Trend Micro Cloud Conformity
Trend Micro Cloud Conformity is a cloud security tool that scans your cloud assets for policy violations. You can bring access control roles, accounts, checks, events, groups, reports, services, and users from Trend Micro into the Brinqa Platform to construct a unified view of your attack, thus strengthening your cybersecurity posture.
This document details the information you must provide for the connector to authenticate with Trend Micro Cloud Conformity and how to obtain that information from Trend Micro. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Trend Micro Cloud Conformity from the Connector dropdown. You must provide the following information to authenticate Trend Micro Cloud Conformity with Brinqa:
-
Server URL: Your organization's Trend Micro Cloud Conformity Server URL. The default URL format is
https://<ServerName>/. -
API key: The API token associated with the Trend Micro Cloud Conformity account, which must have permissions to log in to the API server and return data.
Generate a Trend Micro Cloud Conformity API key
For the Trend Micro Cloud Conformity connector to retrieve data from the Cloud Conformity API, you must provide an API key. To obtain an API key, follow these steps:
-
Log in to your organization's Trend Micro Cloud One portal.
-
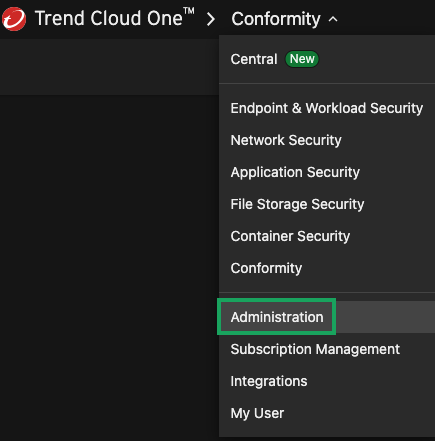
Click the dropdown at the top of the page and select Administration.
-
Navigate to API Keys, and then click New.
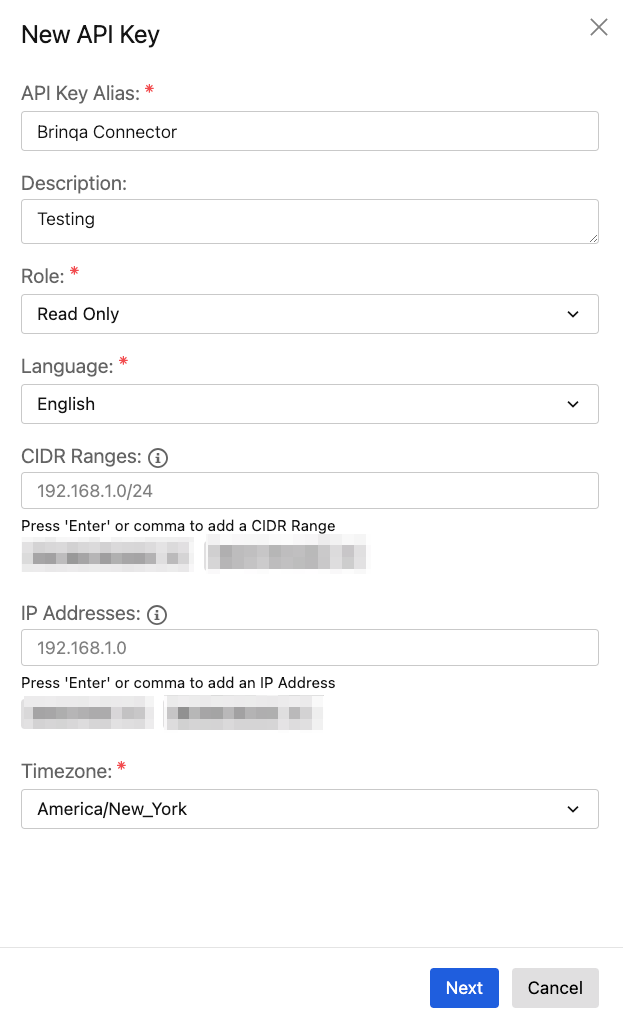
The "New API Key" dialog appears. Complete the following:
-
API Key Alias: Provide an alias, or title, for the API key.
-
Description: (Optional) Provide a description for the API key.
-
Role: Click the dropdown and select Read Only, as this is considered to be the minimum role needed to read and retrieve data from the Cloud Conformity API. For additional information, see Trend Micro Cloud One documentation.
-
Language: Click the dropdown and select language for the API key.
-
CIDR Ranges and IP Addresses: (Optional) Specify the CIDR range(s) and/or specific IP address(es) from which API requests are allowed. You can add multiple ranges or addresses by pressing "Enter" on your keyboard or separating them with commas. Both IPv4 and IPv6 addresses are supported.
You can leave these fields blank to allow any CIDR range or IP address to access the API. Please contact your Brinqa Support team so that they can assist you with the list of CIDR ranges or IP addresses for whitelisting.
-
Timezone: Click the dropdown and specify the timezone for the API key.
-
-
Click Next.
Your API key displays. You cannot view the key again after this. Copy and save it to a secure location.
If you do not have permissions to create an API key, contact your Trend Micro Cloud Conformity administrator. For additional information, see Trend Micro Cloud One documentation.
Additional settings
The Trend Micro Cloud Conformity connector contains additional options for specific configuration:
-
Parallel requests: The maximum number of parallel API requests. The default setting is 4.
