Retrieve Critical Vulnerabilities
This article provides an example demonstrating how to execute a GraphQL query via the Brinqa API to retrieve specific vulnerabilities based on your selected criteria. While this example focuses on a specific set of attributes, you can tailor the query to include the attributes that fit your needs. For more details on the GraphQL explorer, see how to use the GraphQL explorer.
To query for active and critical vulnerabilities in the GraphQL Explorer, follow these steps:
-
Log in to your Brinqa Platform as a System Administrator.
-
Navigate to Administration
> System > GraphQL Explorer.
-
Click
Show GraphQL Explorer to display or switch to the GraphQL Explorer.
-
Click vulnerabilities to display the options and fields for vulnerabilities.
-
To specify a filter, select the filter option and provide a condition such as
status=activeandriskRating=Critical. -
To specify the number of records to be returned, select the limit option and type a number. The default number is 10.
-
To include specific fields in your query, select them from the available fields. For example, you can select ageInDays, complianceStatus, connectorNames, description, id, and riskScore. If needed, click the field again to remove it from the query.
-
To include Common Vulnerabilities and Exposures (CVE) IDs in your query, click type, and then select cveIds, name, and recommendation.
For a brief description of each field, refer to the Docs menu within the GraphQL Explorer. You can use the search function to find specific attributes, or browse the list to get a brief description of each field.
- After you've selected all the desired fields, click Execute query or press Ctrl-Enter to run the query.
The right pane displays the results. You can modify the query by changing the filter conditions and the limit, or by selecting different fields to include in the response.
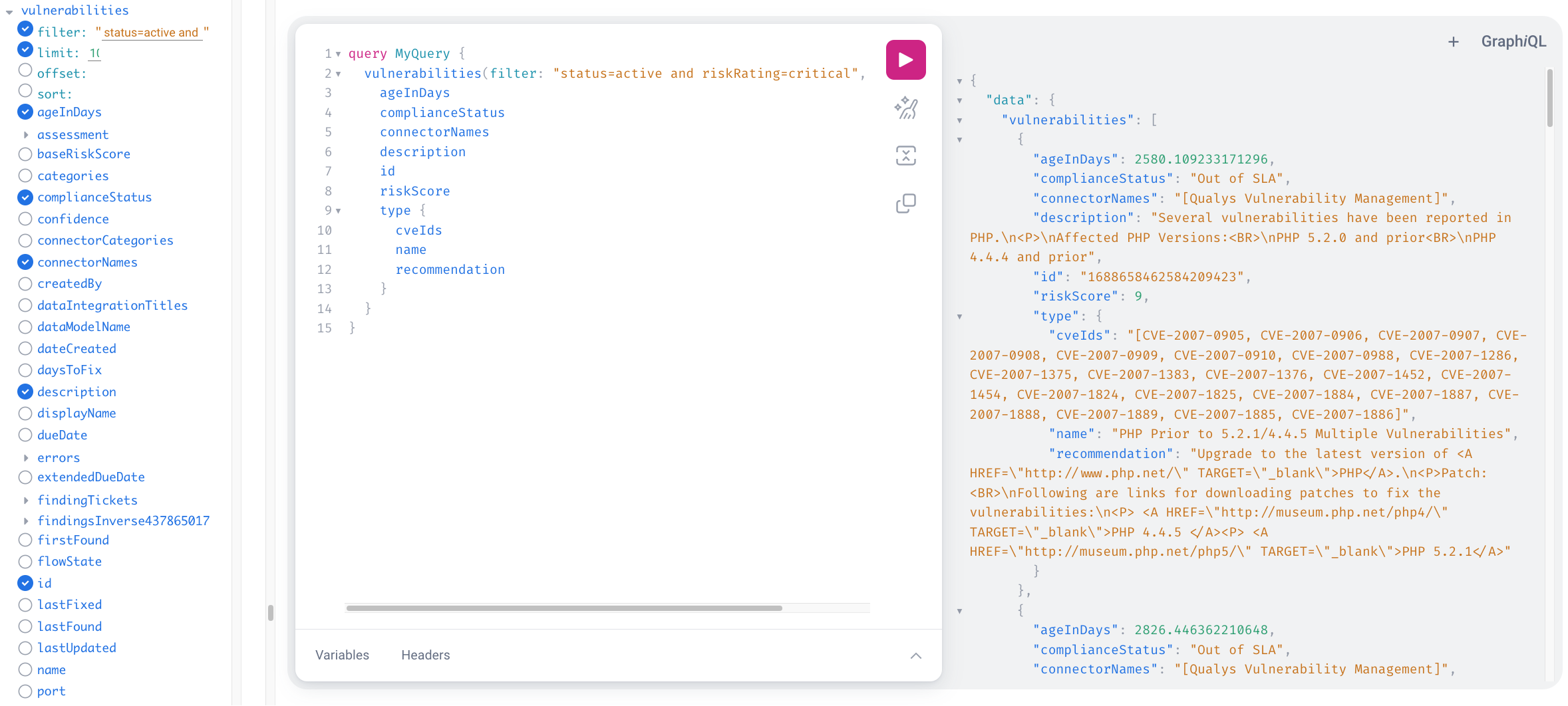
After you've verified that the query is fetching the desired data, you can either copy the query itself or click Show GraphQL Code Exporter to obtain the cURL command.
Here's the cURL command corresponding to the query in the screenshot. It sends a POST request to the Brinqa GraphQL endpoint with specific headers, such as Content-Type and Authorization, to ensure proper handling of the JSON content and authentication:
curl 'https://<BrinqaPlatformName>.brinqa.net/graphql/caasm' \
--compressed \
-X POST \
-H "Content-Type: application/json" \
-H "Authorization: Bearer <your-access-token>" \
-H "Accept: application/json" \
-H "Accept-Encoding: gzip, deflate" \
--data '{
"query": "query MyQuery { vulnerabilities(filter: "status=active and riskRating=critical", limit: 10) { ageInDays complianceStatus connectorNames description id riskScore type { cveIds name recommendation } }}",
"variables": null,
"operationName": "MyQuery"
}'
Replace <BrinqaPlatformName> with the actual name of your Brinqa Platform and replace <your-access-token> with your access token.
The result of this query is a JSON object containing an array of vulnerabilities. Each vulnerability item consists of the fields you have selected in your query. The provided result is a snapshot of the vulnerabilities that meet the criteria specified in the query:
{
"data": {
"vulnerabilities": [
{
"ageInDays": 2580.109233171296,
"complianceStatus": "Out of SLA",
"connectorNames": "[Qualys Vulnerability Management]",
"description": "Several vulnerabilities have been reported in PHP. ...",
"id": "1688658462584209423",
"riskScore": 9,
"type": {
"cveIds": "[CVE-2007-0905, CVE-2007-0906, ...]",
"name": "PHP Prior to 5.2.1/4.4.5 Multiple Vulnerabilities",
"recommendation": "Upgrade to the latest version of PHP. ..."
}
},
{
"ageInDays": 2826.446362210648,
"complianceStatus": "Out of SLA",
"connectorNames": "[Qualys Vulnerability Management]",
"description": "The rpc.statd program, ...",
"id": "1688658462600986646",
"riskScore": 9,
"type": {
"cveIds": "[CVE-2000-0666, CVE-2000-0800]",
"name": "Statd Format Bug Vulnerability",
"recommendation": "For Red Hat Linux: ... For other distributions: ..."
}
},
{
// ... other vulnerabilities ...
}
]
}
}