Google Security Command Center
Google's Security Command Center service provides visibility and insights into your Google Cloud environment. You can bring bucket, compute instance, firewall, and security data from Google Cloud into Brinqa to construct a unified view of your attack surface and enhance your ability to mitigate potential risks.
This document details the information you must provide for the connector to authenticate with Google Cloud and how to obtain that information from Google Cloud. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select Google Security Command Center from the Connector dropdown. If you cannot find the connector in the dropdown, make sure that you have installed it first. You must provide the following information to authenticate Google Cloud with Brinqa:
-
Scope: The relative name of the root asset in your Google Cloud environment. Only the following formats are supported:
-
An organization number, e.g.: "organizations/123".
-
A project ID, e.g.: "projects/my-project-id".
-
A project number, e.g.: "projects/12345".
noteProviding an organization number enables collecting assets from all associated projects, including any new projects added after you have set up the integration. But the credentials you provide must have organization level permissions. Follow the rest of this document for instructions.
-
-
Credentials: The full content of the JSON file that contains your service account key.
Enable the Cloud Asset API
The Google Security Command Center connector requires that you enable the Cloud Asset API on the specified scope.
Create a custom role for Brinqa
Google Cloud uses service accounts to authenticate and authorize API calls, but you can only create service accounts within a project. For the Google Security Command Center connector to collect assets from multiple projects, you must grant the service account organization level permissions through a custom Identity and Access Management (IAM) role.
To create a custom role with organization level permissions, follow these steps:
-
Log in to the Google Cloud Console.
-
Select the organization where you want the connector to collect assets.
-
In the Navigation menu, select IAM & Admin > Roles.
-
Click Create Role.
-
Enter a name and description for your role.
-
Click Add Permissions and add the following read-only permissions required by the connector:
-
cloudasset.viewer -
securitycenter.findingsViewer
-
-
Click Create.
Create a service account and grant organization level permissions
Since the service account must have organization level permissions for the Google Security Command Center connector to collect assets from all the projects within the organization, Brinqa recommends that you create a service account specifically for the connector.
To create a service account and grant the appropriate permissions, follow these steps:
-
Log in to the Google Cloud Console.
-
Select the project where you want to create the service account.
-
In the Navigation menu, select IAM & Admin > Service Accounts.
-
Click Create Service Account.
-
Enter a name and description for the service account.
-
Skip the optional steps and click Done.
-
View the service account details and save the email address for later use.
-
Select the organization where you have created the custom role.
-
In the Navigation menu, select IAM & Admin.
-
Click Grant Access.
-
Click New principals and paste in the email taken from the service account details page.
-
Click Select a role and select the custom role created previously.
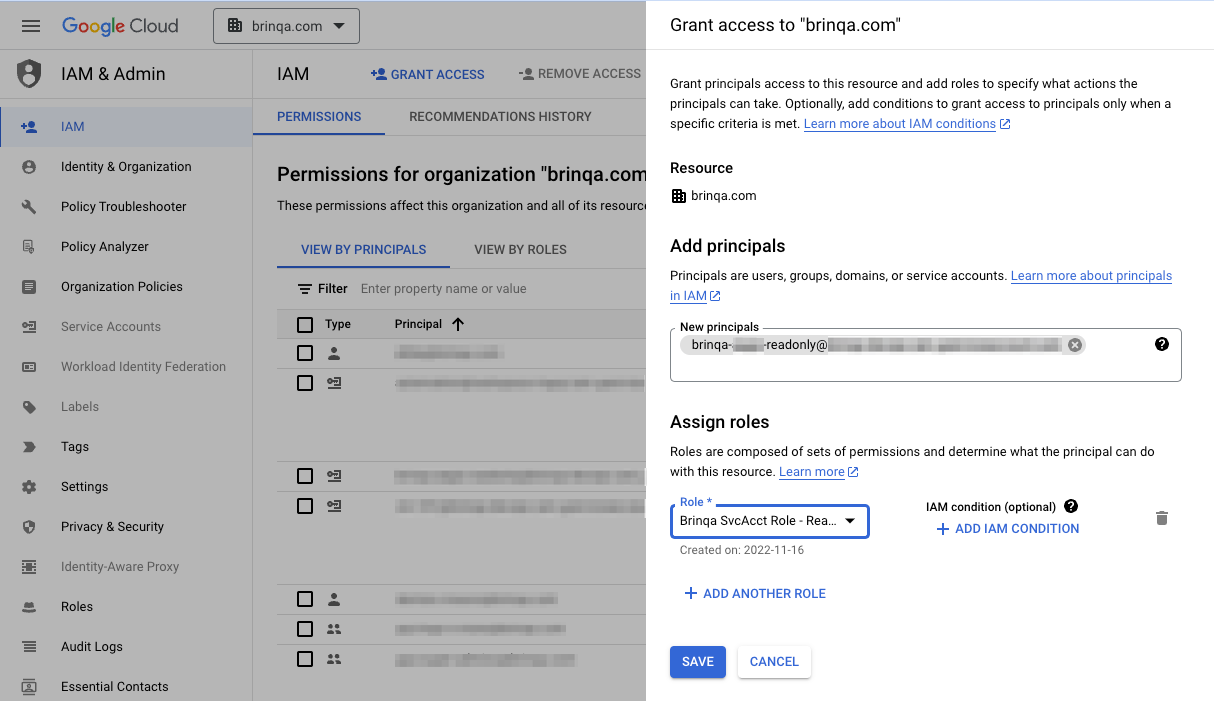
-
Click Save.
Obtain your service account key
