Explore CVEs with AI
BrinqaIQ offers a Common Vulnerabilities and Exposures (CVE) explorer mode that enables you to investigate known vulnerabilities, understand their risk, and evaluate their presence within the Brinqa Platform.
For additional information about how BrinqaIQ works, data usage, and safeguards, see the BrinqaIQ Overview.
What is CVE exploration?
CVE Exploration enables you to ask BrinqaIQ about a known vulnerability using a CVE ID (e.g., CVE-2014-0160) or a named vulnerability (e.g., Heartbleed), and receive a summary of its severity, impact, affected products, mitigation steps, and more.
CVE exploration can simplify and accelerate your vulnerability investigation workflow, specifically when responding to newly published CVEs or prioritizing remediation and patching efforts.
Example workflow
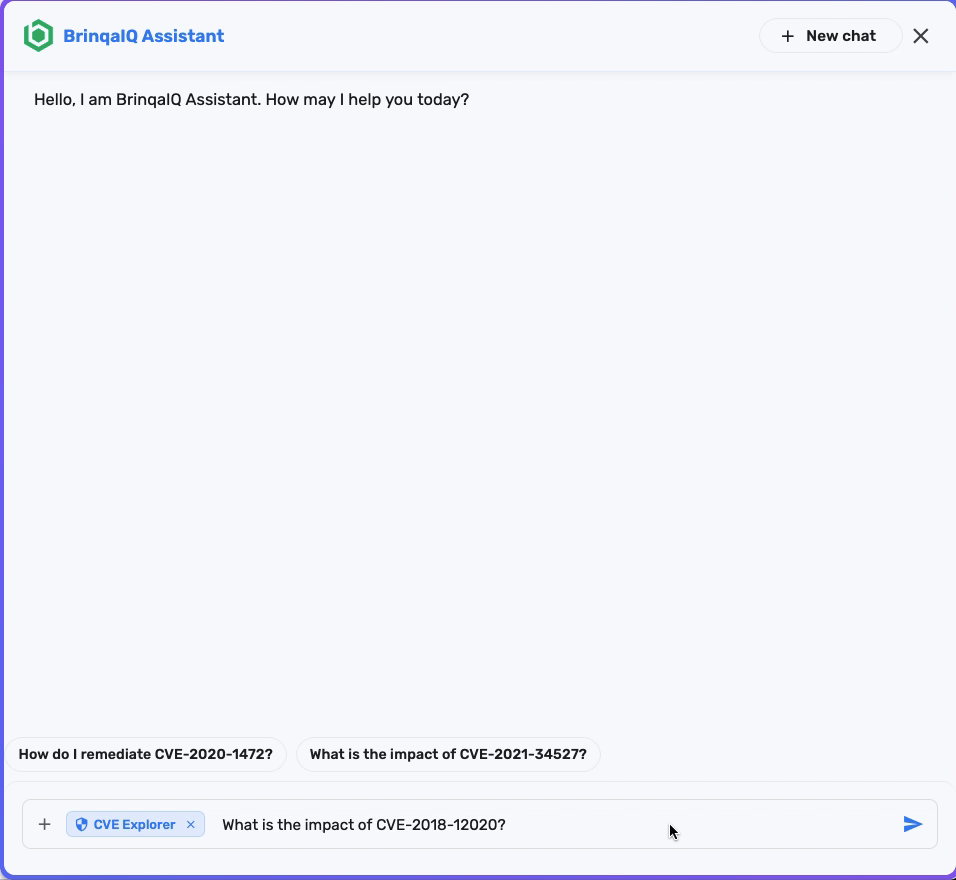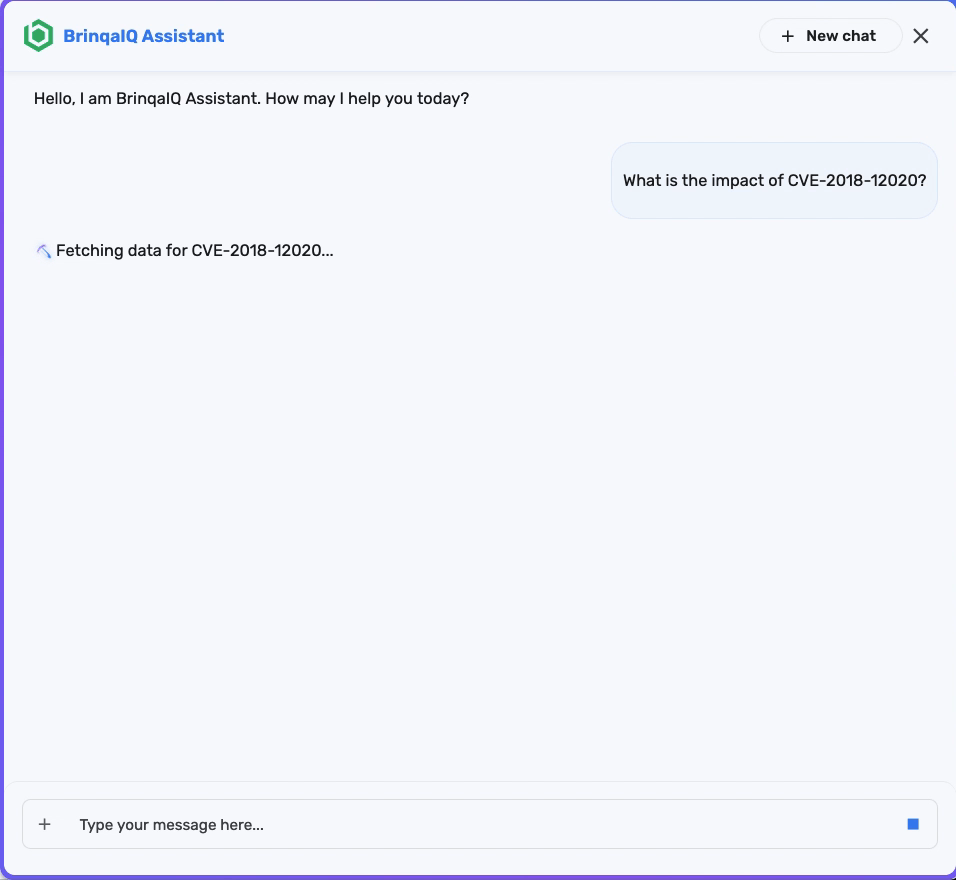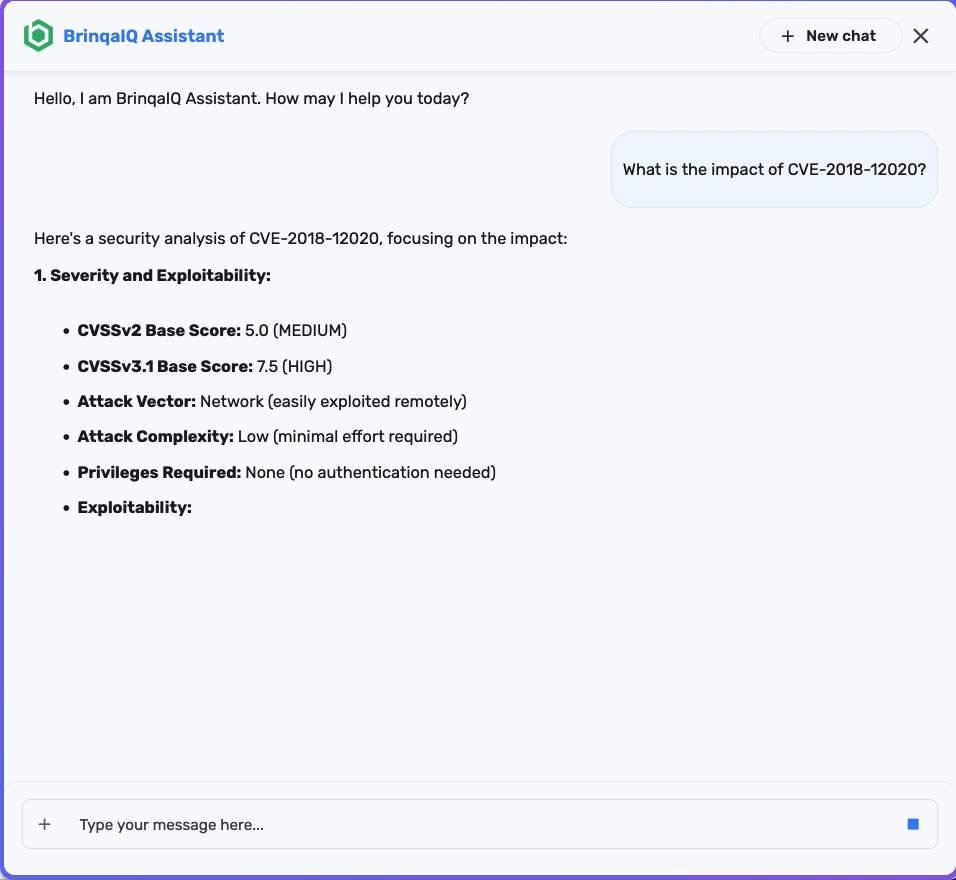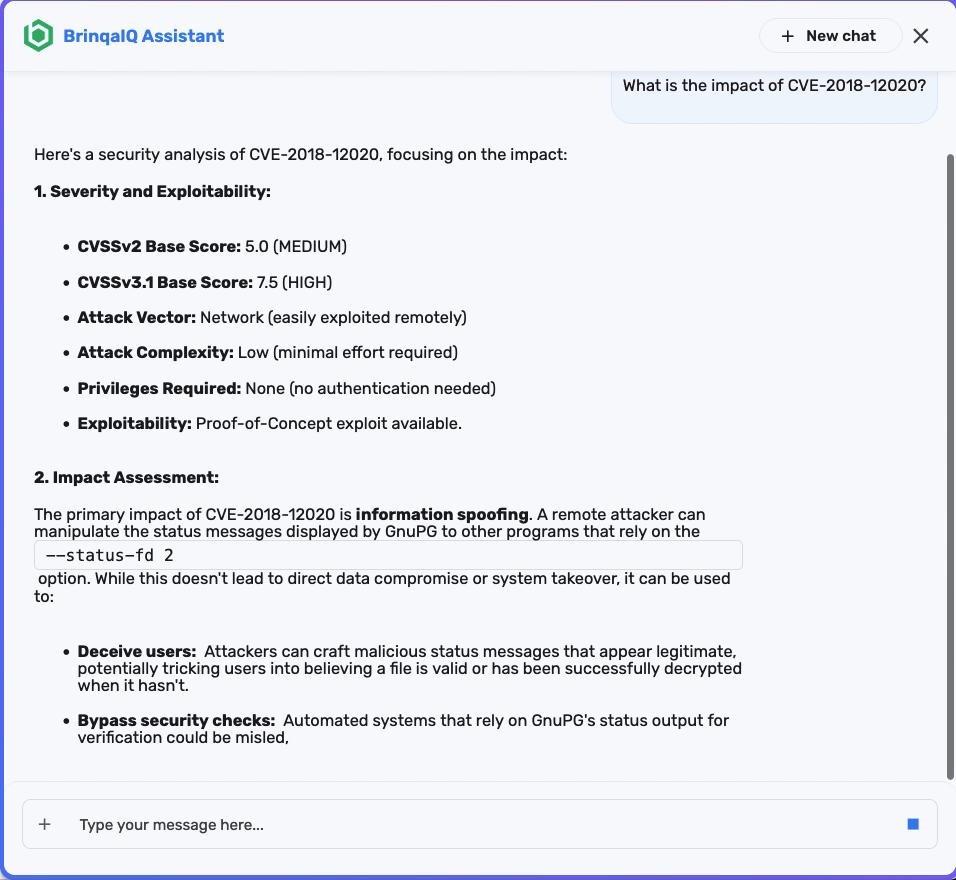
You can start by asking a question such as: "What is the impact of CVE-2018-12020?"
