GitHub
GitHub is a version control and collaboration platform that allows developers to host their own source code. It provides features such as issue tracking, code review, and integration with various tools and services. You can bring code, dependabot, repository, and scan data from GitHub into Brinqa to enhance your organization's security and risk management capabilities.
This document details the information you must provide for the connector to authenticate with GitHub and how to obtain that information from GitHub. See create a data integration for step-by-step instructions on setting up the integration.
Required connection settings
When setting up a data integration, select GitHub from the Connector drop-down. If you cannot find the connector in the drop-down, make sure that you have installed it first. You must provide the following information to authenticate GitHub with Brinqa:
-
API URL: The GitHub API URL. The default URL is
https://api.github.com. -
App ID: The GitHub App identifier. The app ID is associated with the GitHub App used to access the GitHub API. The app ID is a six-number string such as
123456. -
Private key: The private key associated with the GitHub App, which must have permissions to log in to the API server and return data.
Create a GitHub App
You must register a new GitHub App for the connector to authenticate and access the GitHub API. To create a new GitHub App, follow these steps:
-
Sign in to your GitHub account.
-
Click the profile photo in the upper-right corner of the page, and then click Settings.
- If you want to limit the GitHub connector's access to a specific organization rather than a personal account, click Your organizations in the drop-down instead of Settings. Then, to the right of the organization, click Settings. Follow the same steps outlined below for further configuration.
-
In the navigation menu, select Developer settings.
-
Click GitHub Apps, then New GitHub App, and complete the following fields. The fields not mentioned can be left as is.
-
GitHub App name: The name of your GitHub App.
-
Homepage URL: The full URL to your app's website. For example,
https://www.example.com/github-app.www.example.comrepresents the domain of your company or developer who created the GitHub App, and/github-appis a specific page within your website dedicated to providing information about the app.- If you lack a specific URL and your application's source code is located in a public repository, you may use the repository URL. Alternatively, you can use the URL belonging to the organization or individual who owns the application. For example,
https://github.com/yourusername/your-github-app.yourusernamerepresents the GitHub username of the person or organization who created the app, andyour-github-appis the name of the repository containing the app's source code and documentation.
- If you lack a specific URL and your application's source code is located in a public repository, you may use the repository URL. Alternatively, you can use the URL belonging to the organization or individual who owns the application. For example,
-
Permissions: Add the following permissions required by the connector:
-
Repository:
- Code scanning alerts:
Read-only - Contents:
Read-only - Dependabot alerts:
Read-only - Issues:
Read-only - Metadata:
Read-only - Secret scanning alerts:
Read-only
- Code scanning alerts:
-
Organization: None.
-
Account: None.
-
-
-
Click Create GitHub App.
If the registration is successful, the page reloads and displays information about your new GitHub App. You can find the App ID under the "About" section at the top of the page.
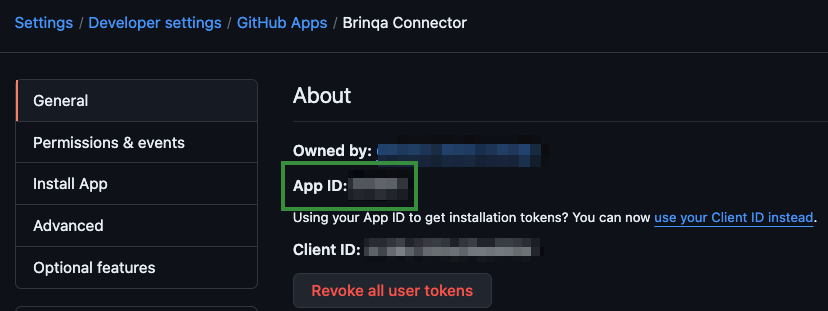
This six-digit string, along with the private key, is required to authenticate the GitHub connector with Brinqa.
If you do not have permissions to create a GitHub App, contact your GitHub administrator. For additional information, see GitHub documentation.
Generate a GitHub private key
Once you've created your GitHub App, you can now generate a private key for authentication. To obtain the private key, follow these steps:
-
While on the same page as your GitHub app information, scroll down to the Private keys section and click Generate a private key.
GitHub generates a new private key and downloads it to your local storage as a
.pemfile. Copy the private key and save the.pemfile in a secure location. -
In the navigation menu, click Install App.
-
Click Install next to the account where you want to install the GitHub App on. You are presented with two options:
-
All repositories: The GitHub App has access to all existing and any future repositories that are owned by the account. This includes public repositories, but the app can only read their contents, not make changes.
-
Only select repositories: Click the "Select repositories" drop-down and select the repositories you want to install the GitHub App to. This also includes read-only public repositories.