If you have completed the previous steps successfully, your service account should have the minimum permissions that the Google Security Command Center connector needs to collect assets from all the projects within your organization.
To obtain the service account key, follow these steps:
-
Log in to the Google Cloud Console.
-
Select your project where the service account resides.
-
In the Navigation menu, select IAM & Admin > Service Accounts.
-
Select the service account and click the Keys tab.
-
Click Add Key > Create new key.
-
Keep JSON as key type and click Create.
The generated private key file is saved to your computer automatically.
Additional settings
The Google Security Command Center connector contains an additional option for specific configuration:
- Page size: The maximum number of records to get per API request. The default setting is 1000. It is not recommended to go over 1000.
Types of data to retrieve
The Google Security Command Center connector can retrieve the following types of data from Google Cloud:
Table 1: Data retrieved from Google Cloud
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Google Security Center Alert | Yes | Alert |
| Google Security Center Alert Definition | Yes | Alert Definition |
| Google Security Center Bucket | Yes | Cloud Resource |
| Google Security Center Compute Instance | Yes | Host |
| Google Security Center Firewall | Yes | Cloud Resource |
| Google Security Center GKE Cluster | Yes | Cloud Resource |
| Google Security Center Project | Yes | Cloud Resource |
| Google Security Center Repository | Yes | Cloud Resource |
| Google Security Center Service Account | Yes | Cloud Resource |
| Google Security Center SQL Instance | Yes | Host |
| Google Security Center Violation | Yes | Violation |
| Google Security Center Violation Definition | Yes | Violation Definition |
| Google Security Center Vulnerability | Yes | Vulnerability |
| Google Security Center Vulnerability Definition | Yes | Vulnerability Definition |
For detailed steps on how to view the data retrieved from Google Cloud in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Google Security Center Alert
Table 2: Google Security Center Alert attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | type |
| createTime | sourceCreatedDate |
| eventTime | Local variable |
| getResourceName | targets, Local variable |
| name | uid |
| SourceProperties.ActivationTrigger | Local variable |
| SourceProperties.ProjectId | projects |
| SourceProperties.ResourcePath | path |
| State | status, sourceStatus, statusCategory |
Google Security Center Alert Definition
Table 3: Google Security Center Alert Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | uid, name |
| findingClass | Local variable |
| severity | severity, sourceSeverity, severityScore |
| SourceProperties.ExceptionInstructions | Local variable |
| SourceProperties.Explanation | description |
| SourceProperties.Recommendation | recommendation |
| SourceProperties.ScannerName | Local variable |
Google Security Center Bucket
Table 4: Google Security Center Bucket attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| acl | Local variable |
| ancestors | Local variable |
| assetType | categories |
| billing.requesterPays | Local variable |
| defaultObjectAcl | Local variable |
| encryption.defaultKmsKeyName | Local variable |
| etag | tags, Local variable |
| iamConfiguration.publicAccessPrevention | Local variable |
| iamConfiguration.uniformBucketLevelAccess | Local variable |
| kind | categories |
| labels | tags, Local variable |
| lifecycle.rule.condition.isLive | status |
| location | location |
| locationType | Local variable |
| logging.logBucket | Local variable |
| id / name | uid |
| name | name |
| owner | Local variable |
| retentionPolicy | Local variable |
