high and critical vulnerabilities. | |
| status | Confirmed, Fixed, NotAProblem, Remediated, Suspicious | A comma-separated list of vulnerability status categories. Filters vulnerabilities by their status category, as determined by Contrast Security. For more information on vulnerability status categories, see Contrast Security documentation. | Key: status Value: Confirmed,Suspicious. This key and value combination retrieves only vulnerabilities with a status of confirmed or suspicious. | |
| tracked | true, false | Filters vulnerabilities based on whether they are being tracked by a bug tracker tool, as specified by Contrast Security. For more information, see Contrast Security documentation. | Key: tracked Value: true. This key and value combination retrieves only vulnerabilities that are currently tracked in a bug tracker. | |
| untracked | true, false | Filters vulnerabilities based on whether they are not being tracked by a bug tracker tool, as specified by Contrast Security. For more information, see Contrast Security documentation. | Key: untracked Value: false. This key and value combination retrieves only vulnerabilities that are not tracked in a bug tracker. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The Contrast Security connector uses the Contrast Security API. Specifically, it uses the following endpoint:
Table 8: Contrast Security API Endpoint
| Connector Object | API Endpoint |
|---|---|
| Application | GET /Contrast/api/ng/{organization_uuid}/applications |
| Library | GET /Contrast/api/ng/{organization_uuid}/libraries |
| Server | GET /Contrast/api/ng/{organization_uuid}/servers |
| Vulnerability | GET /Contrast/api/ng/{organization_uuid}/orgtraces/filter |
GET /Contrast/api/ng/{organization_uuid}/traces/{trace_uuid}/recommendation | |
GET /Contrast/api/ng/{organization_uuid}/traces/{trace_uuid}/story | |
| Vulnerability Definition | GET /Contrast/api/ng/{organization_uuid}/orgtraces/filter |
GET /Contrast/api/ng/{organization_uuid}/traces/{trace_uuid}/recommendation | |
GET /Contrast/api/ng/{organization_uuid}/traces/{trace_uuid}/story |
Changelog
The Contrast Security connector has undergone the following changes:
Table 9: Contrast Security connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.0.1 | Fixed an issue where syncs were failing due to an unexpected character error. | April 16th, 2025 |
| 3.0.0 | Initial Integration+ release. | February 12th, 2025 |