-
-
Review the permissions and click Install.
If you do not have permissions to generate a private key or install a GitHub App, contact your GitHub administrator. For additional information, see GitHub documentation about Managing private keys, and Installing your own GitHub App.
Additional settings
The GitHub connector contains additional options for specific configuration:
-
Repository custom properties: A comma-separated list of custom property names used by the Code Repository object on Github. These names are case-insensitive and will be created as attributes in the source data model.
-
Page size: The maximum number of records to get per API request. The default setting is 100. It is not recommended to go over 100.
-
Maximum retries: The maximum number of times that the integration attempts to connect to the GitHub API before giving up and reporting a failure. The default setting is 5.
Types of data to retrieve
The GitHub connector can retrieve the following types of data from the GitHub API:
Table 1: Data retrieved from GitHub
| Connector Object | Required | Maps to Data Model |
|---|---|---|
| Code Scanning Alert | Yes | Static Code Finding |
| Code Scanning Alert Definition | Yes | Static Code Finding Definition |
| Dependabot Alert | Yes | Open Source Finding |
| Dependabot Alert Definition | Yes | Open Source Finding Definition |
| Repository | Yes | Code Repository |
| Secret Scanning Alert | Yes | Static Code Finding |
| Secret Scanning Alert Definition | Yes | Static Code Finding Definition |
For detailed steps on how to view the data retrieved from GitHub in the Brinqa Platform, see How to view your data.
Attribute mappings
Expand the sections below to view the mappings between the source and the Brinqa data model attributes.
Code Scanning Alert
Table 2: Code Scanning Alert attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| alert.createdAt | firstFound |
| alert.dismissedAt | Local variable |
| alert.dismissedBy | Local variable |
| alert.dismissedReason | Local variable |
| alert.fixedAt | lastFixed |
| alert.htmlUrl | Local variable |
| alert.mostRecentInstance.analysisKey | Local variable |
| alert.mostRecentInstance.commitSha | Local variable |
| alert.mostRecentInstance.environment | tags |
| alert.mostRecentInstance.location | path |
| alert.mostRecentInstance.message | results |
| alert.mostRecentInstance.ref | Local variable |
| alert.mostRecentInstance.state | status, sourceStatus, statusCategory |
| alert.number | Local variable |
| alert.repoId | targets |
| alert.repoName | Local variable |
| alert.rule.id | type, uid |
| alert.updatedAt | lastFound, sourceLastModified |
| alert.url | url |
| alertInfo.getAlertUid | uid |
| installation.account.id | Local variable |
| installation.account.login | Local variable |
| alert.tool.guid | Local variable |
| alert.tool.name | Local variable |
| alert.tool.version | Local variable |
Code Scanning Alert Definition
Table 3: Code Scanning Alert Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| alert.rule.description/alert.rule.name | name |
| alert.rule.fullDescription | description |
| alert.rule.help | recommendation |
| alert.rule.securitySeverityLevel | severity, severityScore, sourceSeverity |
| alert.rule.severity | Local variable |
| alert.rule.id | type, uid |
| rule.tags | cweIds, weaknesses, tags |
Dependabot Alert
Table 4: Dependabot Alert attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| ai.getAlertUid | uid |
| alert.createdAt | firstFound |
| alert.dependency.manifestPath | path |
| alert.dependency.scope | Local variable |
| alert.dismissedAt | Local variable |
| alert.dismissedBy | Local variable |
| alert.dismissedReason | Local variable |
| alert.htmlUrl | Local variable |
| alert.number | Local variable |
| alert.repoId | targets |
| alert.repoName | Local variable |
| alert.state | status, sourceStatus, statusCategory |
| alert.updatedAt | lastFound |
| alert.url | url |
| alert.vulnerability | recommendation, results |
| alert.vulnerability._package | Local variable |
| alert.vulnerability.firstPatchedVersion | Local variable |
| alert.vulnerability.vulnerableVersionRange | Local variable |
| installation.account.id | Local variable |
| installation.account.login | Local variable |
Dependabot Alert Definition
Table 5: Dependabot Alert Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| advisory.cvss | Use CVSS calculator |
| advisory.cveId | cveIds, cveRecords |
| advisory.cwes | cweIds, weaknesses |
| advisory.description | description |
| advisory.ghsaId | Local variable |
| advisory.publishedAt | publishedDate |
| advisory.references.url | references |
| advisory.severity | severity, severityScore, sourceSeverity |
| advisory.summary | name |
| advisory.withdrawnAt | Local variable |
| alert.advisory.ghsaId | type, Local variable / uid |
Use CVSS calculator indicates that the CVSS (Common Vulnerability Scoring System) vectors and scores aren't directly mapped to a specific attribute on the UDM. Instead, a specialized library calculates the CVSS scores from the provided CVSS vector strings.