| selfLink | url |
| storageClass | Local variable |
| timeCreated | firstSeen |
| updateTime | sourceLastModified |
| version | currentVersion |
| website | Local variable |
Google Security Center Compute Instance
Table 5: Google Security Center Compute Instance attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ancestors | Local variable |
| assetType | categories |
| canIpForward | Local variable |
| confidentialInstanceConfig.enableConfidentialCompute | Local variable |
| cpuPlatform | Local variable |
| creationTimestamp | firstSeen |
| deletionProtection | Local variable |
| description | description |
| disks | Local variable |
| displayDevice.enableDisplay | Local variable |
| fingerprint | Local variable |
| id | Local variable |
| id / name | uid |
| kind | categories |
| labels | tags |
| lastStartTimestamp | lastStarted |
| lastStopTimestamp | lastStopped |
| machineType | Local variable |
| name | name, Local variable |
| networkInterfaces.accessConfigs.natIP | ipAddresses, publicIpAddresses |
| networkInterfaces.accessConfigs.networkTier | Local variable |
| networkInterfaces.network | Local variable |
| networkInterfaces.networkIP | ipAddresses, privateIpAddresses |
| networkInterfaces.stackType | Local variable |
| networkInterfaces.subnetwork | Local variable |
| reservationAffinity.consumeReservationType | Local variable |
| scheduling.automaticRestart | Local variable |
| scheduling.onHostMaintenance | Local variable |
| scheduling.preemptible | Local variable |
| scheduling.provisioningModel | Local variable |
| selfLink | url |
| serviceAccounts.email | emails |
| shieldedInstanceConfig.enableIntegrityMonitoring | Local variable |
| shieldedInstanceConfig.enableSecureBoot | Local variable |
| shieldedInstanceConfig.enableVtpm | Local variable |
| startRestricted | Local variable |
| status | status, sourceStatus |
| tags | tags, Local variable |
| updateTime | sourceLastModified |
| version | currentVersion |
| zone | Local variable |
Google Security Center Firewall
Table 6: Google Security Center Firewall attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ancestors | Local variable |
| assetType | categories |
| creationTimestamp | firstSeen |
| description | description |
| direction | Local variable |
| disabled | Local variable |
| id / name | uid |
| kind | categories |
| logConfig.enable | Local variable |
| name | name, Local variable |
| network | Local variable |
| priority | Local variable |
| selfLink | url |
| sourceRanges | Local variable |
| targetTags | tags |
| updateTime | sourceLastModified |
| version | currentVersion |
Google Security Center GKE Cluster
Table 7:Google Security Center GKE Cluster attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ancestors | Local variable |
| assetType | categories |
| clusterIpv4Cidr | Local variable |
| createTime | firstSeen |
| currentMasterVersion | Local variable |
| currentNodeCount | Local variable |
| currentNodeVersion | Local variable |
| description | description |
| enableKubernetesAlpha | Local variable |
| enableTpu | Local variable |
| endpoint | Local variable |
| etag | tags |
| expireTime | Local variable |
| id / name | uid |
| initialClusterVersion | Local variable |
| initialNodeCount | Local variable |
| instanceGroupUrls | Local variable |
| labelFingerprint | Local variable |
| location | Local variable |
| loggingService | Local variable |
| monitoringService | Local variable |
| name | name |
| network | Local variable |
| nodeIpv4CidrSize | Local variable |
| satisfiesPzi | Local variable |
| satisfiesPzs | Local variable |
| selflink | url |
| servicesIpv4Cidr | Local variable |
| status | sourceStatus, status |
| statusMessage | Local variable |