BrinqaIQ responds with a detailed summary that includes severity scores, exploitability details, affected products, mitigation guidance, and links to the CVE in relevant security databases such as the National Vulnerability Database (NVD), CISA Known Exploited Vulnerabilities Catalog (KEV), or other vendor advisory boards.
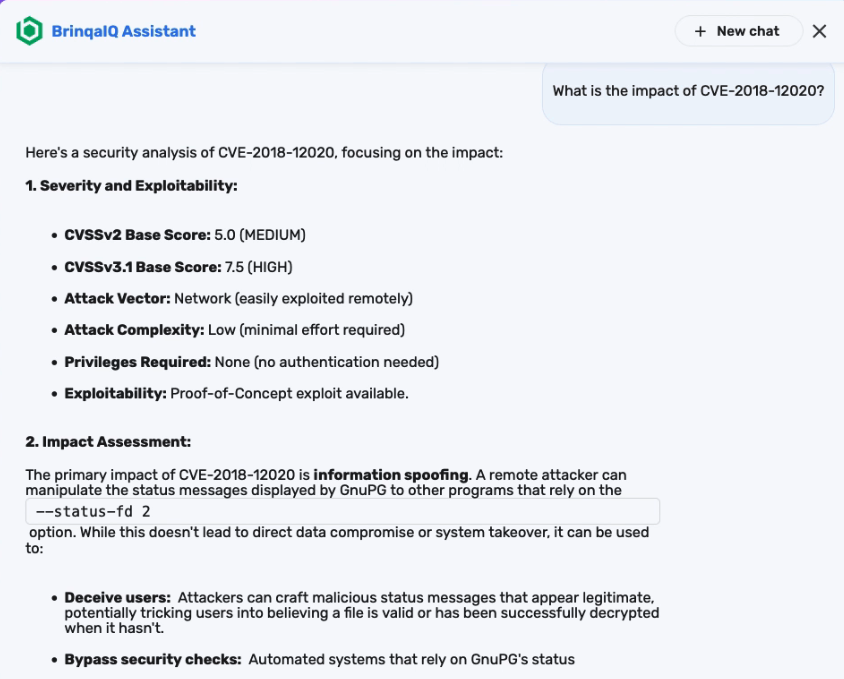
This response provides quick insight into how dangerous the vulnerability is, whether a public exploit exists, and what systems may be affected. You can use this context to prioritize patching, inform stakeholders, or continue investigating the impact within your environment.
You can follow up with questions like: "What findings are impacted by CVE-2018-12020?"
BrinqaIQ returns a BQL query to help you identify where this vulnerability is present in your environment:
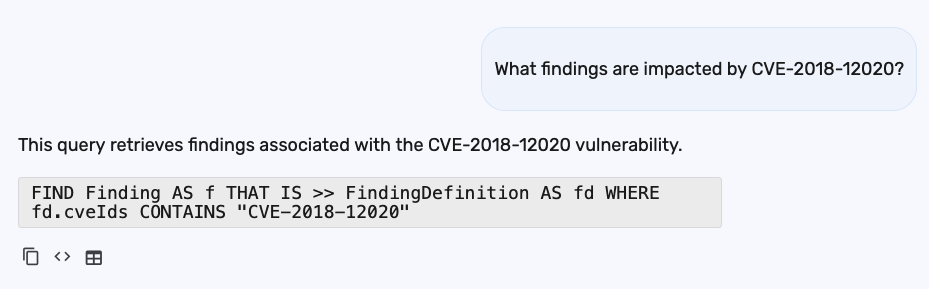
When BrinqaIQ responds with a BQL query, you’ll see three buttons below the response:
-
Copy response to clipboard
: Copies the full chatbot response, including the explanation and the BQL query.
-
Copy code to clipboard
: Copies only the BQL query to your clipboard.