Repository
Table 6: Repository attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| categories | categories |
| installation.account.id | Local variable |
| installation.account.login | Local variable |
| repo._private | Local variable |
| repo.archived | Local variable |
| repo.createdAt | firstSeen, sourceCreatedDate |
| repo.defaultBranch | Local variable |
| repo.description | description |
| repo.disabled | Local variable |
| repo.fork | Local variable |
| repo.forkCount | Local variable |
| repo.hasDiscussions | Local variable |
| repo.hasDownloads | Local variable |
| repo.hasIssues | Local variable |
| repo.hasPages | Local variable |
| repo.hasProjects | Local variable |
| repo.hasWiki | Local variable |
| repo.homepage | Local variable |
| repo.htmlUrl | Local variable |
| repo.isTemplate | Local variable |
| repo.language | languages |
| repo.license | Local variable |
| repo.name | name |
| repo.nodeId | uid |
| repo.openIssuesCount | Local variable |
| repo.owner | owner |
| repo.pushedAt | lastSeen, sourceLastModified, Local variable |
| repo.securityAnalysis.advancedSecurity | Local variable |
| repo.securityAnalysis.dependabotSecurityUpdates | Local variable |
| repo.securityAnalysis.secretScanning | Local variable |
| repo.securityAnalysis.secretScanningNonProviderPatterns | Local variable |
| repo.securityAnalysis.secretScanningPushProtection | Local variable |
| repo.securityAnalysis.secretScanningValidityChecks | Local variable |
| repo.size | Local variable |
| repo.stargazersCount | Local variable |
| repo.topics | Local variable |
| repo.updatedAt | lastSeen, sourceLastModified |
| repo.url | url |
| repo.visibility | Local variable |
| repo.watchersCount | Local variable |
| repo.webCommitSignoffRequired | Local variable |
Secret Scanning Alert
Table 7: Secret Scanning Alert attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| alert.createdAt | firstFound, sourceCreatedDate |
| alert.htmlUrl | Local variable |
| alert.locationsUrl | Local variable |
| alert.number | Local variable |
| alert.pushProtectionBypassed | Local variable |
| alert.pushProtectionBypassedAt | Local variable |
| alert.pushProtectionBypassedBy.login | Local variable |
| alert.repoId | targets |
| alert.repoId, alert.repoName | Local variable |
| alert.repoName | Local variable |
| alert.resolution | Local variable |
| alert.resolutionComment | Local variable |
| alert.resolvedAt | lastFixed |
| alert.resolvedBy.login | Local variable |
| alert.secret | results, Local variable |
| alert.secretType | results, Local variable |
| alert.secretTypeDisplayName | results, Local variable |
| alert.state | status, sourceStatus, statusCategory |
| alert.updatedAt | lastFound, sourceLastModified |
| alert.url | url |
| alert.validity | Local variable |
| installation.account.id | Local variable |
| installation.account.login | Local variable |
| uid | uid |
Secret Scanning Alert Definition
Table 8: Secret Scanning Alert Definition attribute mappings
| Source Field Name | Maps to Attribute |
|---|---|
| description | description |
| name | name |
| recommendation | recommendation |
| type | type, uid, cweIds, weaknesses |
Local variable indicates that the field is processed within a specific context, such as a particular workflow or calculation. Unlike other attributes, local variables aren't mapped to the unified data models. They only exist on the source data model.
Data lifecycle management (DLM) strategy
The following table details the DLM strategy for the GitHub connector:
Table 9: GitHub DLM strategy
| Connector Object | Inactivity Condition | Purge Policy | Summary |
|---|---|---|---|
| Code Scanning Alert | Inactivity is delegated to the Repository object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated repository, and then purges the records after 30 days of inactivity. |
| Dependabot Alert | Inactivity is delegated to the Repository object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated repository, and then purges the records after 30 days of inactivity. |
| Repository | LAST_SEEN NOT IN LAST 180 Days | 30 days after inactivity | Uses the LAST_SEEN attribute to identify code repositories that are inactive within the last 180 days, and then purges the records after 30 days of inactivity. |
| Secret Scanning Alert | Inactivity is delegated to the Repository object | 30 days after inactivity | Inactivity is determined by the lifecycle status of the associated repository, and then purges the records after 30 days of inactivity. |
Operation options
The GitHub connector supports the following operation options. See connector operation options for information about how to apply them.