| subnetwork | Local variable |
| tpuIpv4CidrBlock | Local variable |
| update_time | sourceLastModified |
| version | Local variable |
| zone | Local variable |
Google Security Center Project
Table 8: Google Security Center Project attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ancestors | Local variable |
| assetType | categories |
| createTime | firstSeen |
| data.name | Local variable |
| labels | tags |
| lifecycleState | status |
| parent.id | Local variable |
| parent.type | Local variable |
| projectId | Local variable |
| projectNumber | uid, name |
| updateTime | sourceLastModified |
| version | currentVersion |
Google Security Center Repository
Table 9: Google Security Center Repository attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ancestors | Local variable |
| assetType | categories |
| createTime | firstSeen |
| data.name | Local variable (Project Name) |
| labels | tags |
| lifecycleState | status |
| parent.id | Local variable |
| parent.type | Local variable |
| projectId | Local variable |
| projectNumber | uid, name |
| updateTime | sourceLastModified |
| version | currentVersion |
Google Security Center Service Account
Table 10: Google Security Center Service Account attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ancestors | Local variable |
| asset_type | categories |
| clientID | Local variable |
| description | description |
| disabled | Local variable |
| displayName | Local variable |
| Local variable | |
| etag | tags, Local variable |
| id / name | uid |
| name | name |
| projectId | Local variable |
| uniqueId | Local variable |
| update_time | sourceLastModified |
| version | currentVersion |
Google Security Center SQL Instance
Table 11: Google Security Center SQL Instance attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ancestors | Local variable |
| backendType | Local variable |
| connectionName | Local variable |
| createTime | firstSeen |
| databaseInstalledVersion | Local variable |
| databaseVersion | Local variable |
| dnsNames.connectionType | Local variable |
| dnsNames.dnsScope | Local variable |
| dnsNames.name | dnsNames, publicDnsName, privateDnsName |
| gceZone | Local variable |
| id / name | uid |
| includeReplicasForMajorVersionUpgrade | Local variable |
| instanceType | Local variable |
| ipAddresses.ipAddress | ipAddresses, privateIpAddresses, publicIpAddresses |
| ipAddresses.type | Local variable |
| maintenanceVersion | Local variable |
| project | Local variable |
| region | Local variable |
| resource.name | name, Local variable |
| satisfiesPzi | Local variable |
| selfLink | url |
| serverCaCert.certSerialNumber | Local variable |
| serverCaCert.commonName | Local variable |
| serverCaCert.createTime | Local variable |
| serverCaCert.expirationTime | Local variable |
| serverCaCert.instance | Local variable |
| serverCaCert.sha1Fingerprint | Local variable |
| serviceAccountEmailAddress | emails |
| settings.activationPolicy | Local variable |
| settings.availabilityType | Local variable |
| settings.backupConfiguration.backupRetentionSettings.retainedBackups | Local variable |
| settings.backupConfiguration.backupRetentionSettings.retentionUnit | Local variable |
| settings.backupConfiguration.backupTier | Local variable |
| settings.backupConfiguration.binaryLogEnabled | Local variable |
| settings.backupConfiguration.enabled | Local variable |
| settings.backupConfiguration.location | Local variable |
| settings.backupConfiguration.startTime | Local variable |
| settings.backupConfiguration.transactionLogRetentionDays | Local variable |
| settings.backupConfiguration.transactionalLogStorageState | Local variable |
| settings.connectorEnforcement | Local variable |