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
Types of data to retrieve
The Trend Micro Cloud Conformity connector can retrieve the following types of data from the Cloud Conformity API:
Table 1: Data retrieved from Trend Micro Cloud Conformity
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Access Controls Role | No | Not mapped |
| Account | Yes | Cloud Resource |
| Check | Yes | Cloud Resource, Violation, Violation Definition |
| Event | No | Incident |
| Group | No | Team |
| Report | No | Not mapped |
| Service | No | Not mapped |
| User | Yes | Person |
The Trend Micro Cloud Conformity connector does not currently support operation options for the types of data it retrieves.
For detailed steps on how to view the data retrieved from Trend Micro Cloud Conformity in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Account
Table 2: Account attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| access | Local variable |
| accessLevel | Local variable |
| authFailureCount | Local variable |
| awsaccount-id | cloudAccountId |
| bot-status | Local variable |
| cloud-id | Local variable |
| cloud-type | cloudProvider |
| consumption-tier | Local variable |
| created-date | sourceCreatedDate |
| disabled | Local variable |
| disabledUntil | Local variable |
| environment | Local variable |
| firstAuthErrorDate | Local variable |
| id | uid |
| is-deprecated-rules-free | Local variable |
| last-checked-date | sourceLastModified |
| last-monitoring-event-date | Local variable |
| name | name |
| resources-count | Local variable |
| security-package | Local variable |
| status | status, statusCategory, sourceStatus |
| tags | tags |
| type | type |
Check
Table 3: Check attribute mappings
| Source Field Name | Maps To UDM | Maps to Attribute |
|---|---|---|
| categories | Not mapped | categories |
| ccrn | Cloud Resource | uid, Local variable |
| cloudAccountId | Cloud Resource | local variable, cloudAccountId |
| compliances | Not mapped | local variable |
| cost | Not mapped | local variable |
| created-date | Violation | sourceCreatedDate |
| descriptorType | Not mapped | local variable |
| excluded | Not mapped | local variable |
| extradata.label | Not mapped | local variable |
| extradata.name | Not mapped | local variable |
| extradata.type | Not mapped | local variable |
| extradata.value | Not mapped | local variable |
| failure-discovery-date | Not mapped | local variable |
| failureCount | Not mapped | Local variable |
| id | Violation | uid |
| last-modified-date | Violation | sourceLastModified |
| last-refresh-date | Not mapped | local variable |
| link | Cloud Resource | url, local variable |
| link-title | Not mapped | local variable |
| message | Not mapped | local variable |
| pretty-risk-level | Not mapped | local variable |
| provider | Cloud Resource | cloud provider, local variable |
| region | Violation, CloudResource | region |
| relationships.account.data.id | Violation | targets |
| relationships.account.data.type | Not mapped | local variable |
| relationships.rule.data.id | Not mapped | type |
| relationships.rule.data.type | Not mapped | local variable |
| resolution-page-url | Not mapped | local variable |
| resource | Not mapped | local variable |
| resourceName | Not mapped | local variable |
| risk-level | Not mapped | local variable |
| rule-title | Not mapped | local variable |
| rules.accountIds | Not mapped | Local variable |
| rules.categories | Violation Definition | categories |
| rules.provider | Not mapped | local variable |
| rules.riskLevels | Violation Definition | severity, sourceSeverity, severityCategory |
| rules.ruleId | Violation Definition | uid |
| rules.ruleTitle | Violation Definition | name |
| rules.services | Not mapped | local variable |
| service | Violation | targets |
| status | Violation | status, statusCategory, sourceStatus |
| status_reason | Not mapped | local variable |
| suppressedCount | Not mapped | Local variable |
| suppressedFailureCount | Not mapped | Local variable |
| suppressedSuccessCount | Not mapped | Local variable |
| tags | Violation | tags |
| type | Not mapped | local variable |
| waste | Not mapped | local variable |
Event
Table 4: Event attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| description | description |
| id | uid |
| name | name |
| relationships.account.data.id | Local variable |
| relationships.account.data.type | Local variable |
| relationships.organization.data.id | Local variable |
| relationships.organization.data.type | Local variable |
| relationships.user.data.id | Local variable |
| relationships.user.data.type | Local variable |
| time | sourceCreatedDate |
| type | type |
Group
Table 5: Group attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| accounts.data.id | Local variable |
| accounts.data.type | Local variable |
| created-date | sourceCreatedDate |
| id | uid |
| last-modified-date | sourceLastModified |
| name | name |
| relationships.organization.data.id | Local variable |
| relationships.organization.data.type | Local variable |
| tags | tags |
| type | type |
User
Table 6: User attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| created-date | sourceCreatedDate |
| email-organization-id | Local variable |
| first-name | firstName |
| has-credentials | Local variable |
| id | uid |
| is-cloud-one-ssov2-user | Local variable |
| is-cloud-one-user | Local variable |
| last-login-date | lastSeen |
| last-name | lastName |
| role | Local variable |
| status | status |
| summary-email-opt-out | Local variable |
| type | type |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
APIs
The Trend Micro Cloud Conformity connector uses the Cloud Conformity API. Specifically, it uses the following endpoints:
Table 7: Trend Micro Cloud Conformity API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Access Controls Role | GET /access-control/roles |
| Account | GET /accounts |
| Check | GET /checks |
| Event | GET /events |
| Group | GET /groups |
| Report | GET /reports |
| Service | GET /services |
| User | GET /users |
Changelog
The Trend Micro Cloud Conformity connector has undergone the following changes:
Table 8: Trend Micro Cloud Conformity connector changelog
| Version | Description | Date Published |
|---|---|---|
| 3.0.1.2 | Initial Integration+ release. | November 14th, 2024 |