Table 10: GitHub connector operation options
| Connector Object | Option | All Possible Values | Description | Example |
|---|---|---|---|---|
| Secret Scanning Alert | secret_type | Any GitHub secret scanning alert type | A comma-separated list of secret scanning alert types. You can use this option to filter secret scanning alerts by type. For additional information, see GitHub documentation. | Key: secret_type Value: secret_scanning_sample_token,github_personal_access_token,http_basic_authentication_header. This key and value combination only retrieves secret scanning alerts with the specified types. |
The option keys and values are case-sensitive as they are shown in this documentation.
APIs
The GitHub connector uses the GitHub REST API. Specifically, it uses the following endpoints:
Table 11: GitHub REST API Endpoints
| Connector Object | API Endpoints |
|---|---|
| Code Scanning Alert | GET /orgs/{account_id}/code-scanning/alerts |
| Code Scanning Alert Definition | GET /orgs/{account_id}/code-scanning/alerts |
| Dependabot Alert | GET /orgs/{account_id}/dependabot/alerts |
| Dependabot Alert Definition | GET /orgs/{account_id}/dependabot/alerts |
| Repository | GET /orgs/{account_id}/repos |
| Secret Scanning Alert | GET /orgs/{account_id}/secret-scanning/alerts |
| Secret Scanning Alert Definition | GET /orgs/{account_id}/secret-scanning/alerts |
Changelog
The GitHub connector has undergone the following changes:
Table 12: GitHub connector changelog
| Version | Description |
|---|---|
| 4.0.11 | Replaced the masked value with a hash in the Secret attribute on the Secret Scanning Alert object to support deduplication of alerts across repositories. |
| 4.0.10 | - Added support for Data lifecycle management to the Code Repository, Code Scanning Alert, Dependabot Alert, and Secret Scanning Alert objects. - Added the PROVIDER_STATUS and SOURCE_STATUS attributes to the Code Scanning Alert, Dependabot Alert, and Secret Scanning Alert objects. - Code clean up and general maintenance. |
| 4.0.9 | Fixed an issue where the secret_type operation option for the Secret Scanning Alert object only retrieved the first secret type from a list, instead of correctly handling multiple secret types provided in a comma-separated list. |
| 4.0.8 | Added the LAST_FIXED attribute to the Dependabot Alert object. |
| 4.0.7 | Added a new operation option to filter by Secret Scanning Alert types: secret_type. |
| 4.0.6 | Fixed an issue where the CM_COMPLIANCE attribute on the Code Repository object was not populating correctly. |
| 4.0.5 | Added the following attributes to the Dependabot Alert object:
|
| 4.0.4 | Added the SCOPE attribute to the Dependabot Alert object to help indicate whether a dependency is used at runtime or during development. |
| 4.0.3 | Added the HTML_URL attribute to the Repository object to display the GitHub web link. This provides a clearer reference to the repository location. |
| 4.0.2 | Changed the ADVANCED_SECURITY and DEPENDABOT_SECURITY_UPDATES attribute types on the Code Repository object from string to boolean. |
| 4.0.1 | Added the HTML_URL attribute to the Dependabot Alert object. |
| 4.0.0 | - Transitioned the GitHub connector to fully use the GitHub REST API to enhance performance and reliability. - Renamed the following objects to better align with GitHub terminology:
- Updated the Repository object with new attributes while removing some that are no longer available or relevant in the GitHub REST API. - Enhanced the details and recommendations provided by Code Scanning Alerts to offer more comprehensive information. |
| 3.0.14 | Fixed an issue where the Code Repository sync was returning a 406 error. |
| 3.0.13 | Changed the PUSH_PROTECTION_BYPASSED attribute type on the Secret Scanning Alert object from string to boolean. |
| 3.0.12 |
|
| 3.0.11 | Fixed an issue where the RESULTS attribute on Open Source Finding object was returning as a multi-value attribute. |
| 3.0.10 | Added a new setting for custom properties in the Code Repository object. |
| 3.0.9 | Made the Package object optional. |
| 3.0.8 | Fixed an issue where Code Repository records weren't getting synced. |
| 3.0.7 | Updated dependencies. |
| 3.0.6 | Fixed a data integration failure when attempting to sync Secret Scanning Alert, Static Code Finding, or Static Code Finding Definition objects. |
| 3.0.5 | Added a VALIDITY attribute to the Secret Scanning Alert object. |
| 3.0.4 | Changed the 'AUTO_DISMISSED' status to 'Fixed' in the Open Source Finding and Static Code Finding objects. |
| 3.0.3 | Enhanced to retrieve all statuses of the Open Source Finding object. |
| 3.0.2 | Fixed an issue on the CATEGORIES attribute that caused data integration to fail. |
| 3.0.1 | Removed the use of ImmutableSet. |
| 3.0.0 | Initial Integration+ release. |