| settings.dataDiskSizeGb | Local variable |
| settings.dataDiskType | Local variable |
| settings.deletionProtectionEnabled | Local variable |
| settings.edition | Local variable |
| settings.finalBackupConfig.enabled | Local variable |
| settings.finalBackupConfig.retentionDays | Local variable |
| settings.ipConfiguration.ipv4Enabled | Local variable |
| settings.ipConfiguration.requireSsl | Local variable |
| settings.ipConfiguration.serverCaMode | Local variable |
| settings.ipConfiguration.sslMode | Local variable |
| settings.locationPreference.zone | Local variable |
| settings.maintenanceWindow.day | Local variable |
| settings.maintenanceWindow.hour | Local variable |
| settings.maintenanceWindow.updateTrack | Local variable |
| settings.pricingPlan | Local variable |
| settings.replicationLagMaxSeconds | Local variable |
| settings.replicationType | Local variable |
| settings.retainBackupsOnDelete | Local variable |
| settings.settingsVersion | Local variable |
| settings.storageAutoResize | Local variable |
| settings.storageAutoResizeLimit | Local variable |
| settings.tier | Local variable |
| sqlNetworkArchitecture | Local variable |
| state | status, sourceStatus |
| update_time | sourceLastModified |
| version | currentVersion |
Google Security Center Violation
Table 12: Google Security Center Violation attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| createTime | sourceCreatedDate |
| eventTime | Local variable |
| getResourceName | targets, Local variable |
| name | uid |
| SourceProperties.ActivationTrigger | Local variable |
| SourceProperties.ProjectId | projects |
| SourceProperties.ResourcePath | path |
| State | status, sourceStatus, statusCategory |
Google Security Center Violation Definition
Table 13: Google Security Center Violation Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | uid, name |
| findingClass | Local variable |
| severity | severity, sourceSeverity, severityScore |
| SourceProperties.ExceptionInstructions | Local variable |
| SourceProperties.Explanation | description |
| SourceProperties.Recommendation | recommendation |
| SourceProperties.ScannerName | Local variable |
Google Security Center Vulnerability
Table 14: Google Security Center Vulnerability attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| createTime | sourceCreatedDate |
| cve.id | type, cveIds, cveRecords |
| eventTime | Local variable |
| getResourceName | targets, Local variable |
| name | uid |
| security_bulletin.bulletin_id | type |
| SourceProperties.ActivationTrigger | Local variable |
| SourceProperties.ProjectId | projects |
| SourceProperties.ResourcePath | path |
| State | status, sourceStatus, statusCategory |
| vulnerability.fixed_package | results |
| vulnerability.offending_package | results |
Google Security Center Vulnerability Definition
Table 15: Google Security Center Vulnerability Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| category | categories |
| cve.cvssv3.attack_vector | cvssV3Av |
| cve.cvssv3.base_score | cvssV3BaseScore |
| cve.cvssv3.confidentiality_impact | cvssV3Ci |
| cve.cvssv3.integrity_impact | cvssV3Ii |
| cve.id | uid, name, cveIds, cveRecords |
| cve.references.uri | references |
| cve.upstream_fix_available | fixable |
| description | recommendation |
| findingClass | Local variable |
| security_bulletin.bulletin_id | uid, name |
| severity | severity, sourceSeverity, severityScore |
| SourceProperties.Description | description |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Operation options
The Google Security Command Center connector supports the following operation options. See connector operation options for information about how to apply them.