-
Run BQL in Explorer
: Opens the Explorer page and runs the query.
To further narrow the scope, you could ask: "What about the findings impacted by CVE-2018-12020 that are on active assets?"
BrinqaIQ provides a BQL query that identifies your findings related to CVE-2018-12020 that are specifically associated with active assets:
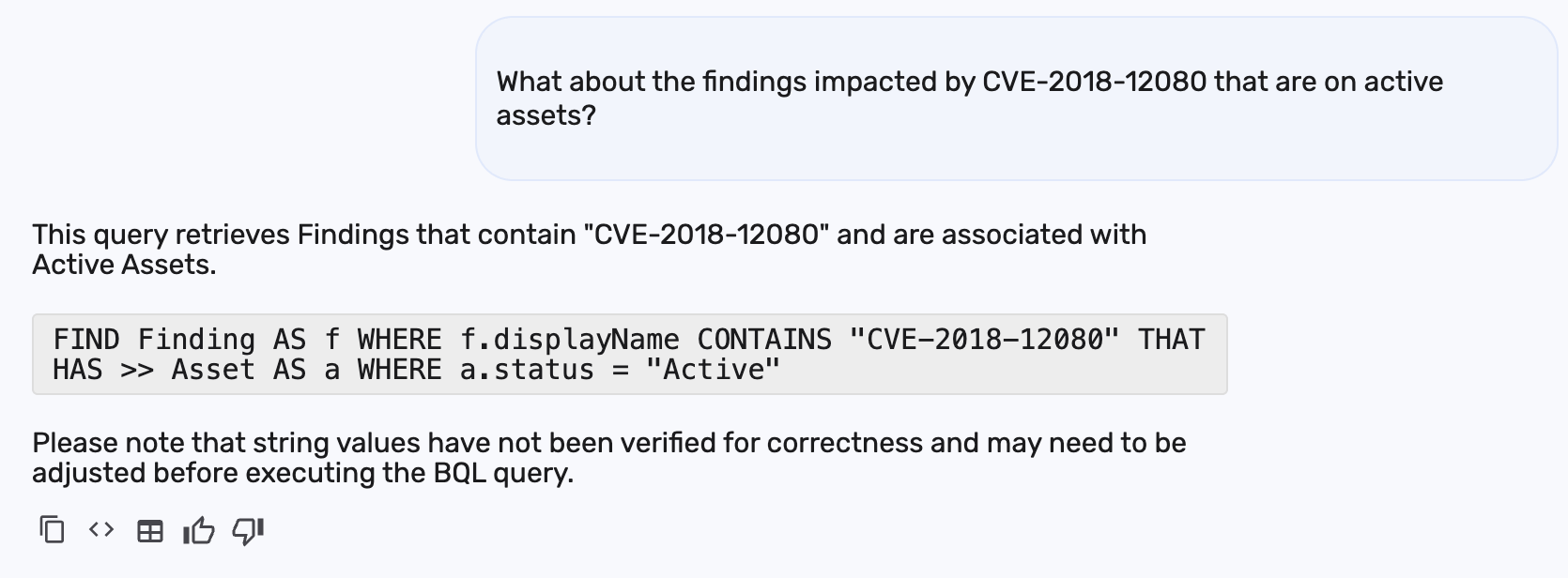
As the result states, string values such as "Active" may need to be verified and adjusted to match your environment’s exact attribute values before executing the query.
By iterating on your questions and prompts, you can move from high-level awareness of a vulnerability to specific actions you can take in the Brinqa Platform.
Example prompts
Here are some examples to help you explore and investigate known CVEs using BrinqaIQ:
-
What is the impact of
CVE-XXXX-YYYY? -
What products are affected by
CVE-XXXX-YYYY? -
How can I remediate
CVE-XXXX-YYYY? -
What operating systems are affected by
CVE-XXXX-YYYY? -
Which findings are impacted by
CVE-XXXX-YYYY?Replace
CVE-XXXX-YYYYwith the CVE ID you want to investigate (e.g.,CVE-2018-12020).