Table 16: Security Command Center connector operation options
| Connector Object | Option | All Possible values | Description | Example |
|---|---|---|---|---|
| Alert, Alert Definition, Violation, Violation Definition, Vulnerability, Vulnerability Definition | asset_type | ComputeInstance, Bucket, Firewall, GKECluster, Project, ServiceAccount | A comma-separated list of asset types. You can use this option to limit retrieved findings by asset type, as determined by Google. | Key: asset_type Value: ComputeInstance,Project. This key and value combination only retrieves findings associated with Compute Instances and Projects. |
| findingClass | FINDING_CLASS_UNSPECIFIED, MISCONFIGURATION, OBSERVATION, SCC_ERROR, THREAT, VULNERABILITY | A comma-separated list of finding classes or categories. Retrieve findings based on the specified class, as determined by Google. | Key: findingClass Value: SCC_ERROR,THREAT. This key and value combination only retrieves findings that are classified as SCC errors or threats. | |
| severity | Unspecified, Low, Medium, High, Critical | A comma-separated list of finding severities. Retrieve findings based on the specified severity, as determined by Google. | Key: severity Value: High,Critical. This key and value combination only retrieves high and critical findings. | |
| state | ACTIVE, INACTIVE | Retrieves findings based on their state, as defined by Google. By default, the connector retrieves only ACTIVE findings. To retrieve both active and inactive findings, use state: ACTIVE,INACTIVE. | Key: state Value: ACTIVE,INACTIVE. This key and value combination retrieves both active and inactive findings. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The Google Security Command Center connector uses the Cloud Asset Inventory client libraries and Security Command Center API to interact with Google Security Command Center. Specifically, it uses the following client libraries:
Google Security Center Alert
SecurityCenterClient client = SecurityCenterClient.create();
ListFindingsRequest.Builder request =
ListFindingsRequest.newBuilder().setParent(sourceName.toString()).setFilter(filter);
// Call the API.
ListFindingsPagedResponse response = client.listFindings(request.build());
Google Security Center Alert Definition
SecurityCenterClient client = SecurityCenterClient.create();
ListFindingsRequest.Builder request =
ListFindingsRequest.newBuilder().setParent(sourceName.toString()).setFilter(filter);
// Call the API.
ListFindingsPagedResponse response = client.listFindings(request.build());
Google Security Center Bucket
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// Add asset type "storage.googleapis.com/Bucket" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center Compute Instance
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// Add asset type "compute.googleapis.com/Instance" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center Firewall
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// Add asset type "compute.googleapis.com/Firewall" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center GKE Cluster
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// add asset type "container.googleapis.com/Cluster" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center Project
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// add asset type "cloudresourcemanager.googleapis.com/Project" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center Repository
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// add asset type "container.googleapis.com/Cluster" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center Service Account
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// add asset type "iam.googleapis.com/ServiceAccount" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center SQL Instance
AssetServiceClient client = createAssetServiceClient();
ListAssetsRequest.Builder bld = ListAssetsRequest.newBuilder()
.setParent(scope)
.setPageSize(pageSize)
.setContentType(ContentType.RESOURCE)
.addAssetTypes(assetType);
// add asset type "container.googleapis.com/Cluster" to filter
// Call listAssets API with assetType filter
ListAssetsPagedResponse response = client.listAssets(bld.build());
Google Security Center Violation
SecurityCenterClient client = SecurityCenterClient.create();
ListFindingsRequest.Builder request =
ListFindingsRequest.newBuilder().setParent(sourceName.toString()).setFilter(filter);
// Call the listFindings API.
ListFindingsPagedResponse response = client.listFindings(request.build());
Google Security Center Violation Definition
SecurityCenterClient client = SecurityCenterClient.create();
GroupFindingsRequest.Builder bld =
GroupFindingsRequest.newBuilder().setParent(sourceName.toString()).setGroupBy("category").setPageSize(1000);
// Call the GroupFinding API.
GroupFindingsPagedResponse response = client.groupFindings(bld.build());
// Categories are listed from GroupFindingsPagedResponse.
// Then set category as filter on listFindings API
ListFindingsPagedResponse response = client.listFindings(request.build());
Google Security Center Vulnerability
SecurityCenterClient client = SecurityCenterClient.create();
ListFindingsRequest.Builder request =
ListFindingsRequest.newBuilder().setParent(sourceName.toString()).setFilter(filter);
// Call the API.
ListFindingsPagedResponse response = client.listFindings(request.build());
Google Security Center Vulnerability Definition
SecurityCenterClient client = SecurityCenterClient.create();
ListFindingsRequest.Builder request =
ListFindingsRequest.newBuilder().setParent(sourceName.toString()).setFilter(filter);
// Call the API.
ListFindingsPagedResponse response = client.listFindings(request.build());
Changelog
The Google Security Command Center connector has undergone the following changes:
Table 17: Security Command Center connector changelog
This connector is part of a bundled release with other connectors from the same vendor. If a version shows "No change", it means that the connector version was updated for consistency as part of the bundle, but no functional changes were made to this specific connector. You can update to or skip this version without affecting your existing configuration.
| Version | Description | Date Published |
|---|---|---|
| 3.2.10 | Added the RESULTS attribute to the Vulnerability object, populated from the affected and fixed package details. | February 13th, 2026 |
| 3.2.9 | Added the KUBERNETES_OBJECTS attribute to the Vulnerability, Alert, and Violation objects. | January 29th, 2026 |
| 3.2.8 | Added logic to match assets by the parent project when the same firewall or any asset name exists in two different projects and when the asset cannot be retrieved directly by its uid. | December 26th, 2025 |
| 3.2.7 | - In the Compute Instance object, mapped natIP to PUBLIC_IP_ADDRESSES and networkIP to PRIVATE_IP_ADDRESSES. - The connector now retrieves the SQL Instance object from Google Cloud. - Moved the mapping of RECOMMENDATION attribute from Violation Definition to Violation object. | October 30th, 2025 |
| 3.2.6 | Fixed an issue where the severity level of findings from Google Security Command Center were not accurately reflected in Brinqa. | September 9th, 2025 |
| 3.2.5 | The Security Command Center connector has been renamed to "Google Security Command Center" and the connector icon has been updated. This change only affects the connector label and icon, it does not impact functionality. You can update without making any changes to your existing configurations. | August 5th, 2025 |
| 3.2.4 | - The connector now retrieves the Repository object from Google Cloud. - Fixed an issue where the TARGETS values on the Alert, Violation, and Vulnerability objects were populated with asset names instead of unique identifiers, which prevented proper consolidation with asset records. - Fixed an issue where the Vulnerability Definition object sync was not retrieving any data. - Added a new operation option on all Finding-related objects (Alert, Alert Definition, Violation, Violation Definition, Vulnerability, and Vulnerability Definition) to filter records by asset type: asset_type. | July 2nd, 2025 |
| 3.2.3 | No change. | June 4th, 2025 |
| 3.2.2 | - Changed the ENABLE_DISPLAY attribute type on the Compute Instance object from boolean to string to resolve a data type mismatch error. - Fixed an issue where CVE details were incorrectly mapped to the Vulnerability object. These values are now mapped to the Vulnerability Definition object. | June 4th, 2025 |
| 3.2.1 | - The connector now retrieves the following objects from Google: Google Security Center Alert, Google Security Center Alert Definition, Google Security Center GKE Cluster, Google Security Center Project, Google Security Center Service Account, Google Security Center Vulnerability, and Google Security Center Vulnerability Definition. - Renamed the Finding and Finding Definition objects to Violation and Violation Definition to more accurately reflect the type of misconfiguration and policy violations being ingested. - Findings classified as vulnerabilities now consolidate to the Vulnerability and Vulnerability Definition data models and all other categories consolidate to Violation and Violation Definition. - Added the FINDING_CLASS attribute to Violation and Violation Definition objects. - Added a new operation option for filtering by finding class: findingClass. - Updated the logic to use a more precise UID generation method to prevent duplicates. - Fixed attribute mappings for severity fields, including Severity, Severity Score, and Source Severity. - Added the TAGS attribute to Bucket and Compute Instance objects by combining data from the tags and labels fields. | April 24th, 2025 |
| 3.2.0 | Code cleanup and general maintenance. | April 24th, 2025 |
| 3.1.3 | No change. | December 13th, 2024 |
| 3.1.2.1 | - Fixed an issue where the test connection was failing. - Code cleanup and general maintenance. | December 13th, 2024 |
| 3.1.1 | Added the CVE_IDS and CVE_RECORDS attributes to the Finding object to retrieve CVE information. | October 1st, 2024 |
| 3.1.0 | Initial Integration+ release. | March 12th, 2024 |